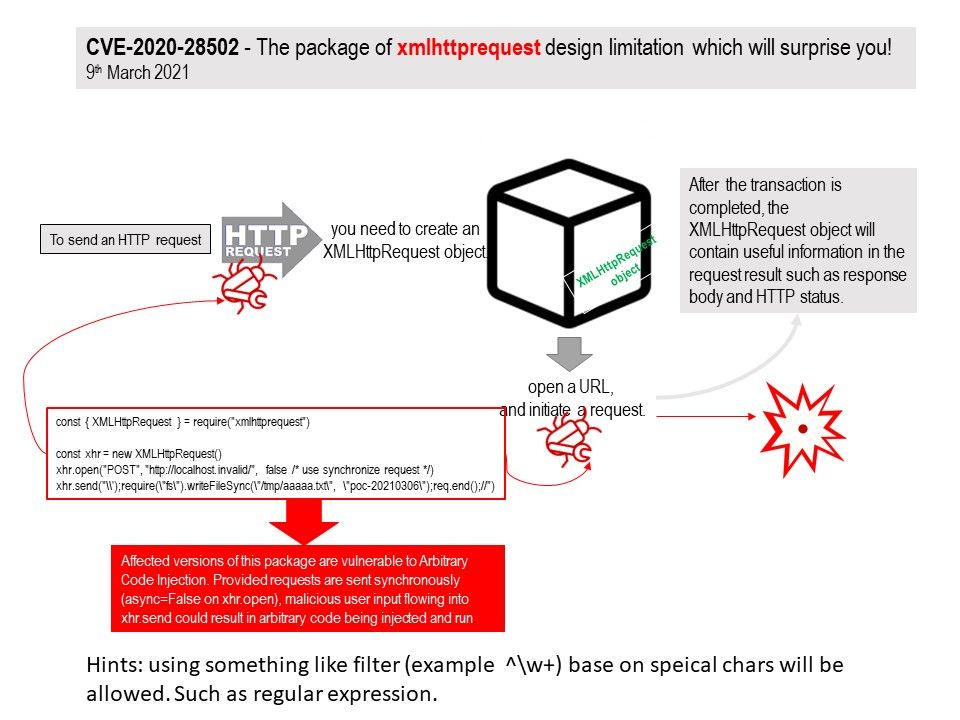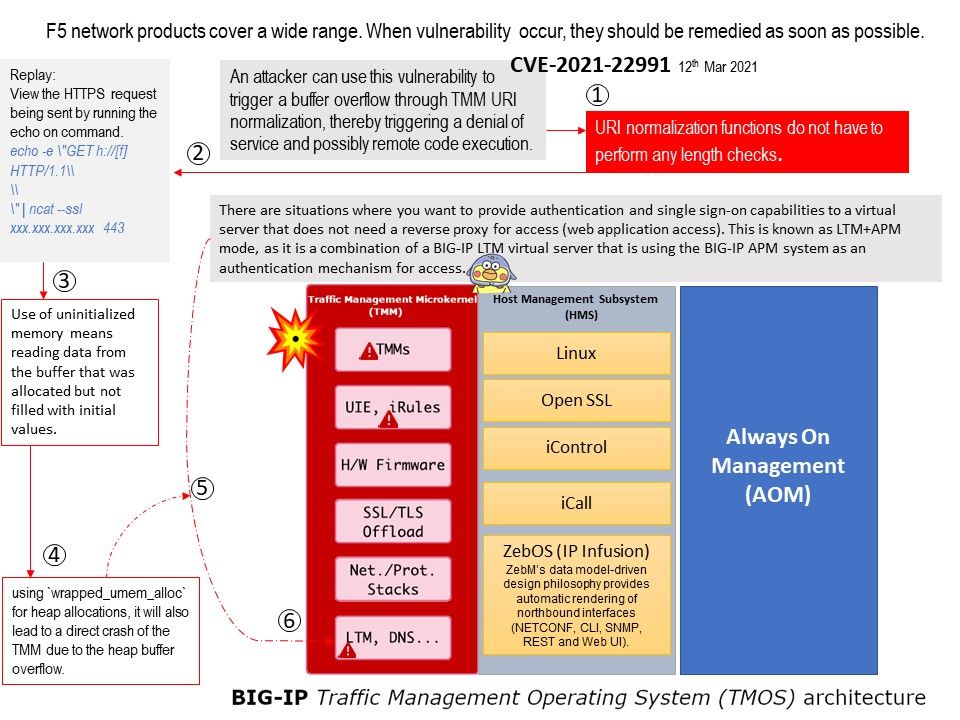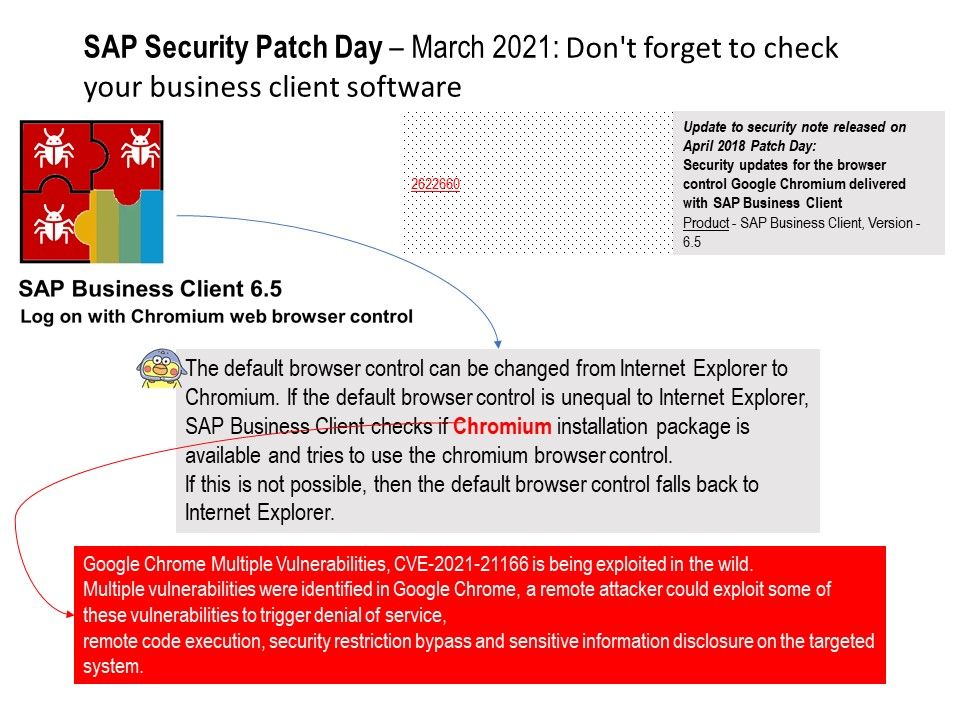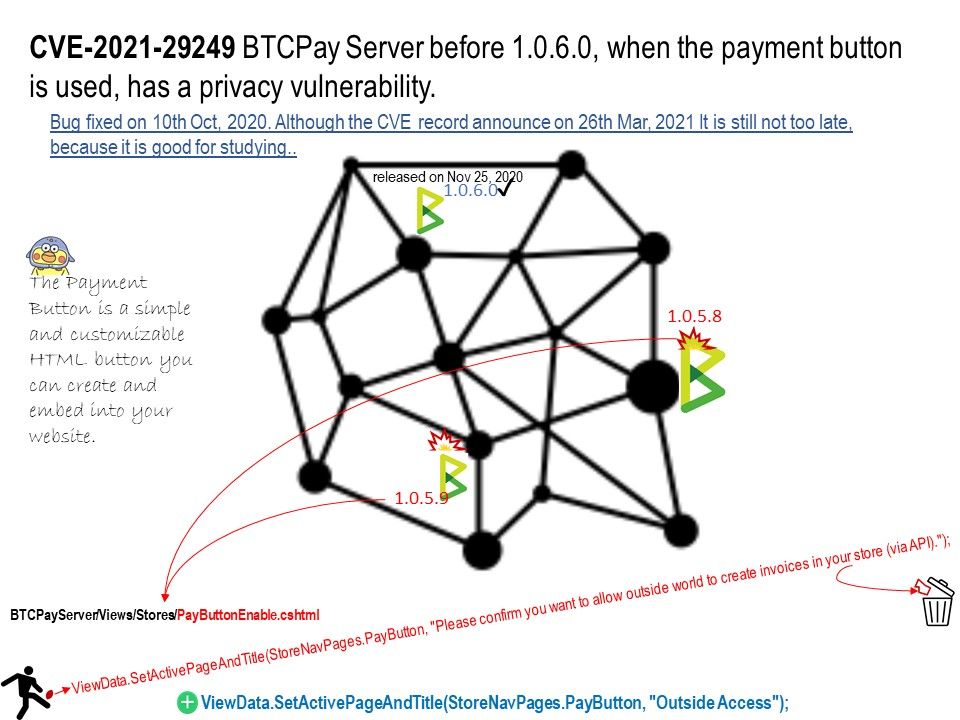
Preface: From a investment market perspective, blockchain might become next-generation investment tool. So called investment will contain risk. For instance, Hedge Fund and currencies buy and sell on markets are risky. This atmosphere we are living in long time. So no feeling any special.
BTCPay server background:
– MIT License.
– Anyone can deploy a server. Become a self-hosted payment processor and receive payments directly to your wallet.
– Your private key is never required. Non-custodial. BTCPay only needs xpubkey (public key) to generate invoices.
– Code is open-source and can be inspected by security auditors and developers.
Vulnerability details: The data is shared only between two parties – the buyer and a seller. However, due to a vulnerability, it may allow outsiders (via API) to create invoices in your store. So it is possible for people to read the data in your store.
Impact: BTCPay Server before 1.0.6.0 when the payment button is used, has vulnerability occurred.
Remedy: Due to a vulnerability occur, users of the payment button are strongly encouraged to update to 1.0.6.0 as soon as possible.
.jpg?width=1920&height=1080&fit=bounds)