Preface: AMD Secure Encrypted Virtualization-Secure Nested Paging (SEV-SNP) is a feature of AMD EPYC processors that adds strong memory integrity protection to help prevent malicious hypervisor-based attacks in order to create an isolated execution environment.
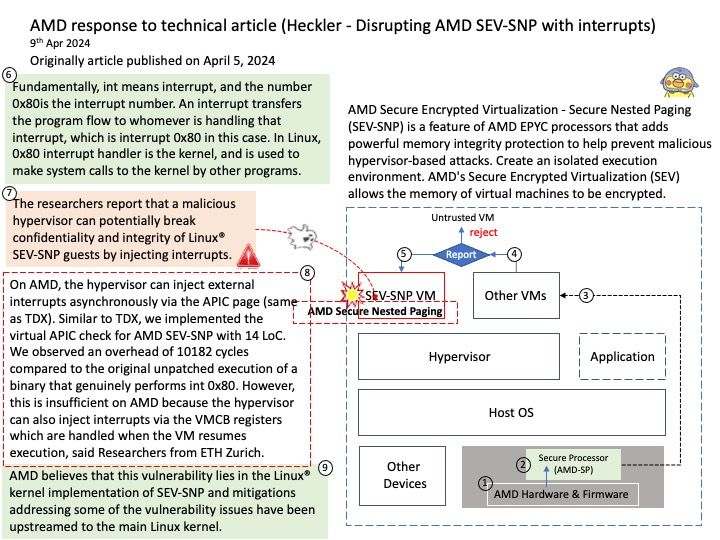
Background: Fundamentally, int means interrupt, and the number 0x80is the interrupt number. An interrupt transfers the program flow to whomever is handling that interrupt, which is interrupt 0x80 in this case. In Linux, 0x80 interrupt handler is the kernel, and is used to make system calls to the kernel by other programs.
In current Linux, 32-bit syscalls (including int 0x80 from 64-bit) eventually end up indo_syscall_32_irqs_on(struct pt_regs *regs). It dispatches to a function pointer ia32_sys_call_table, with 6 zero-extended args. This maybe avoids needing a wrapper around the 64-bit native syscall function in more cases to preserve that behaviour, so more of the ia32 table entries can be the native system call implementation directly.
Vulnerability details: Researchers from ETH Zurich have shared with AMD a paper titled “Heckler: Disrupting AMD SEV-SNP with Interrupts.”
In their paper, the researchers report that a malicious hypervisor can potentially break confidentiality and integrity of Linux® SEV-SNP guests by injecting interrupts.
Official announcement: Please refer to the link for details – https://www.amd.com/en/resources/product-security/bulletin/amd-sb-3008.html