.jpg?width=1920&height=1080&fit=bounds)
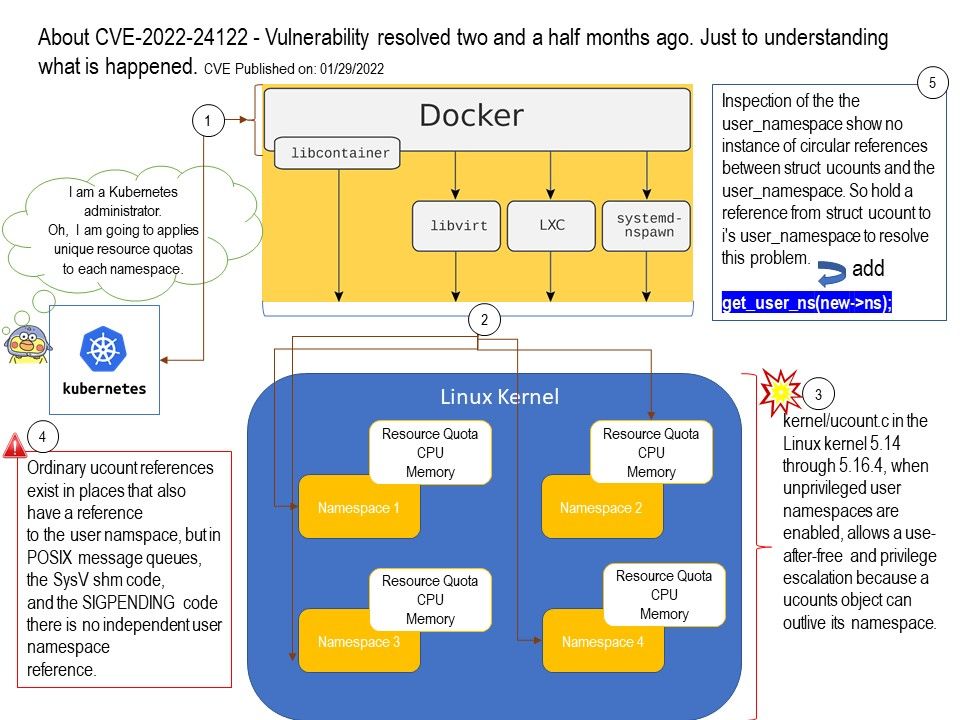
Preface: If the loop can be influenced by an attacker, this weakness could allow attackers to consume excessive resources such as CPU or memory.
Background: Django itself is web framework used for developing web applications based on python. Which is used for making development proccess more simple and easy. It provides various built in things such as Django ORM, Forms, Security, Authentication, Admin and many third party packages that are available on django packages.
MultiPartParser
- It parses the incoming request form contents into QueryDict.
- It is used if “Content-Type” is set to “multipart/form-data”.
- request.data will be a QueryDict containing all the form parameters.
- request.files will be a QueryDict containing all the form files.
- FormParser and MultiPartParser together used for full support of HTML form data.
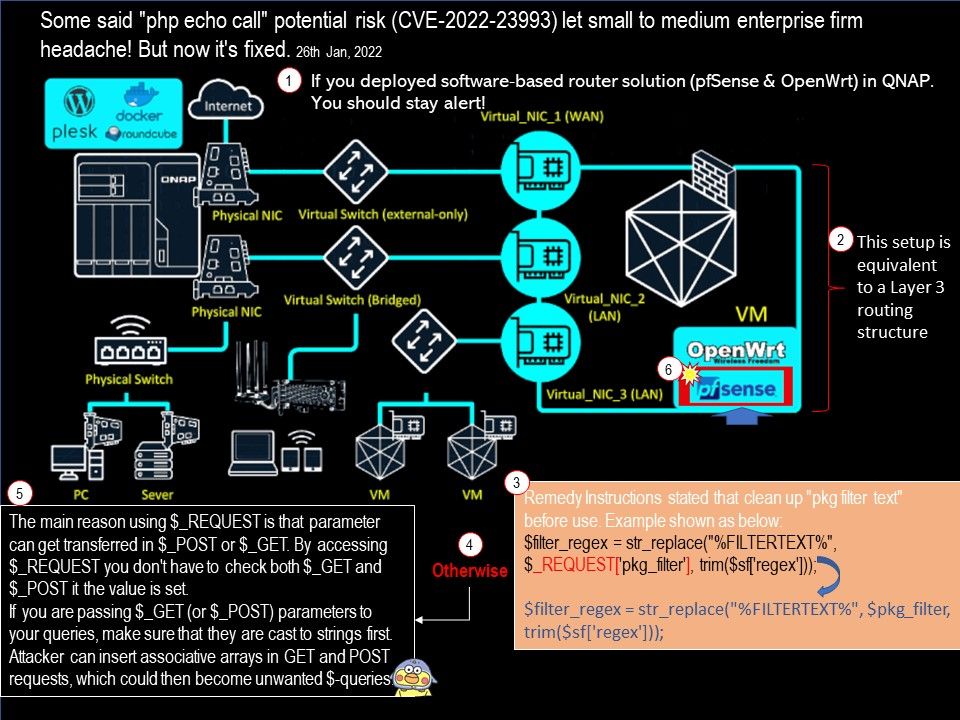
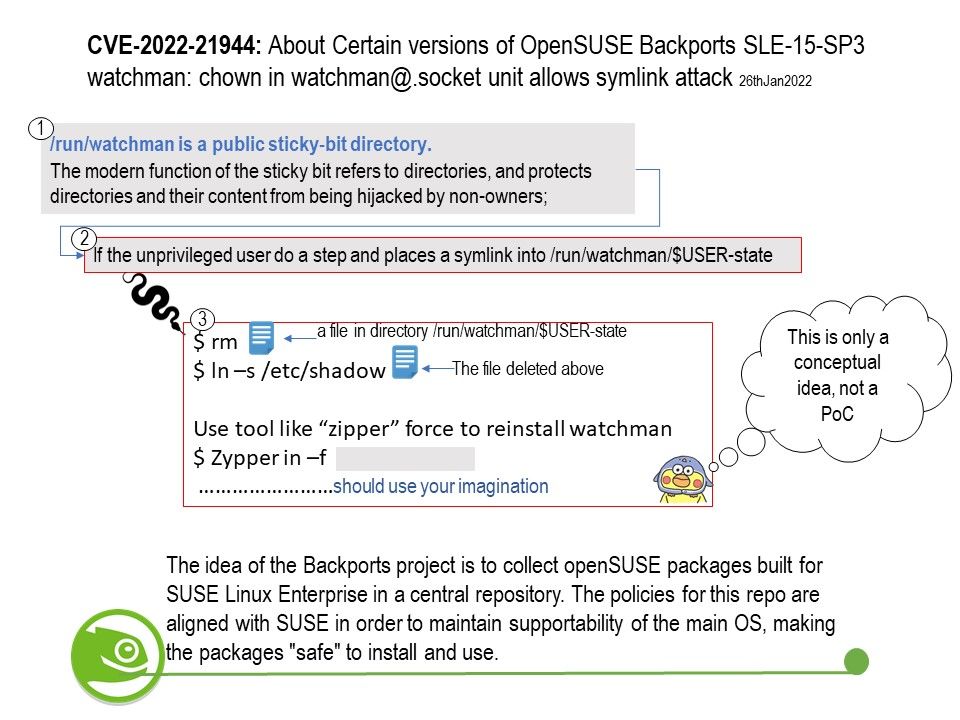
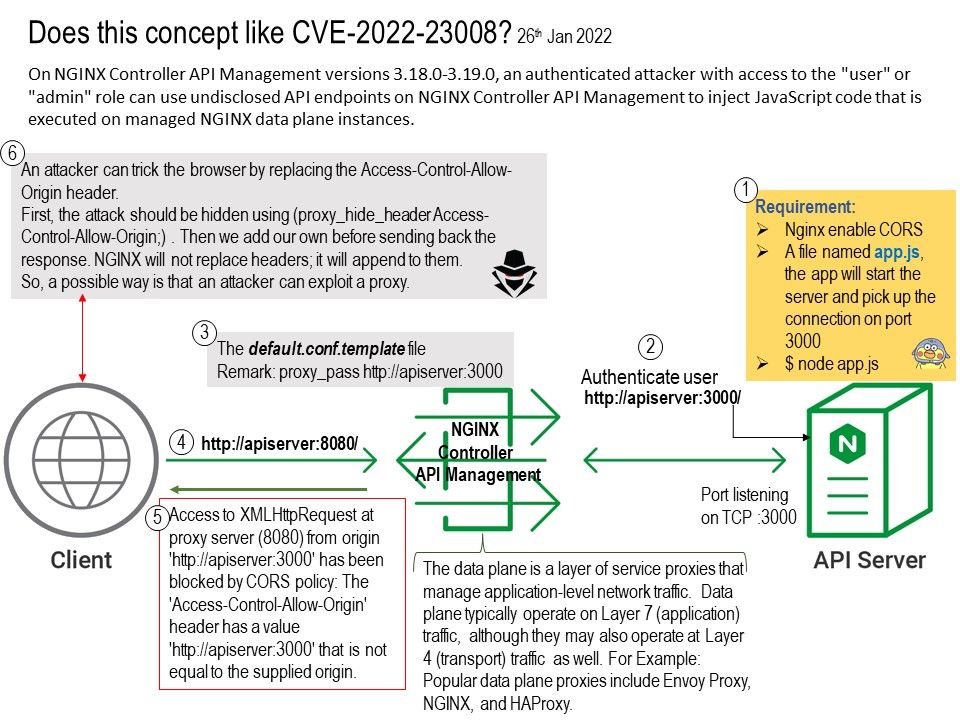
Vulnerability details: In below operating process sequence, a design weakness occurs . For more details, please see below:
Factors that expose this vulnerability. Content-Type should contain multipart and the boundary information.
- Step 1. UploadHandler instance that performs operations on the uploaded data.
- Step 2. Parse the header to get the boundary to split the parts.
- Step 3. Whether or not to signal a file-completion at the beginning of the loop.
- Step 4. If step 3 is negative, it cannot be sure a file is complete until it hit the next boundary/part of the multipart content. Loop will continue to run until the Boolean expression is TRUE.
Impact: An issue was discovered in MultiPartParser in Django 2.2 before 2.2.27, 3.2 before 3.2.12, and 4.0 before 4.0.2. Passing certain inputs to multipart forms could result in an infinite loop when parsing files.
Remedy: Fixed CVE-2022-23833 (Fixed DoS possiblity in file uploads). Please refer to the link for details – https://github.com/django/django/blob/main/django/http/multipartparser.py
.jpg?width=1920&height=1080&fit=bounds)