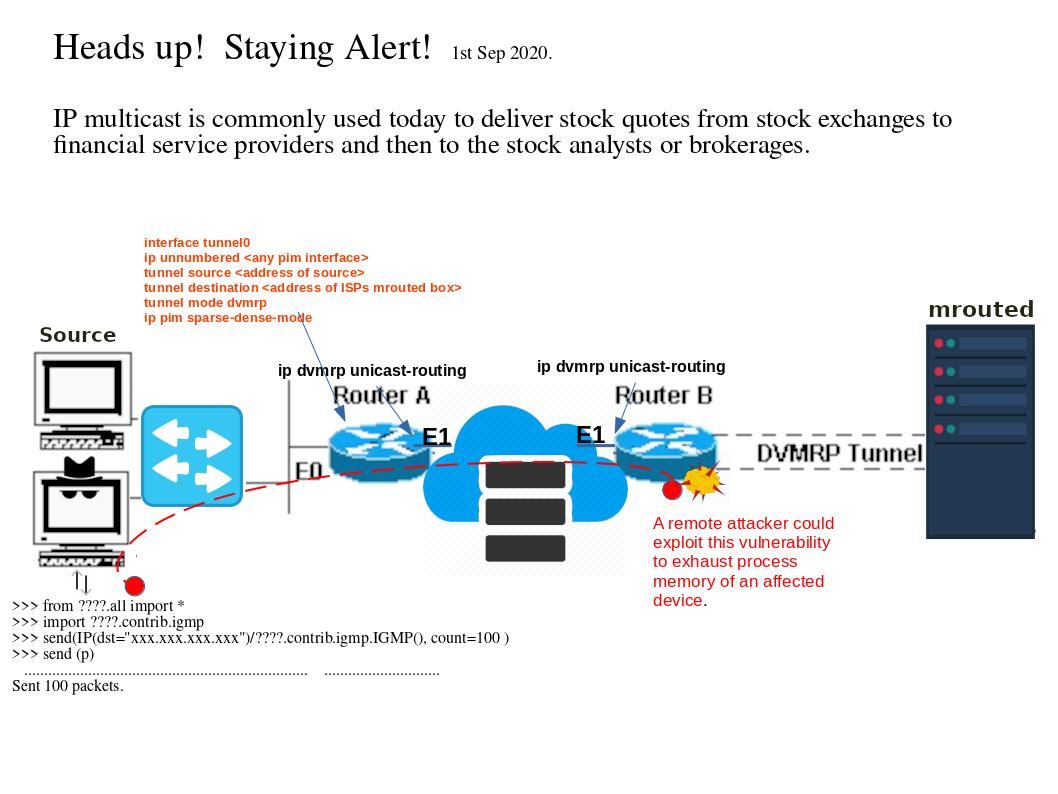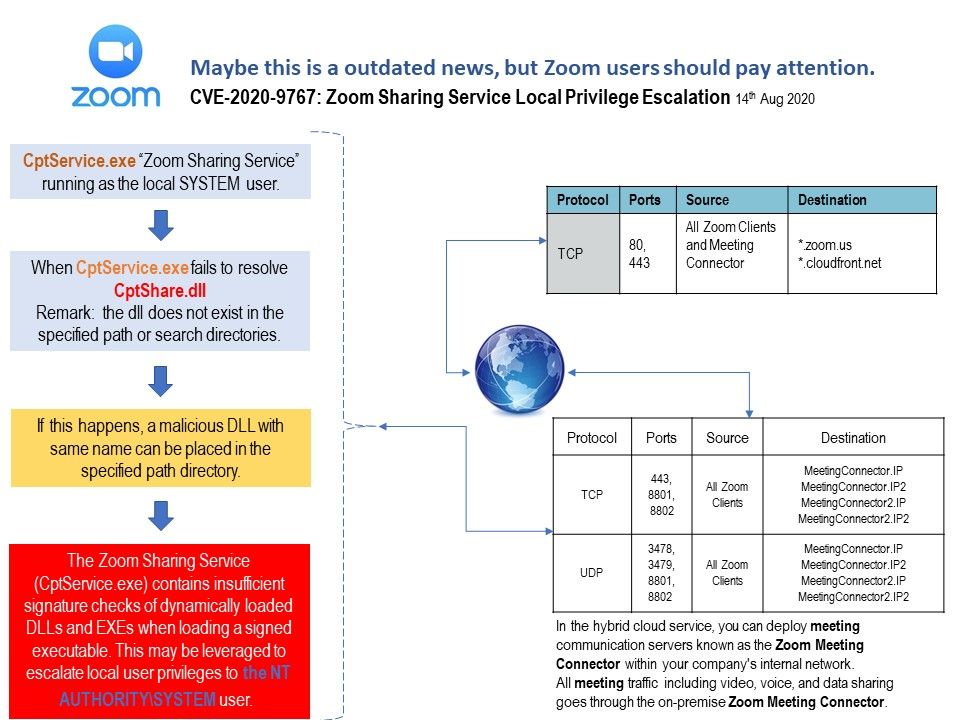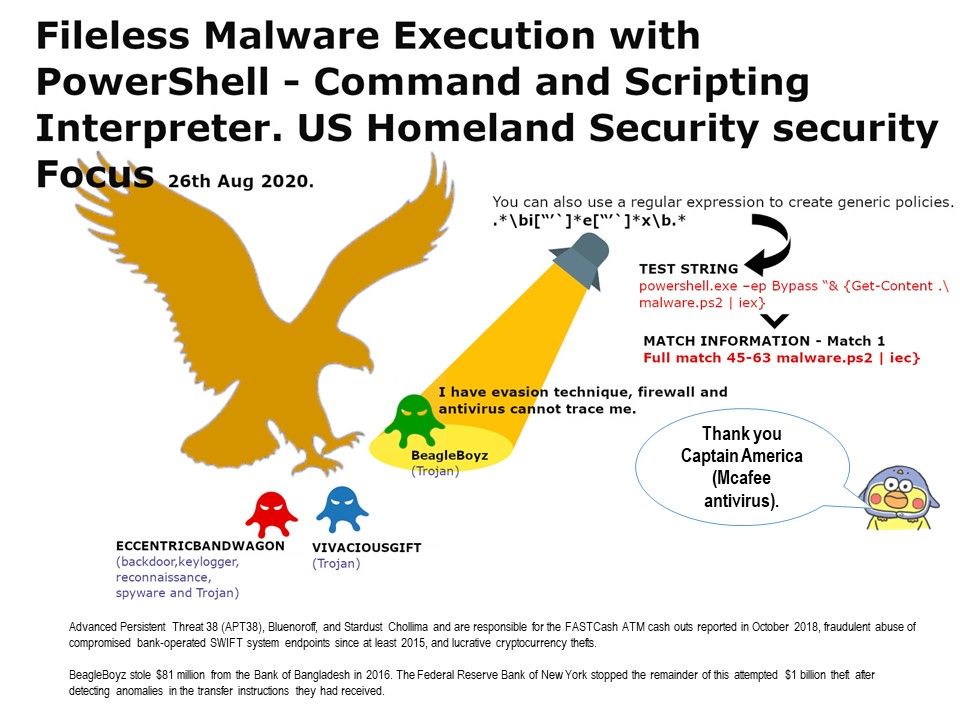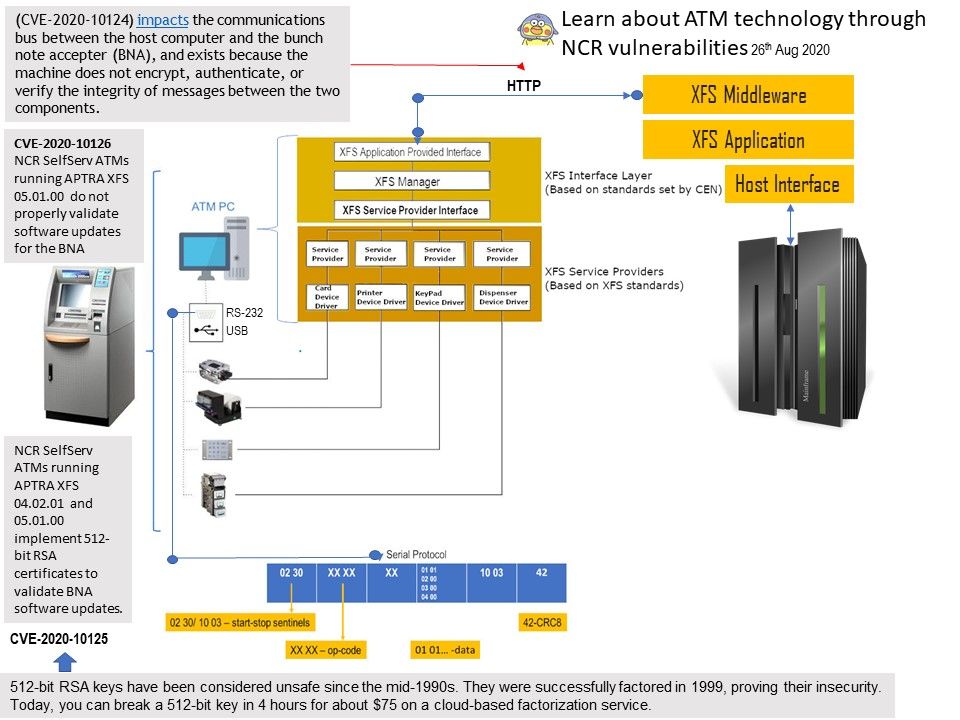