Preface:
Renaissance – The period of this revival, roughly the 14th through the 16th century, marking the transition from medieval to modern times.
Background:
The virus and malware wreak havoc in information technology environment in past decade especially on Microsoft windows operating system platform. It looks that a transformation was happened since smartphone leading the IT technology trend today. The percentage of usage for smartphones are bigger than traditional computer devices (desktop, notebook and server).
Transformation of cyber attack scenario
The major of cyber attacks in information technology environment are given by tradition virus since early 90’s. A quick and simplified explanation below diagram is able to awaken your memories in this regard.
The Evolution diagram of virus, worm, malware and ransomware
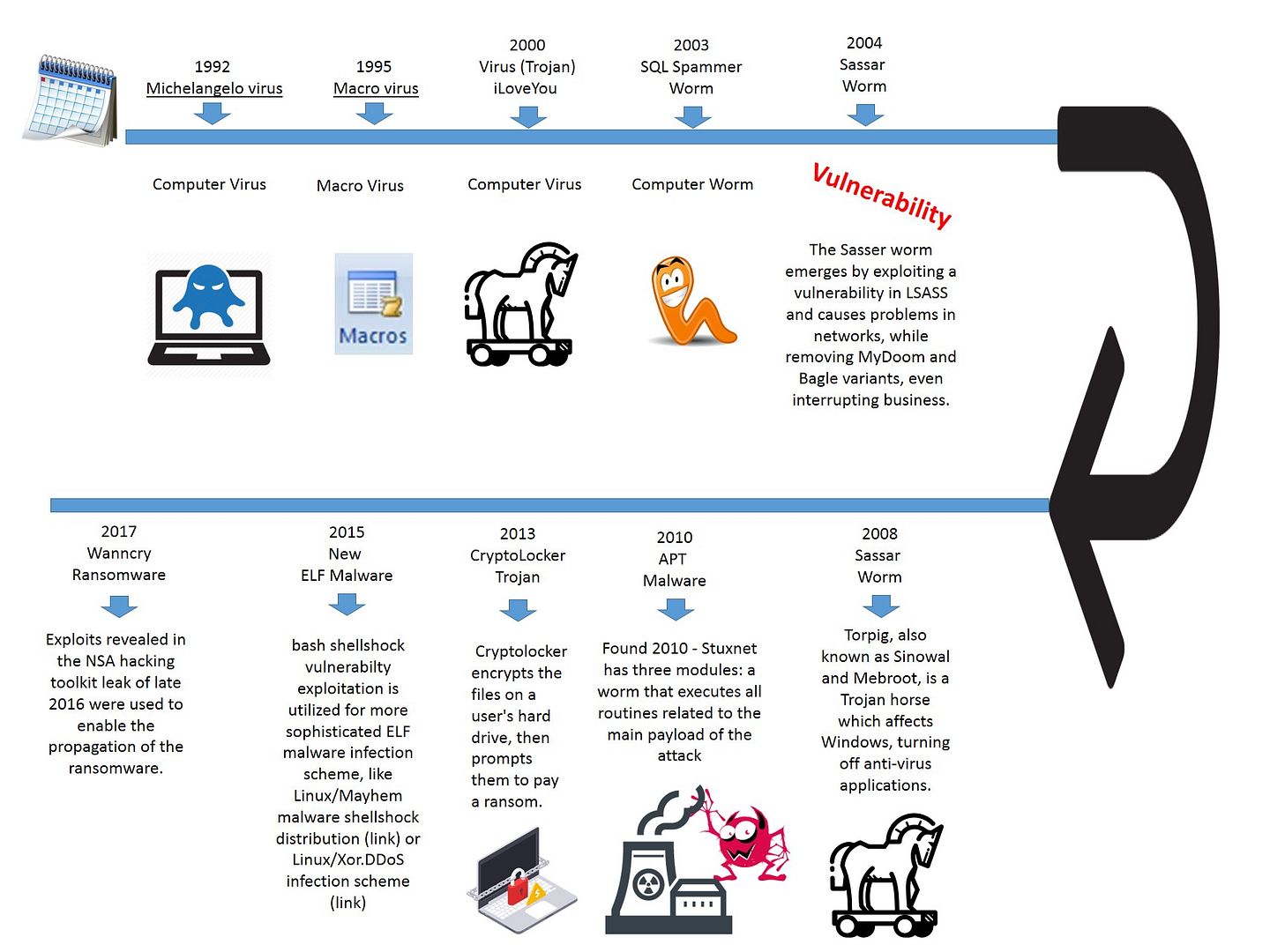
Remark: Perhaps we shown the generations of the virus and malware past three decades. The diagram looks simple. However it represents the virus and malware in the specific period of time.
