Preface: Continuing yesterday’s discussion on CVE-2022-44683. Since cve doesn’t provide technical details. This point piqued my interest.
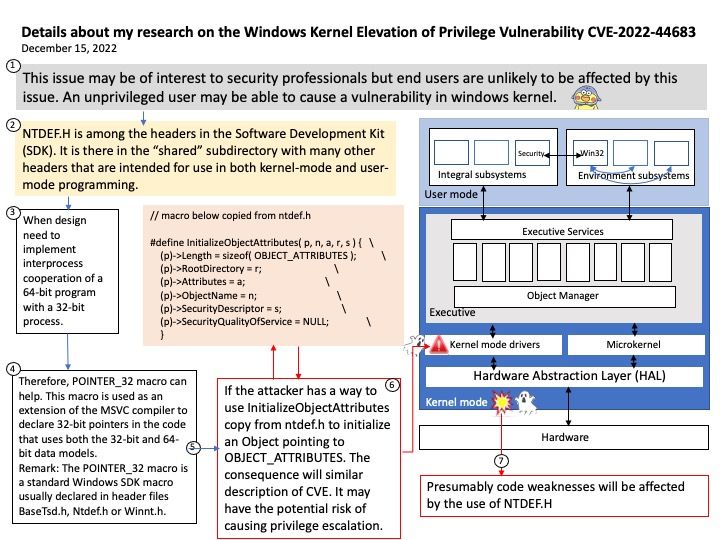
Background: NTDEF(.)H is among the headers in the Software Development Kit (SDK). It is there in the “shared” subdirectory with many other headers that are intended for use in both kernel-mode and user-mode programming.
Ref: NTDEF(.)H is also a ready illustration of how some, if not many, headers in the WDK and SDK are created from some sort of script or master header that extracts from yet more headers. This applies especially to some of the most prominent headers: WDM(.)H, NTDDK(.)H and NTIFS(.)H for kernel-mode programming and WINNT(.)H for user-mode programming.
Vulnerability details: A vulnerability has been discovered and classified as critical in Microsoft Windows (operating system). It’s about an unknown feature of a kernel component. The exact effect of a successful attack is unknown. Furthermore there is no technical details on this vulnerability.
Since the official details do not have information provided. Following details is my speculation. If the attacker has a way to use InitializeObjectAttributes copy from ntdef(.)h to initialize an Object pointing to OBJECT_ATTRIBUTES. The consequence will similar description of CVE. It may have the potential risk of causing privilege escalation.
Official announcement: For details, see the link – CVE-2022-44683: Windows Kernel Elevation of Privilege Vulnerability.