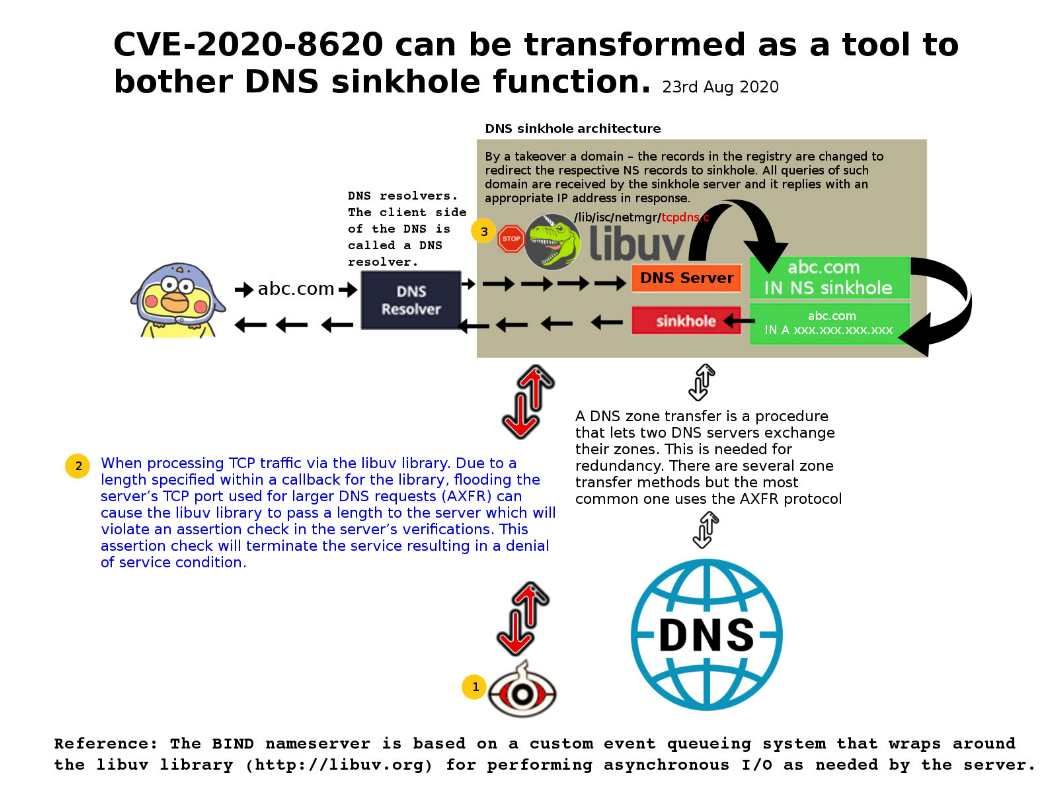
Preface: NVD published date on 09/03/2020. Strongly believe that technical matter was resolved by vendor completely. However we should recording this issue in notes. As we know, hacker jump to client network will hide himself for a period of time. Sometimes such action cater for their data exfiltration activities or ….