The attack surface targets to Microsoft products till SmartPhone appears.
We all known the design goal of virus and malware targeted Microsoft products fundamentally. We feel that Linux base operating system will be provided a secure environment. But the question is that which element change the atmosphere in silent way?
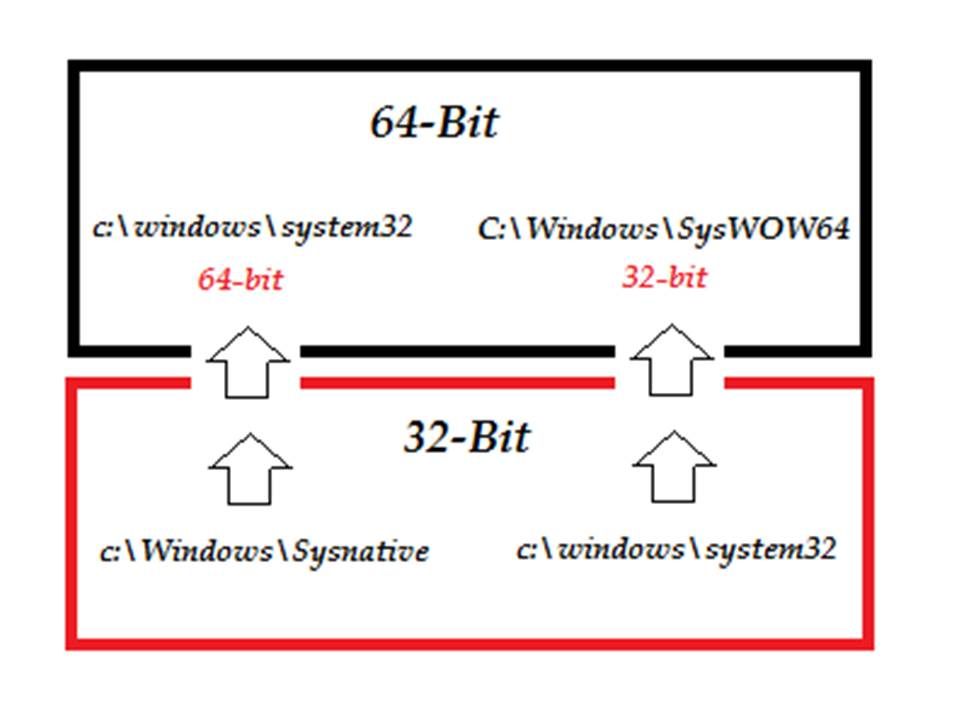
We understand that the infection of malware divided into four phase (see below diagram). Since the malicious file (so called dropper – file) relies on the PE (portable executable) to execute the infiltation. The way is that the malicious code will try to infiltrate for executables, object code, DLLs, FON Font files, and others used in 32-bit and 64-bit versions of Windows operating systems.
However the specifics mechanism does not work in Linux environment till ELF malware invented.
