Preface: If management functions follow best practices, keep them running on separate network segments. Among other things, it limits the management console to a small number of workstations. Even if the product has vulnerabilities. Risk may be significantly reduced.
Background: TERNUS CS8000 is a datacenter solution for backup storage for mainframe and open systems. Using intelligent process automation and the pooling of storage capacities, backup data is automatically managed between different storage tiers, including disk, deduplication and tape technology.
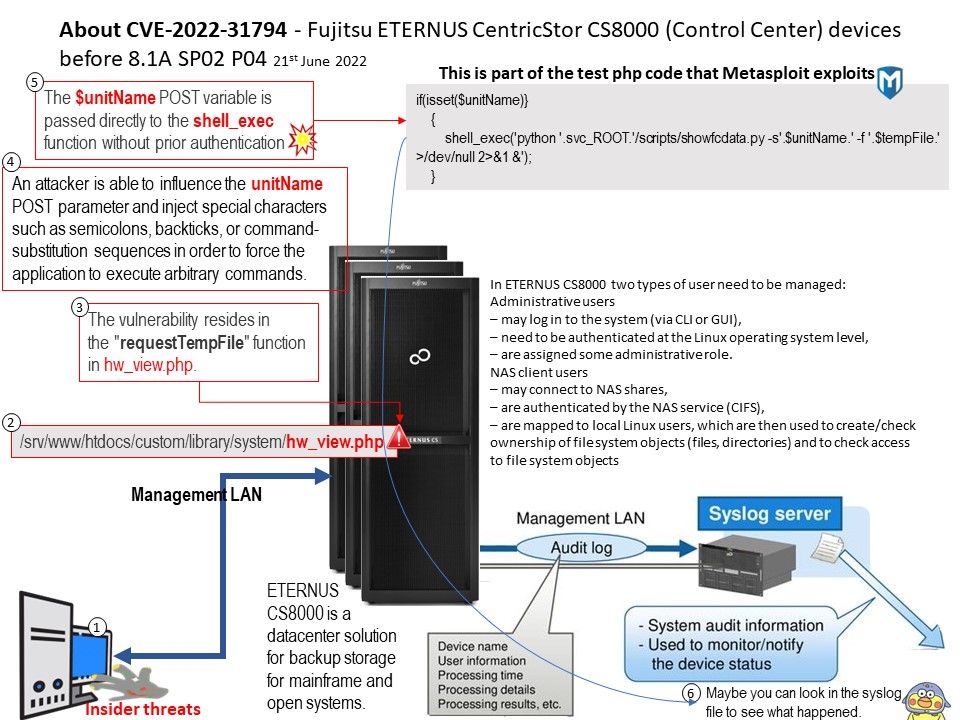
The console GUI provides a complete graphical representation of an ETERNUS CS8000 system, and covers all connected devices and ISPs(Integrated Service Processor) such as ICPs(integrated channel processor), IDPs (integrated device processor) and VLPs (virtual library processor).
Vulnerability details: An issue was discovered on Fujitsu ETERNUS CentricStor CS8000 (Control Center) devices before 8.1A SP02 P04. The vulnerability resides in the requestTempFile function in hw_view.php. An attacker is able to influence the unitName POST parameter and inject special characters such as semicolons, backticks, or command-substitution sequences in order to force the application to execute arbitrary commands. The vulnerability resides in the “requestTempFile” function in hw_view[.]php.
Solution: Applying the patch 8.1A SP02 P04 is able to eliminate this problem.
Typically, a data center already has a SIEM installed. A SIEM might have no trouble tracking down similar cyber attacks.
In order to correctly define the triggering rules. You can refer to NCCGroup technical papers as a reference. Please refer to the link for details – https://research.nccgroup.com/2022/05/27/technical-advisory-fujitsu-centricstor-control-center-v8-1-unauthenticated-command-injection/