Preface: For example, if an integer data type allows integers up to two bytes or 16 bits in length (or an unsigned number up to decimal 65,535), and two integers are to be added together that will exceed the value of 65,535, the result will be integer overflow.
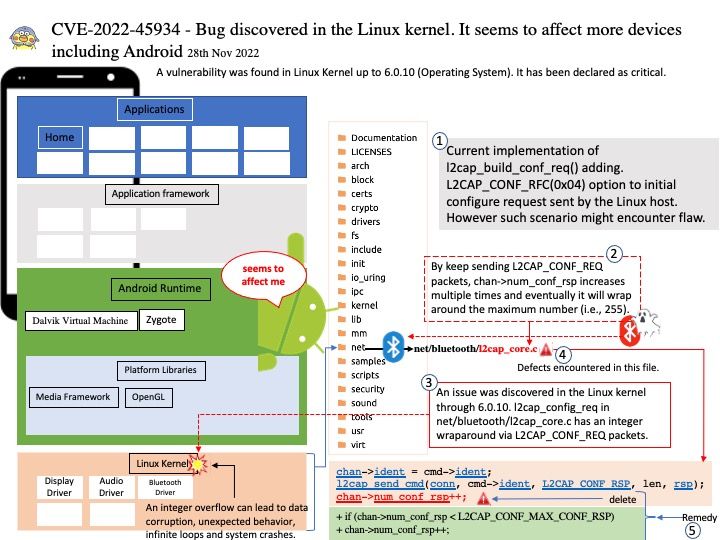
Background: L2CAP is used within the Bluetooth protocol stack. It passes packets to either the Host Controller Interface (HCI) or, on a hostless system, directly to the Link Manager/ACL link. L2CAP’s functions include: Multiplexing data between different higher layer protocols.In order to provide several data streams, L2CAP uses channels, which are represented by the l2cap_cha structure (include/net/bluetooth/l2cap.h). Current implementation of l2cap_build_conf_req() adding. L2CAP_CONF_RFC(0x04) option to initial configure request sent by the Linux host.
Vulnerability details: A vulnerability was found in Linux Kernel up to 6.0.10 (Operating System). It has been declared as critical. An issue was discovered in the Linux kernel through 6.0.10. l2cap_config_req in net/bluetooth/l2cap_core.c has an integer wraparound via L2CAP_CONF_REQ packets.
Solution: Applying a patch should eliminate this problem.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2022-45934