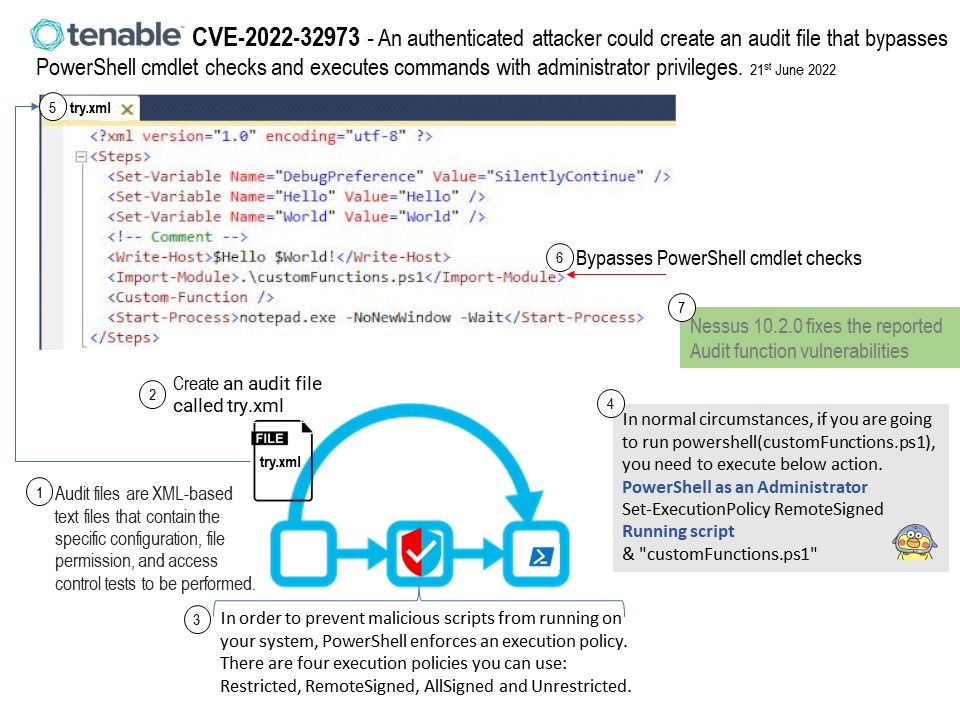
Preface: In order to prevent malicious scripts from running on your system, PowerShell enforces an execution policy. There are four execution policies you can use: Restricted, RemoteSigned, AllSigned and Unrestricted.
Background: The Nessus vulnerability scanner allows you to perform compliance audits of numerous platforms including (but not limited to) databases, Cisco, Unix, and Windows configurations as well as sensitive data discovery based on regex contained in audit files. Audit files are XML-based text files that contain the specific configuration, file permission, and access control tests to be performed.
After you create an audit file, you can reference the audit file in a template-based Policy Compliance Auditing scan policy or a custom scan policy, said Tenable.
Vulnerability details: An authenticated attacker could create an audit file that bypasses PowerShell cmdlet checks and executes commands with administrator privileges.
Ref: In normal circumstances, if you are going to run powershell(xxx.ps1), you need to execute below action.
- PowerShell as an Administrator
- Set-ExecutionPolicy RemoteSigned
- Running script (see below)
& “xxx.ps1”
Official announcement: Tenable has opted to upgrade these components to address the potential impact of the issues. Nessus 10.2.0 fixes the reported Audit function vulnerabilities. For more details, please refer to link – https://www.tenable.com/security/tns-2022-11