Techincal background: Slogan of Thomson Reuters Eikon. Access an incredible depth and breadth of financial analysis data to make smarter decisions. Reuters Eikon is a financial data platform which includes data on financial markets, companies’ (especially listed companies’) financial data, financial news, macro data etc. The product is analogous to the Bloomberg Terminal aka “Open Bloomberg”. It allow client install the Eikon software on their company workstation.
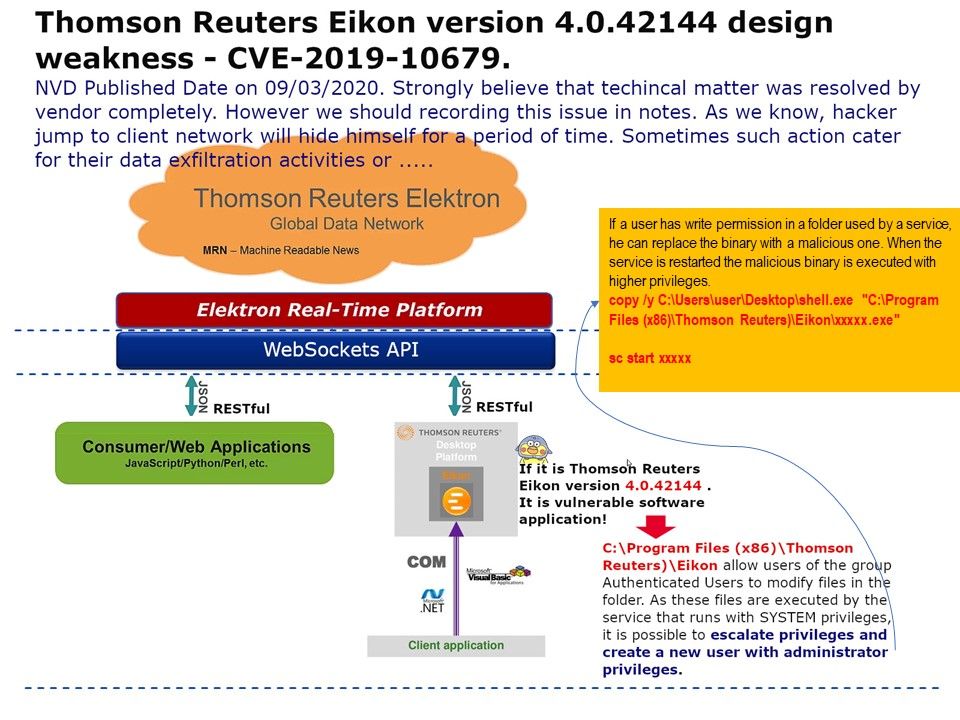
Vulnerability details: The current file permissions of the directory C[:]\Program Files (x86)\Thomson Reuters)\Eikon allow users of the group Authenticated Users to modify files in the folder. As these files are executed by the service that runs with SYSTEM privileges, it is possible to escalate privileges and create a new user with administrator privileges.
If a user has write permission in a folder used by a service, he can replace the binary with a malicious one. When the service is restarted the malicious binary is executed with higher privileges. Please refer to the attached picture for details.
Since Reuters and related terminal will be installed in Investment bank or broker firm dealing room. Perhaps this is the area which lure the hacker interest. And is a typical example of insider threats.
For my point of view, apply advanced cyber security filter and scanning function in this area not a possible solution. It was because it will encounter false alarm and therefore interrupt the services. In order to avoid unknown incident happen in this place, SIEM + (Predictive analysis tools like Darktrace) are the appropriate solution.
