Official last updated on May 8, 2024. An early advisory for this vulnerability was issued on March 5, 2024.
Preface: If you recall, this design flaw was discovered in April 2021. Has it been fixed? Or it is vendors fine-tuned their vulnerability management strategies?
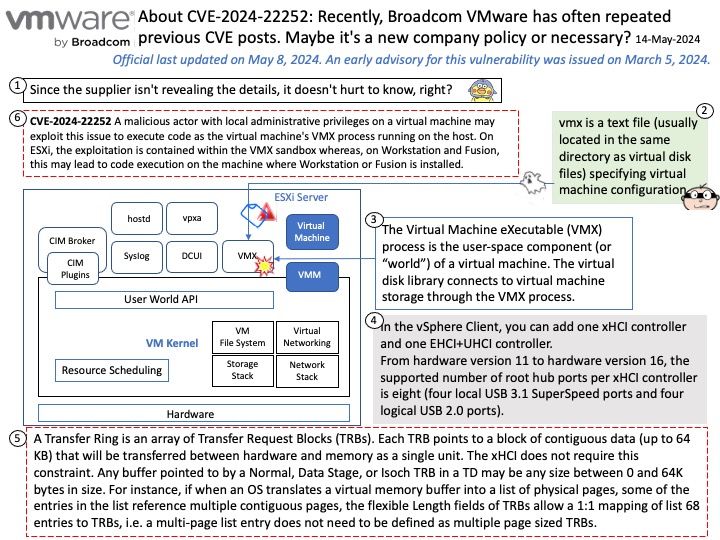
Background: A Transfer Ring is an array of Transfer Request Blocks (TRBs). Each TRB points to a block of contiguous data (up to 64 KB) that will be transferred between hardware and memory as a single unit. The xHCI does not require this constraint. Any buffer pointed to by a Normal, Data Stage, or Isoch TRB in a TD may be any size between 0 and 64K bytes in size. For instance, if when an OS translates a virtual memory buffer into a list of physical pages, some of the entries in the list reference multiple contiguous pages, the flexible Length fields of TRBs allow a 1:1 mapping of list 68 entries to TRBs, i.e. a multi-page list entry does not need to be defined as multiple page sized TRBs.
Vulnerability details: VMware ESXi, Workstation, and Fusion contain a use-after-free vulnerability in the XHCI USB controller. VMware has evaluated the severity of this issue to be in the Critical severity range with a maximum CVSSv3 base score of 9.3 for Workstation/Fusion and in the Important severity range with a maximum CVSSv3 base score of 8.4 for ESXi.
Known Attack Vectors: A malicious actor with local administrative privileges on a virtual machine may exploit this issue to execute code as the virtual machine’s VMX process running on the host. On ESXi, the exploitation is contained within the VMX sandbox whereas, on Workstation and Fusion, this may lead to code execution on the machine where Workstation or Fusion is installed.
Official announcement: Please refer to the link for details – https://support.broadcom.com/web/ecx/support-content-notification/-/external/content/SecurityAdvisories/0/24266