Preface: Character combinations consisting of a backslash (\) followed by a letter or by a combination of digits are called “escape sequences.”
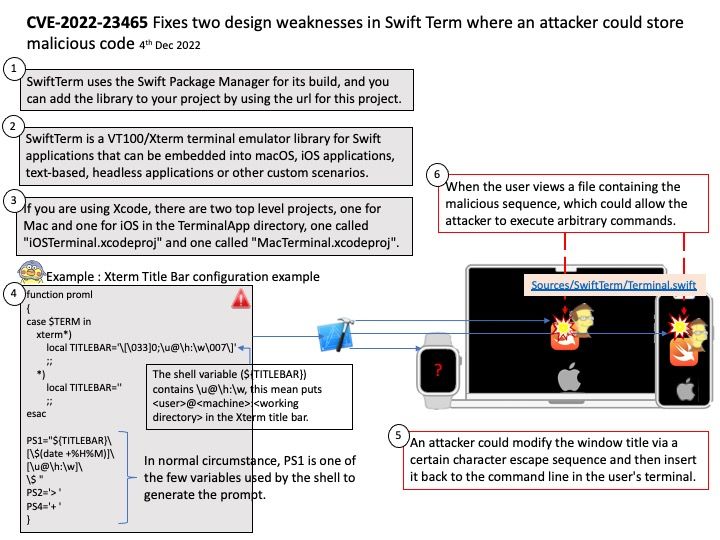
Background: SwiftTerm uses the Swift Package Manager for its build, and you can add the library to your project by using the url for this project.
SwiftTerm is a VT100/Xterm terminal emulator library for Swift applications that can be embedded into macOS, iOS applications, text-based, headless applications or other custom scenarios.
Ref: If you are using Xcode, there are two top level projects, one for Mac and one for iOS in the TerminalApp directory, one called “iOSTerminal.xcodeproj” and one called “MacTerminal.xcodeproj”.
Vulnerability details: Prior to commit a94e6b24d24ce9680ad79884992e1dff8e150a31, an attacker could modify the window title via a certain character escape sequence and then insert it back to the command line in the user’s terminal. When the user views a file containing the malicious sequence, which could allow the attacker to execute arbitrary commands.
Official announcement: Please refer to the link for details – https://nvd.nist.gov/vuln/detail/CVE-2022-23465