Preface: Node[.]js has a built-in WebSocket module, but this module doesn’t provide the functionalities required to build complex real-time applications; this is why Socket[.]io exists.
Socket[.]IO is quite popular and companies like Amazon, Zendesk,……and several others use it to develop robust real-time applications. It one of the most powerful JavaScript frameworks on GitHub, and most depended-upon NPM (Node Package Manager) module.
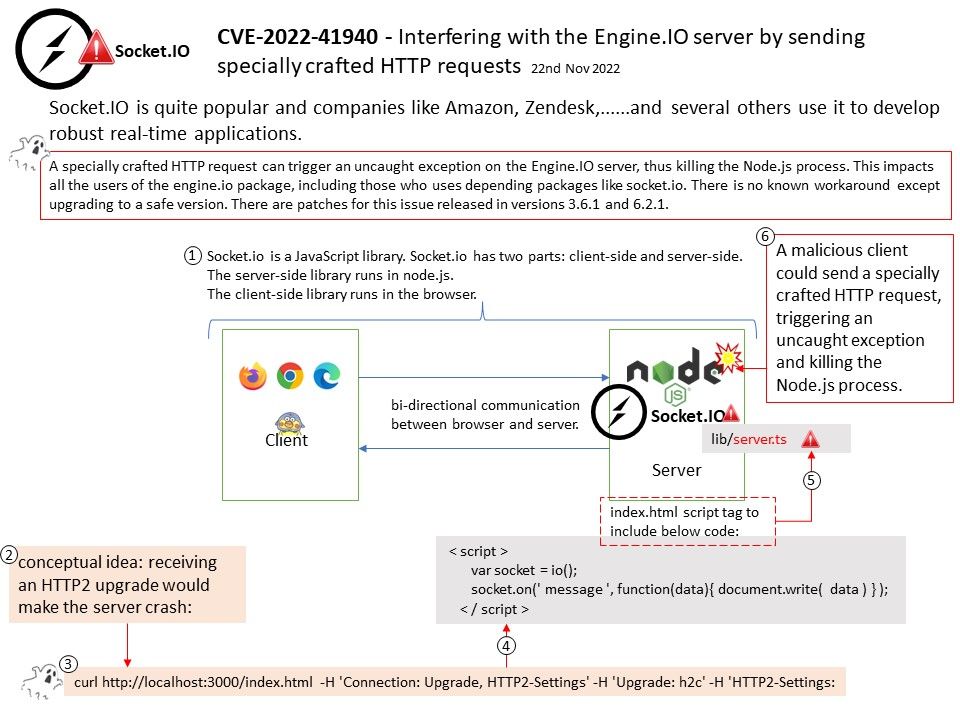
Background: Socket[.]io is a JavaScript library. It is a way to communicate between a client and a server. It allows real-time data flow. It is bi-directional communication, means we can flow data in both directions:
- Client to Server
- Server to Client
engine.io is a lower level library than socket.io. Engine is to Socket[.]IO what Connect is to Express. If you want the lower level abstraction, use engine[.]io. If you want a websocket abstraction, keep using socket[.]io.
Remark: engine[.]io is of more interest to you if you’re building a library/framework on top of socket[.]io.
Vulnerability details: A specially crafted HTTP request can trigger an uncaught exception on the Engine[.]IO server, thus killing the Node[.]js process. This impacts all the users of the engine[.]io package, including those who uses depending packages like socket[.]io.
A malicious client could send a specially crafted HTTP request, triggering an uncaught exception and killing the Node[.]js process:
Solution: There is no known workaround except upgrading to a safe version. There are patches for this issue released in versions 3.6.1 and 6.2.1.
Official announcement: Please refer to the link for details – https://github.com/advisories/GHSA-r7qp-cfhv-p84w