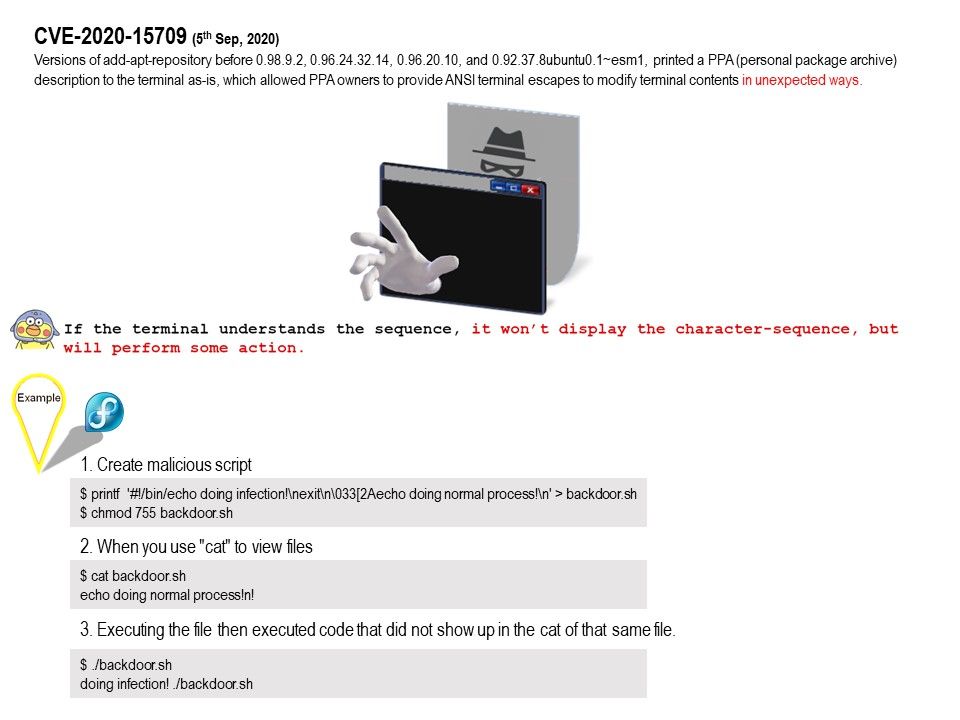
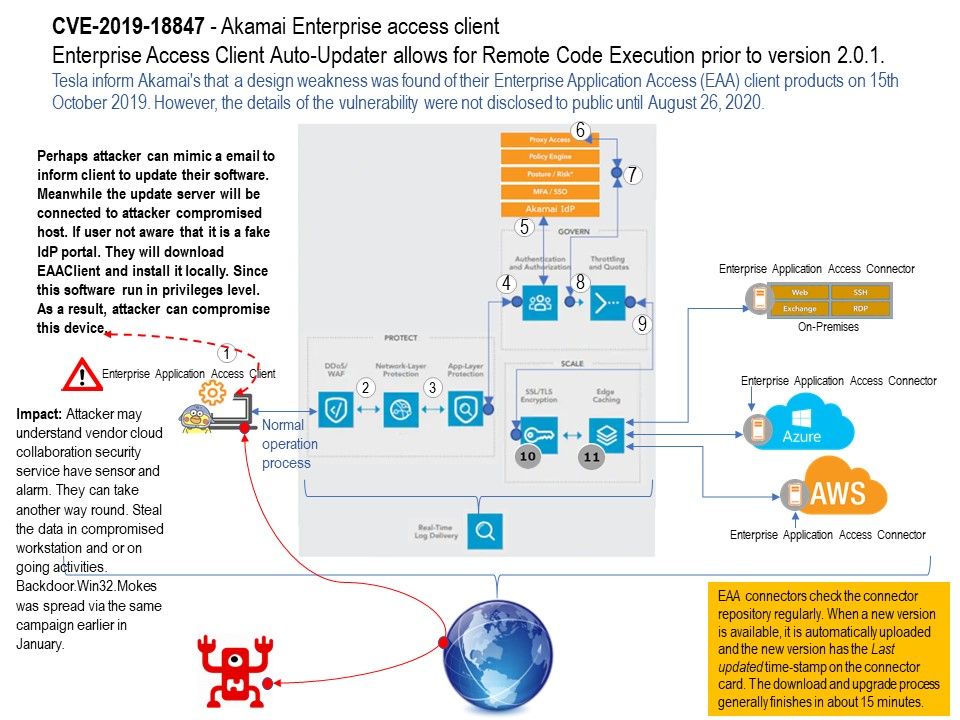
.jpg?width=1920&height=1080&fit=bounds)