21st June 2022
Preface: What is Linux boot security?
Secure Boot allows only approved operating systems to run on the machine. Secure Boot checks the cryptographic signature in the operating system’s bootloader to see if it matches a registered key in the UEFI firmware. If a match is found, the boot process proceeds.
Background: UEFI Secure Boot requires that the operating system kernel is signed with a recognized private key. UEFI Secure Boot then verifies the signature using the corresponding public key. For Red Hat Enterprise Linux Beta releases, the kernel is signed with a Red Hat Beta-specific private key. UEFI Secure Boot attempts to verify the signature using the corresponding public key, but because the hardware does not recognize the Beta private key, Red Hat Enterprise Linux Beta release system fails to boot. Therefore, to use UEFI Secure Boot with a Beta release, add the Red Hat Beta public key to your system using the Machine Owner Key (MOK) facility.
To determine your version, use grub-install -V. (GRUB2 is configured with /boot/grub2/grub[.]cfg)
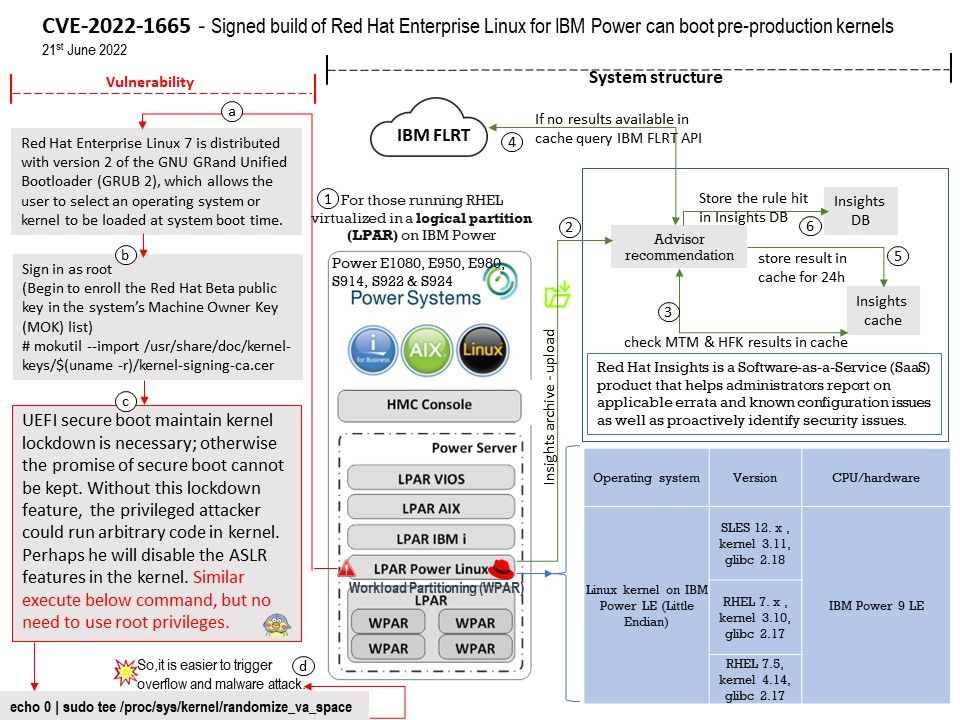
Red Hat Enterprise Linux 7 is distributed with version 2 of the GNU GRand Unified Bootloader (GRUB 2), which allows the user to select an operating system or kernel to be loaded at system boot time.
Vulnerability details: A set of pre-production kernel packages of Red Hat Enterprise Linux for IBM Power architecture can be booted by the grub in Secure Boot mode even though it shouldn’t. These kernel builds don’t have the secure boot lockdown patches applied to it and can bypass the secure boot validations, allowing the attacker to load another non-trusted code.
Red Hat Bugzilla – Bug 2089529 – https://bugzilla.redhat.com/show_bug.cgi?id=2089529