Stages of a Malware Infection and technology evolution overview
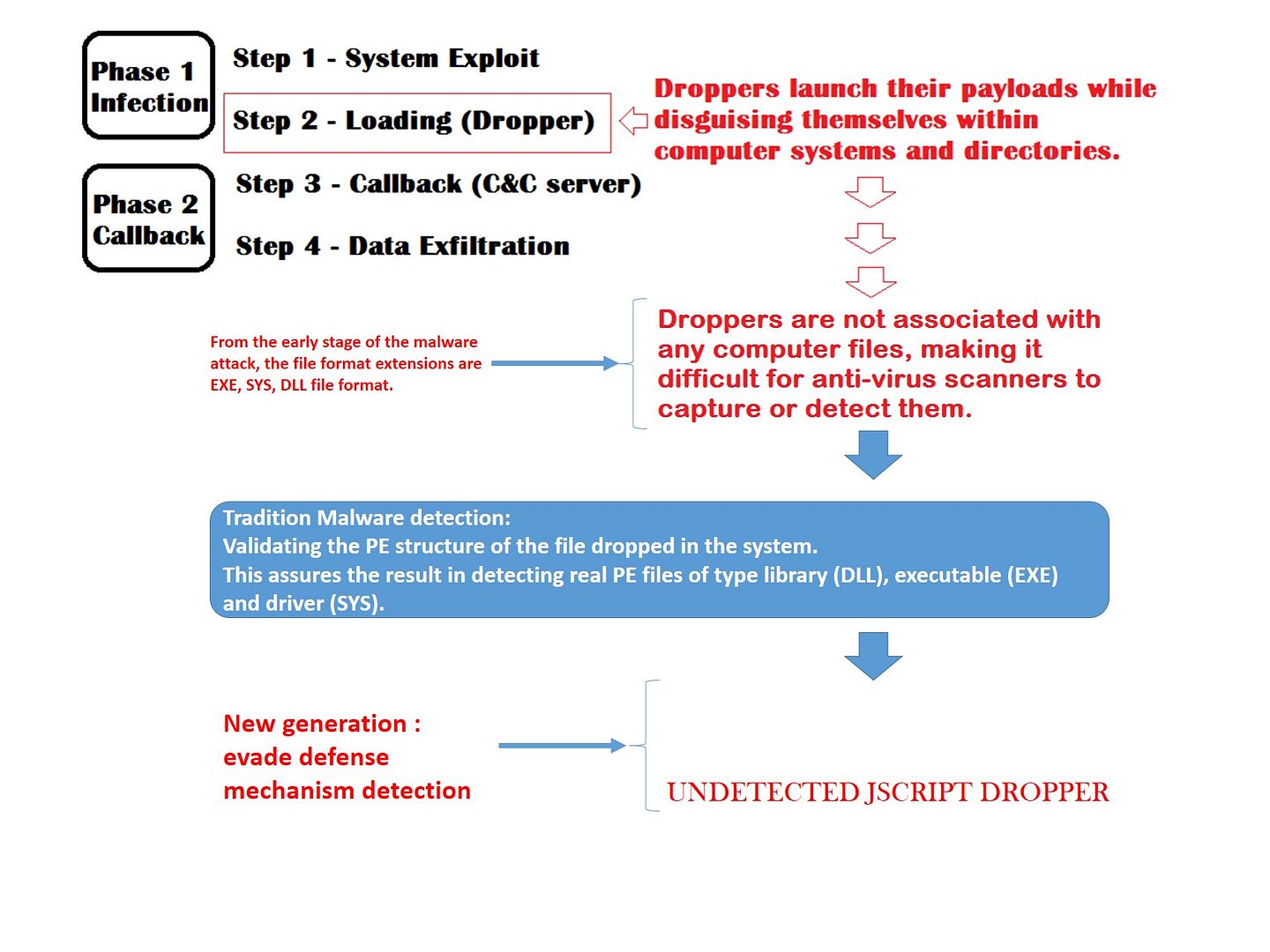
Where it began? Code Injection to Linux world.
Linux Operating system looks like a well protected castle but a beast live inside. Whether are you familiar with ptrace() command on Linux? With reference to tutorial (execute man command in Linux). The ptrace() system call provides a means by which a parent process may observe and control the execution of another process, and examine and change its core image and registers. It is primarily used to implement breakpoint debugging and system call tracing.”
