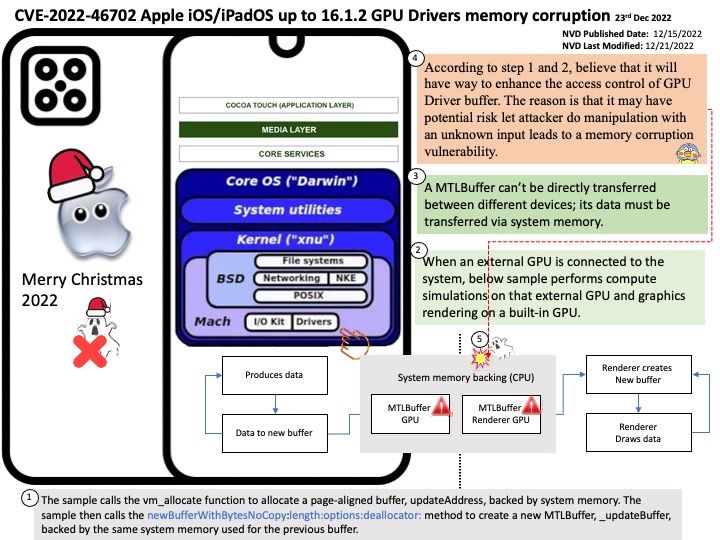
Preface: When an external GPU is connected to the iOS system. Refer to attached diagram , it will perform compute simulations on that external GPU. And thus graphics rendering on a built-in GPU.
According the current GPU design. Do you think is there desugn weakness happen here. For instance, memory access control and access permission.
Background: A MTLBuffer can’t be directly transferred between different devices; its data must be transferred via system memory. Refer to attached diagram. The sample calls the vm_allocate function to allocate a page-aligned buffer, updateAddress, backed by system memory. The sample then calls the newBufferWithBytesNoCopy:length:options:deallocator: method to create a new MTLBuffer, _updateBuffer, backed by the same system memory used for the previous buffer.
Vulnerability details: The issue was addressed with improved memory handling. This issue is fixed in iOS 16.2 and iPadOS 16.2. An app may be able to disclose kernel memory.
As details could not be found in the official announcement. My speculation is shown as below:
According to step 1 and 2 (refer to attached diagram), believe that it will have way to enhance the access control of GPU Driver buffer. The reason is that it may have potential risk let attacker do manipulation with an unknown input leads to a memory corruption vulnerability. As a result, it may be possible for an application to leak kernel memory.
Official announcement: For details, see the link – https://support.apple.com/en-us/HT213530
- Christmas is celebrated to commemorate the birth of Jesus Christ, who Christians believe is the Son of God. Sunday, December 25, 2022 is Christmas. Maybe you don’t have this belief. However, I also wish you Merry Christmas and my best wishes to you and your family.