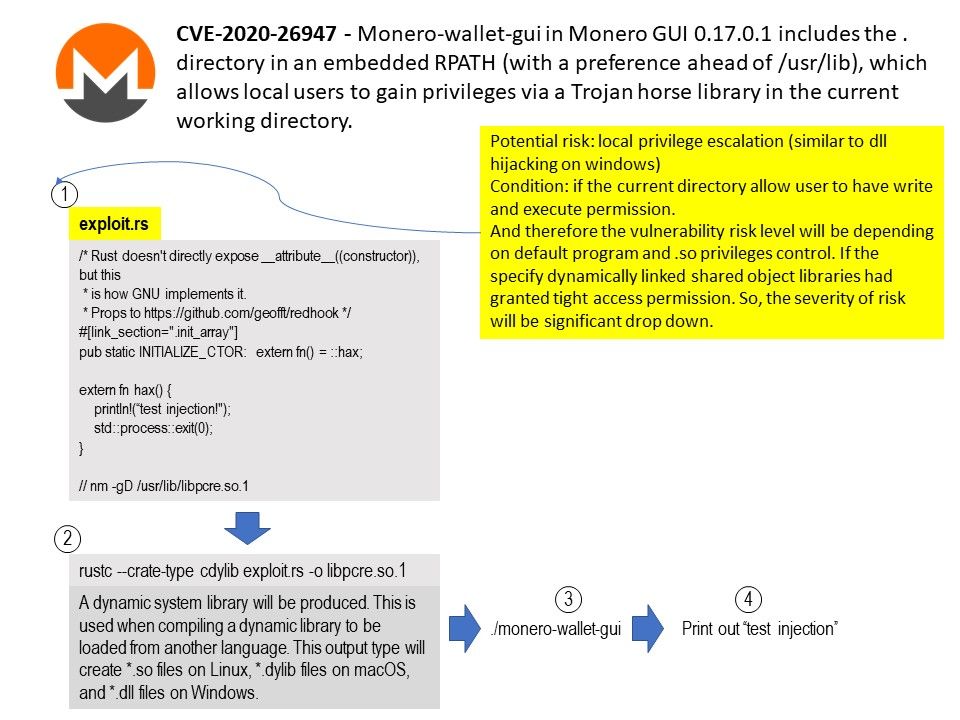
.jpg?width=1920&height=1080&fit=bounds)
Preface: If you like open source application. You should also like the bug he given.
OpenSLP has been ported to a wide variety of systems. For example: Linux (32/64),Windows (32/64),SCO Unix,FreeBSD,Solaris,Tru64,Mac OS X,Darwin,… OpenSLP eliminates the need for users to know the names of network hosts. With OpenSLP, the users need only know the description of the service they want to use. Based on this description, OpenSLP is then able to return the URL of the requested service.
Vulnerability details: A malicious actor residing in the management network who has access to port 427 on an ESXi machine may be able to trigger a use-after-free in the OpenSLP service resulting in remote code execution. To exploit the vulnerability, a malicious user must send a malformed SLP packet to the target system.
Remedy: https://www.vmware.com/security/advisories/VMSA-2020-0023.html
Comment: Regarding to my observation, similar of OpenSLP vulnerability found few years ago. However there is no official patch to do the remediation. Strongly believe that this bug will be exploit by cyber criminal. So it is highly recommended to disable this function.
