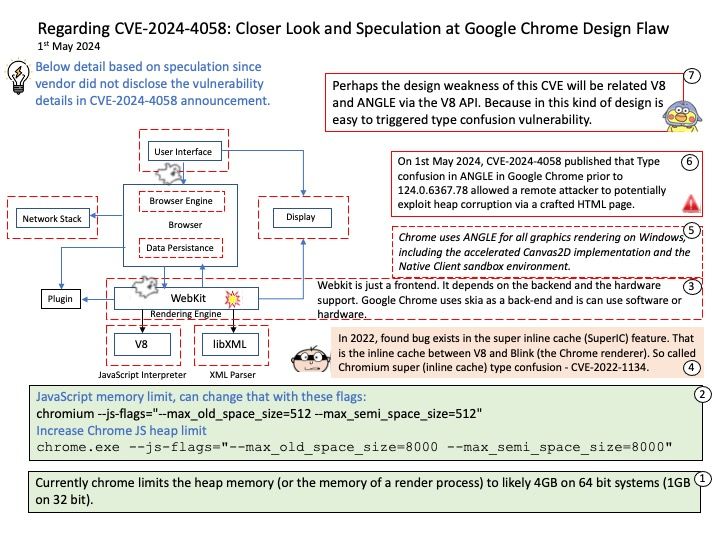
Preface: Type confusion vulnerability can be powerful. According to Common Weakness Enumeration (CWE) The program allocates or initializes a resource such as a pointer, object, or variable using one type, but it later accesses that resource using a type that is incompatible with the original type. When the program accesses the resource using an incompatible type, this could trigger logical errors because the resource does not have expected properties. In languages without memory safety, such as C and C++, type confusion can lead to out-of-bounds memory access.
Background: Chrome uses ANGLE not only for WebGL, but also for its implementation of the 2D HTML5 canvas and for the graphics layer of the Google Native Client(which is OpenGL ES 2.0 compatible). Safari web browser uses ANGLE as basis for its WebGL implementation. Firefox uses ANGLE as the default WebGL backend on Windows.
ANGLE provides OpenGL ES 2.0 and EGL 1.4 libraries and dlls. You can use these to build and run OpenGL ES 2.0 applications on Windows, Linux, Mac and Android.
Vulnerability details: Type confusion in ANGLE in Google Chrome prior to 124.0.6367.78 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. (Chromium security severity: Critical)
Official announcement: Please refer to the link for details – https://chromereleases.googleblog.com/2024/04/stable-channel-update-for-desktop_24.html