Preface: The software writes data past the end, or before the beginning, of the intended buffer. Typically, this can result in corruption of data, a crash, or code execution.
Background: In the Android system, an application has at least one process, and each process has its own independent resources and memory space. Other processes cannot arbitrarily access the memory and resources of the current process. If you want to communicate between processes, you need to use IPC means.
Virtual memory managed by the kernel, with the help of hardware (the memory management unit). Multiple mappings are maintained at all times. In modern smartphone design, kernel has one or two of its own, shared by all processes, and each process gets its own user-space mapping.
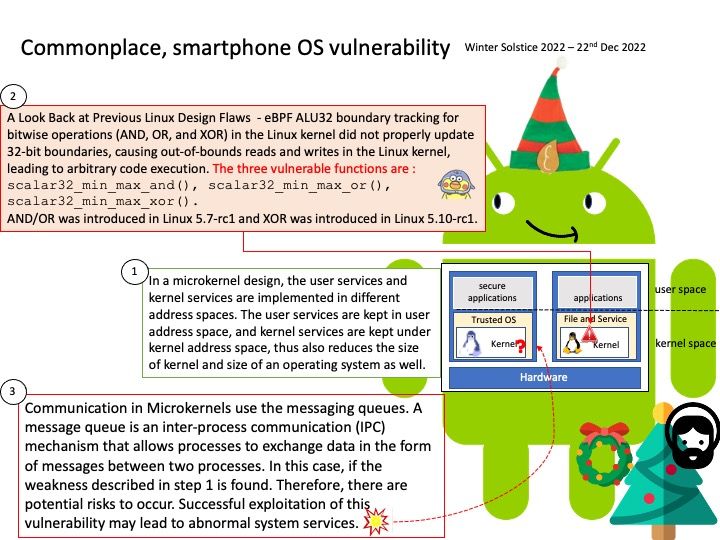
A Look Back at Previous Linux Design Flaws – eBPF ALU32 boundary tracking for bitwise operations (AND, OR, and XOR) in the Linux kernel did not properly update 32-bit boundaries, causing out-of-bounds reads and writes in the Linux kernel, leading to arbitrary code execution. The three vulnerable functions are scalar32_min_max_and(), scalar32_min_max_or(), scalar32_min_max_xor(). AND/OR was introduced in Linux 5.7-rc1 and XOR was introduced in Linux 5.10-rc1.
Research and speculation: Communication in Microkernels use the messaging queues. A message queue is an inter-process communication (IPC) mechanism that allows processes to exchange data in the form of messages between two processes. In this case, if the Linux kernel did not properly update 32-bit boundaries, Therefore, there are potential risks to occur. Successful exploitation of this vulnerability may lead to abnormal system services.
Today is the winter solstice, I wish you a happy dinner with your family tonight.