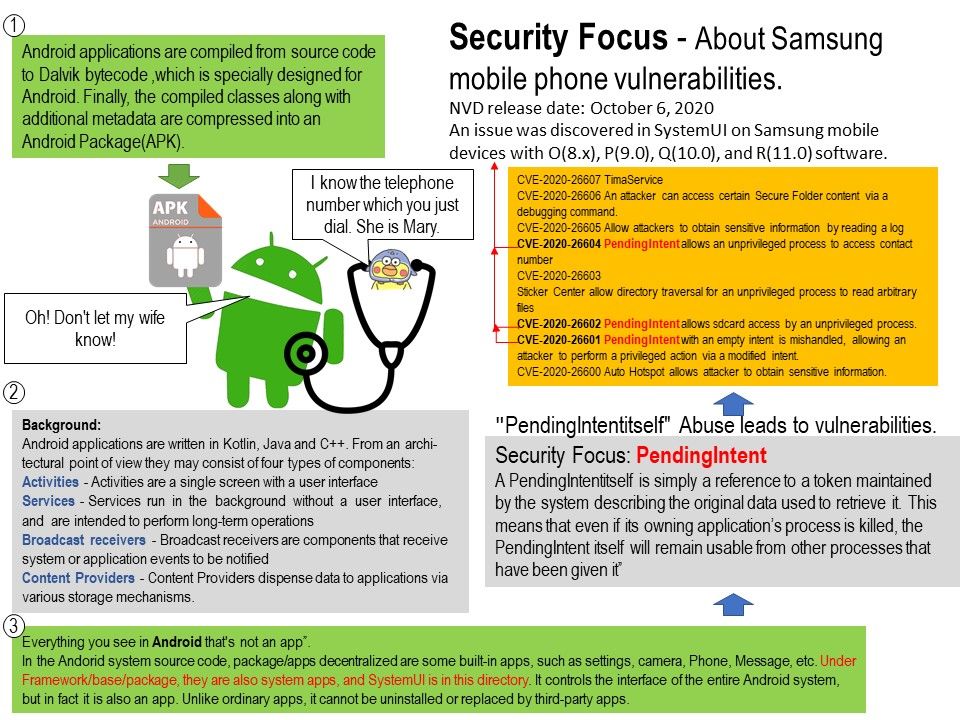
.jpg?width=1920&height=1080&fit=bounds)

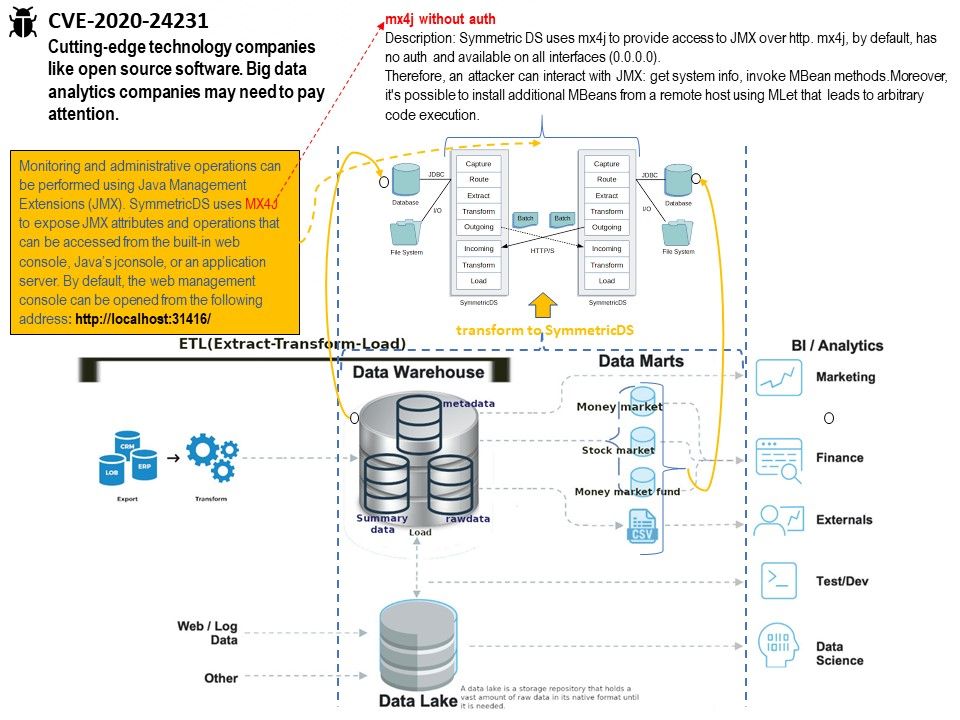
.jpg?width=1920&height=1080&fit=bounds)