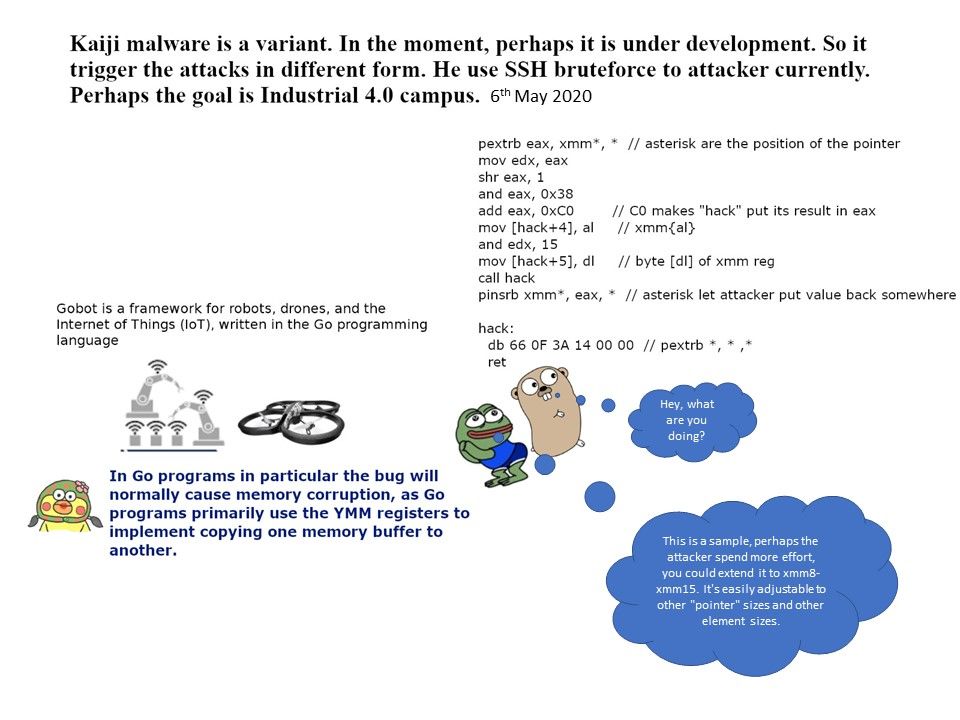
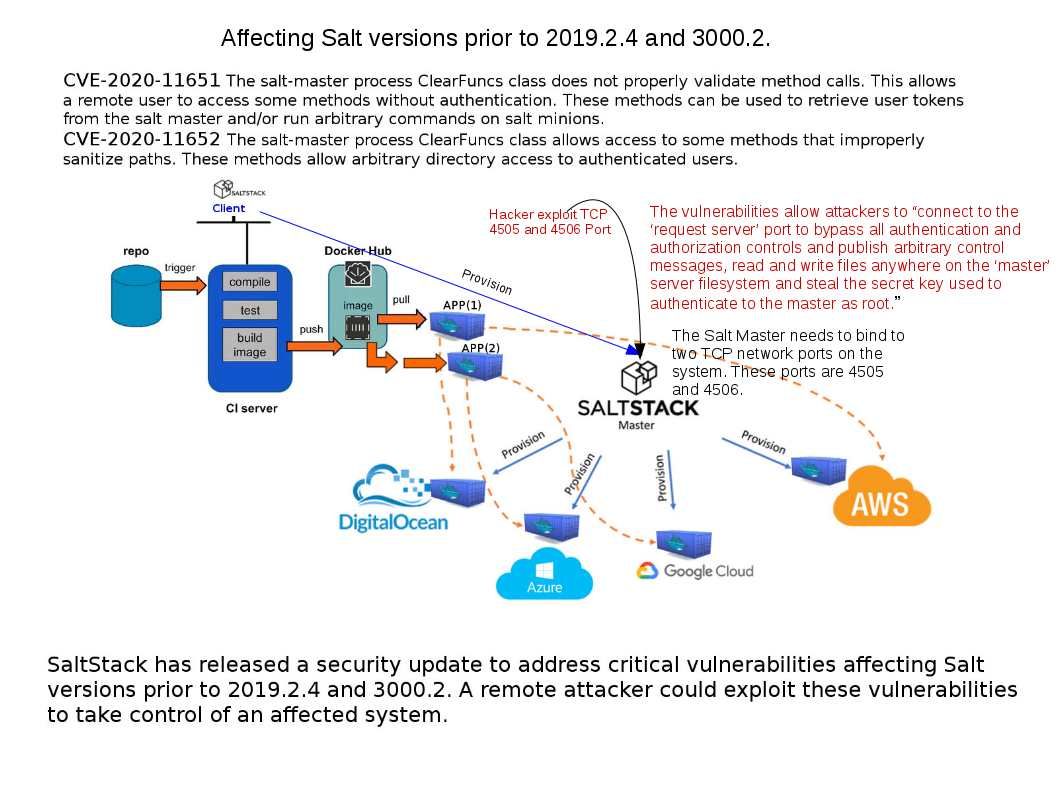
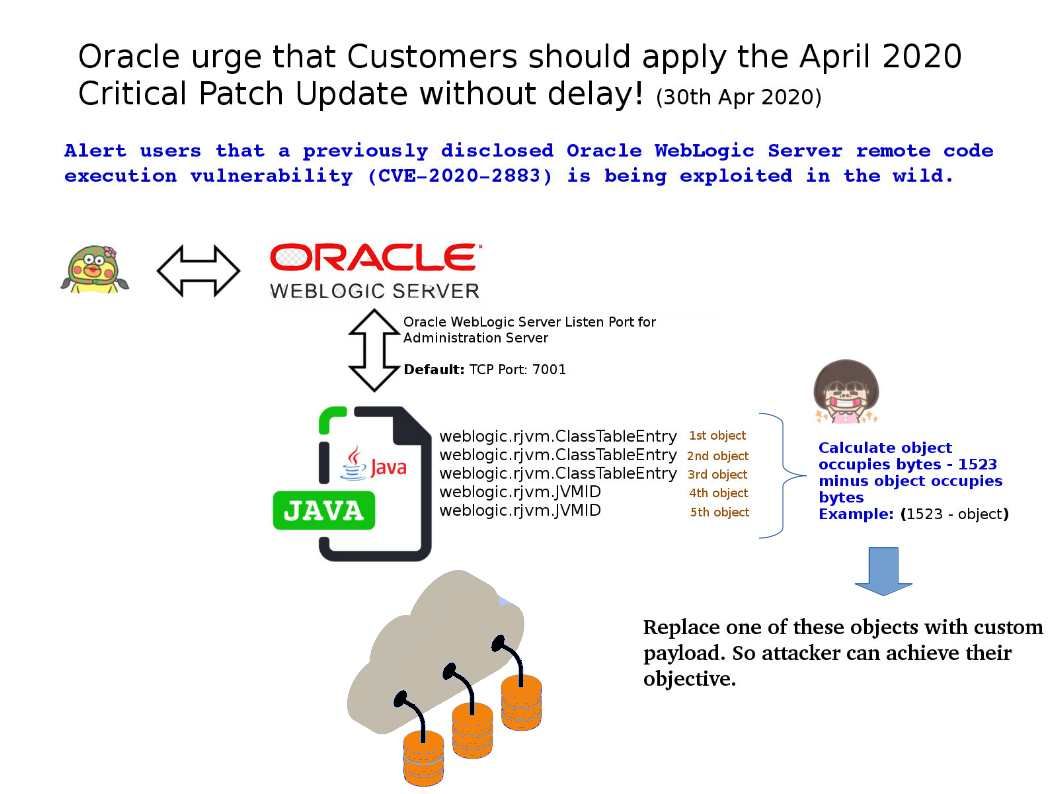
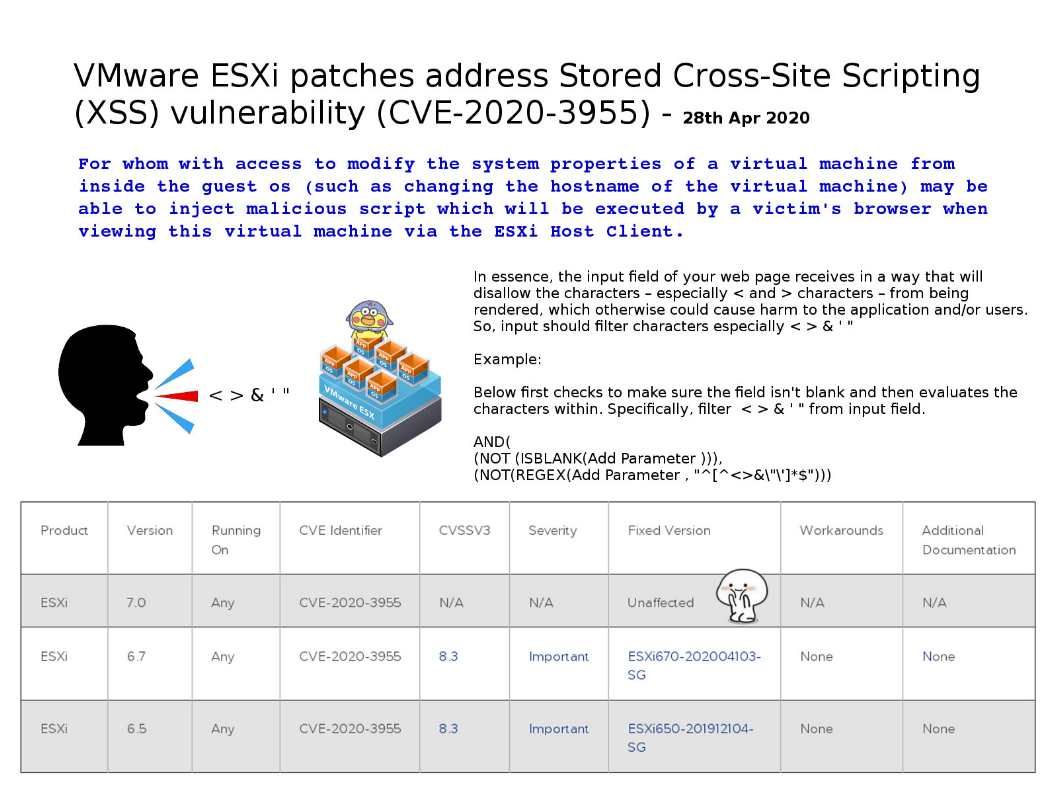
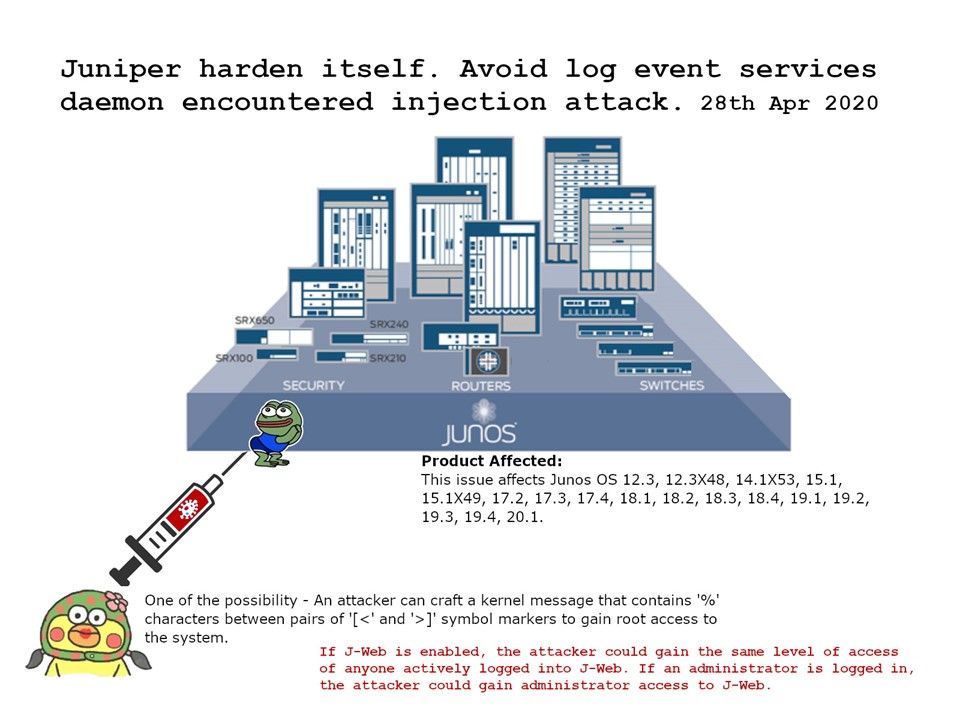
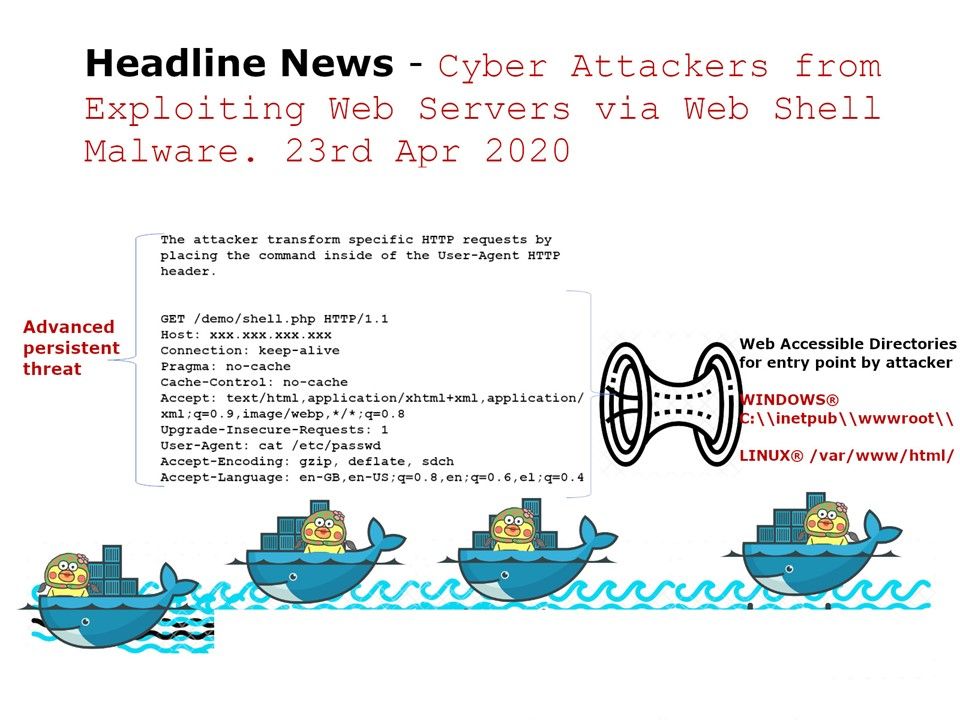
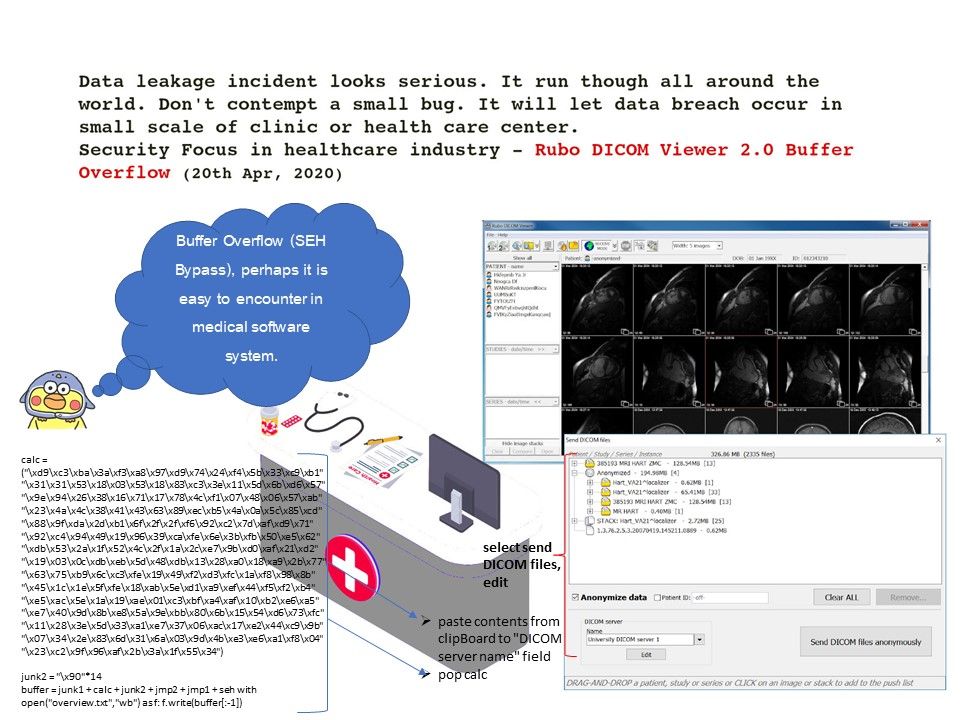
.jpg?width=1920&height=1080&fit=bounds)
Preface: The pandemic virus has killed about 211,000 people. Is it an artificial product or created by nature?
My story can tell: Population growth, it is hard to avoid has a cold. The symptom causes cough & sneeze.However the main problem is the sputum. Perhaps we are the living in modern civilization. However the spit behaviors we seen everywhere. We assumed that the sputum dissolve into soil. However this pollute cycle keep run in a constant cycle into long period of time. So,the unknown matter contains in the soil then transform to a virus storage. The high density populated insect living in the world equivalent man kind population in the earth. It is the ant under the ground. Perhaps the virus or virus being transformation could not kill them. Therefore, ant become couriers. Who is the enemy of ant. Pangolins eat ants. If human being eat the pangolins. As a result, the infection cycle being started.
If you think the above prediction is nonsense. Please read the headlines. How did coronavirus start and where did it come from? Was it really Wuhan’s animal market?
.jpg?width=1920&height=1080&fit=bounds)