Preface: You can clear the cache of nscd by performing the following actions:
Execute the following command: sudo /etc/init[.]d/nscd restart.
Background:
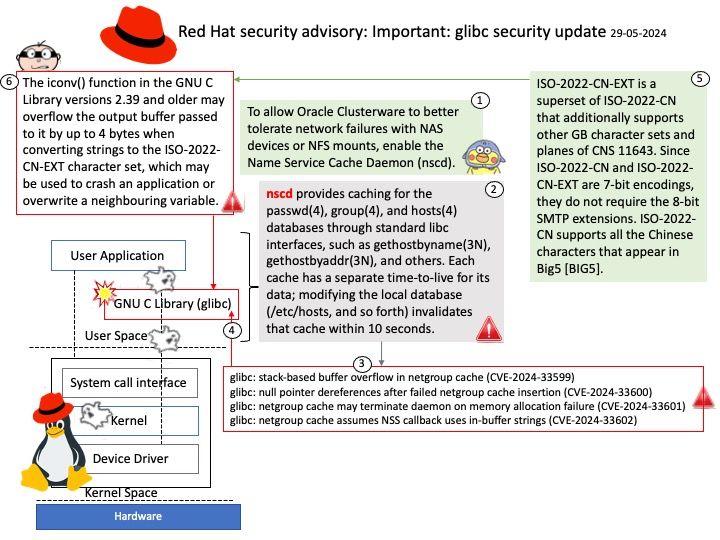
Nscd is a daemon that provides a cache for the most common name service requests. The default configuration file, /etc/nscd. conf, determines the behavior of the cache daemon.
The glibc packages provide the standard C libraries (libc), POSIX thread libraries (libpthread), standard math libraries (libm), and the name service cache daemon (nscd) used by multiple programs on the system. Without these libraries, the Linux system cannot function correctly.
The iconv() function shall convert the sequence of characters from one codeset, in the array specified by inbuf, into a sequence of corresponding characters in another codeset, in the array specified by outbuf. The codesets are those specified in the iconv_open() call that returned the conversion descriptor, cd.
Vulnerability details:
glibc: Out of bounds write in iconv may lead to remote code execution (CVE-2024-2961)
glibc: stack-based buffer overflow in netgroup cache (CVE-2024-33599)
glibc: null pointer dereferences after failed netgroup cache insertion (CVE-2024-33600)
glibc: netgroup cache may terminate daemon on memory allocation failure (CVE-2024-33601)
glibc: netgroup cache assumes NSS callback uses in-buffer strings (CVE-2024-33602)
Official announcement: For detail, please refer to link – https://access.redhat.com/errata/RHSA-2024:3464