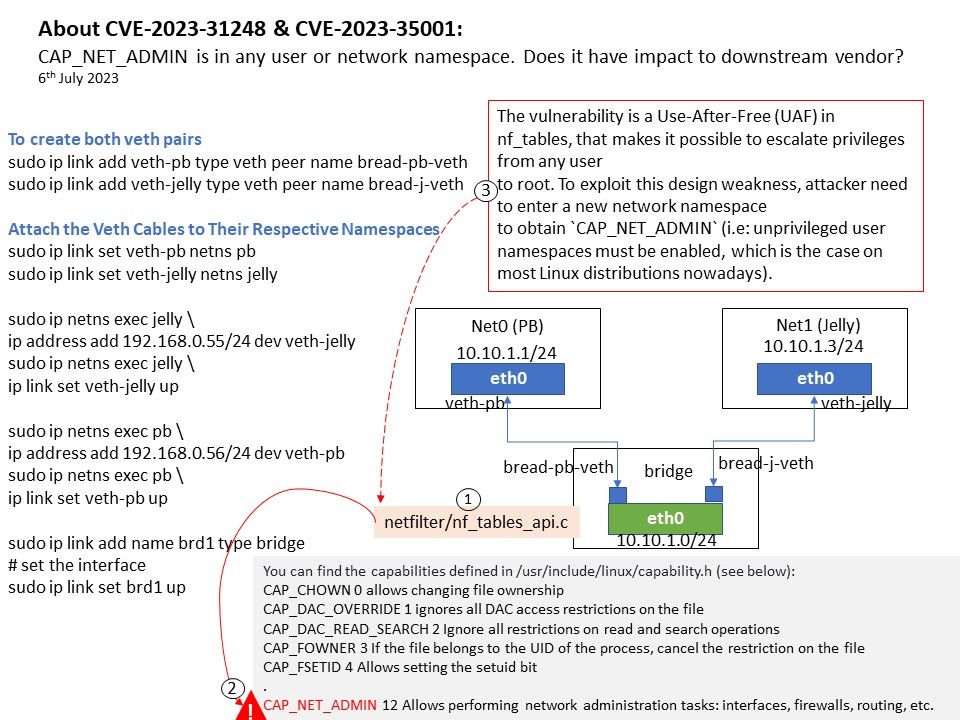
Preface: CAP_NET_ADMIN is in any user or network namespace.
Background: The “Capabilities” mechanism was introduced after the Linux kernel 2.2. If the “Capabilities” setting is incorrect,
it will give attackers an opportunity to achieve privilege escalation. Linux capabilities provide a subset of the available root privileges to a process.
Starting from the Linux-2.1 kernel, the concept of capability is introduced to achieve grained access control.
You can find the capabilities defined in /usr/include/linux/capability[.]h (see below):
CAP_CHOWN 0 allows changing file ownership
CAP_DAC_OVERRIDE 1 ignores all DAC access restrictions on the file
CAP_DAC_READ_SEARCH 2 Ignore all restrictions on read and search operations
CAP_FOWNER 3 If the file belongs to the UID of the process, cancel the restriction on the file
CAP_FSETID 4 Allows setting the setuid bit
.
CAP_NET_ADMIN 12 Allows performing network administration tasks: interfaces, firewalls, routing, etc.
Vulnerability details:
CVE-2023-31248 Linux Kernel nftables Use-After-Free Local Privilege Escalation Vulnerability;nft_chain_lookup_byid() failed to check whether a chain was active and CAP_NET_ADMIN is in any user or network namespace.
For details, please refer to the link – https://www.tenable.com/cve/CVE-2023-31248
CVE-2023-35001 Linux Kernel nftables Out-Of-Bounds Read/Write Vulnerability; nft_byteorder poorly handled vm register contents when CAP_NET_ADMIN is in any user or network namespace
Focus on CVE-2023-31248
This is due to the nft_chain_lookup_by id ignoring the genmask.
Remark: The Genmask field is the bit mask that IP applies to the destination address from the packet to see if the address matches the destination value in the table.
If a bit is on in the bit mask, the corresponding bit in the destination address is significant for matching the address.
Once the first table is removed, all the member objects, as well as the table itself, are kfree()’d, but the references will be kept in the second table, so it encountered a use-after-free condition.