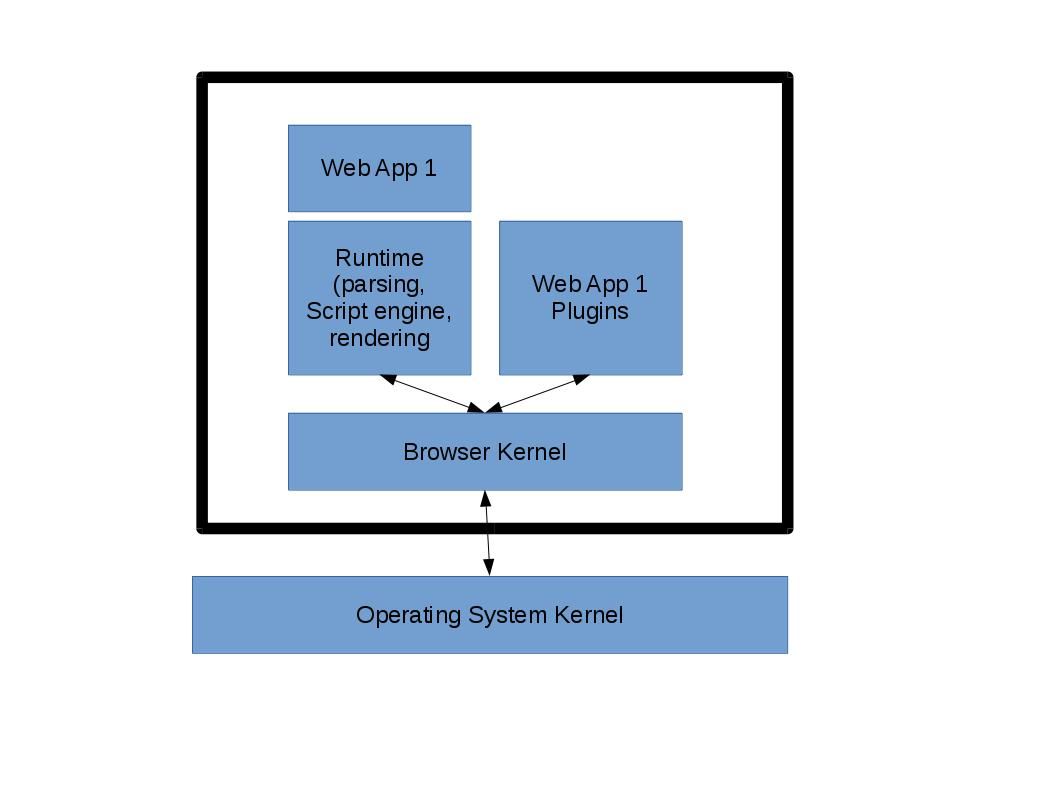
Docker, an open-source technology. Meanwhile Docker is the company driving the container movement and the only container platform provider to address every application across the hybrid cloud. Microsoft cloud product family also embraced Docker. Below informatics diagram can bring an idea to you on how the docker works.
