Preface: Android 13, released on August 15, 2022, is the latest version, and the recently released Android 12.1/12L includes improvements specific to foldable phones, tablets, desktop-sized screens and Chromebooks.
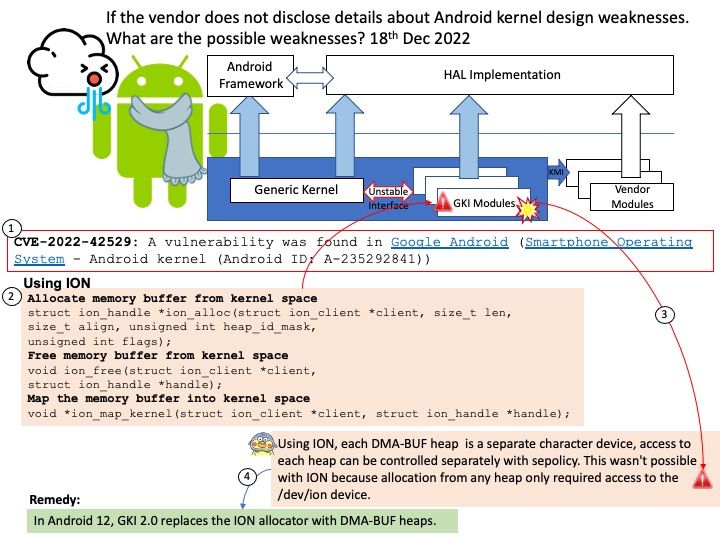
Background: In Android 11, the Android Common Kernel v5. Before kernel 4.12, opening /dev/ion allocated an Ion client. The IOC_ION_ALLOC ioctl allocated a new buffer and returned it to userspace as an Ion handle (an opaque integer meaningful only to the Ion client that allocated it). To map buffers into userspace or share them with other processes, Ion handles were re-exported as dma-buf fds using the IOC_ION_SHARE ioctl.
My speculation based on the details above: Using ION, each DMA-BUF heap is a separate character device, access to each heap can be controlled separately with sepolicy. This wasn’t possible with ION because allocation from any heap only required access to the /dev/ion device.
Vulnerability details: CVE-2022-42529 – A vulnerability was found in Google Android Smartphone Operating System – Android kernel (Android ID: A-235292841))
Official announcement: For details, see the link – https://source.android.com/docs/security/bulletin/pixel/2022-12-01