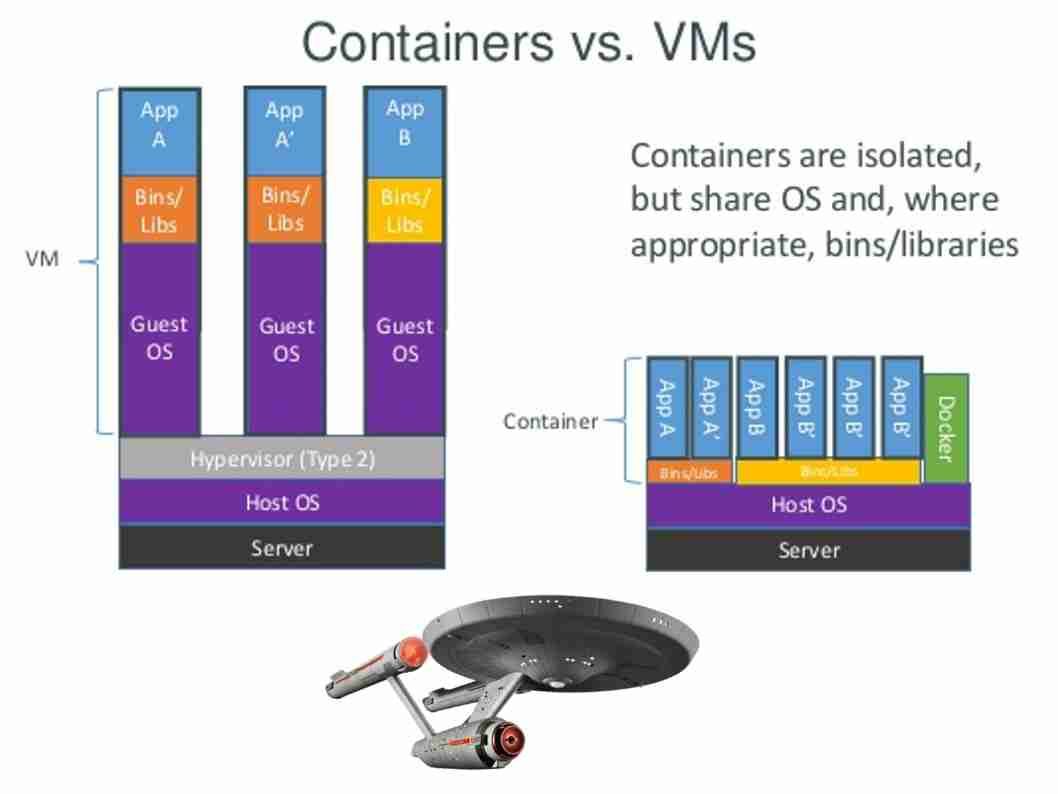
No matter Fedora workstation or Cloud computing platform (Docker). The command (ptrace()) can do the magic. Even though attach to system process!
Reference: you can disable this behavior by the following:
If you are using Fedora (see below for reference)
echo 0 > /proc/sys/kernel/yama/ptrace_scope
or modify (with root privileges)
/etc/sysctl.d/10-ptrace.conf
If you are using Docker, you will probably need below options:
docker run --cap-add=SYS_PTRACE --security-opt seccomp=unconfined
Above detail information intends to proof of comment which described earlier. Linux Operating system looks like a well protected castle but a beast live inside. Why? If there is a zero day vulnerability occurred in Linux. A ELF format of file embedded malicious code relies on zero day vulnerability execute the attack. That is to awake the beast with privileges escalation. This assumption not rare. Dirty COW (CVE-2016-5195) is a privilege escalation vulnerability in the Linux Kernel found last year. Such incident not only harm to workstation. It also includes cloud infrastructure. From technical point of view, it do not have difference in between Microsoft Product and Linux product.
ELF malware space
Above example highlight the ELF format file. ELF is flexible, extensible, and cross-platform, not bound to any given central processing unit (CPU) or instruction set architecture. This has allowed it to be adopted by many different operating systems on many different hardware platforms. Since smartphone especially Android phone fully utilize Linux OS platform. Perhaps the vendor announcement told this is not a standard Linux OS. But the truth is that they are using Linux base kernel.
According to the IDC Quarterly Mobile Phone Tracker, phone companies shipped a total of 344.3 million smartphones worldwide in the first quarter of 2017 (1Q17). And such away the cyber attack includes BYOD botnet or IoT botnet wreak havoc.
In order to cope with IT technology and smartphone trend. The attackers will build ELF malware using a customized builder. And therefore the malware of target to Linux system includes smartphone rapidly growth. For instance, Gyrfalcon implant, which targets OpenSSH clients on a wider variety of Linux platforms. Should you have interest, please refer below url for reference.
https://wikileaks.org/vault7/#OutlawCountry
Summary:
Information security expert found Stagefright exploit puts millions of Android devices at risk on early 2016. The attack is effective against devices running Android versions 2.2 through 4.0 and 5.0 and 5.1. Another way round of malware attack to android devices is copyCat. CopyCat Malware Infected 14M Android Devices, Rooted 8M, in 2016. Since this is a history but the malware attacks to Linux world are on the way!