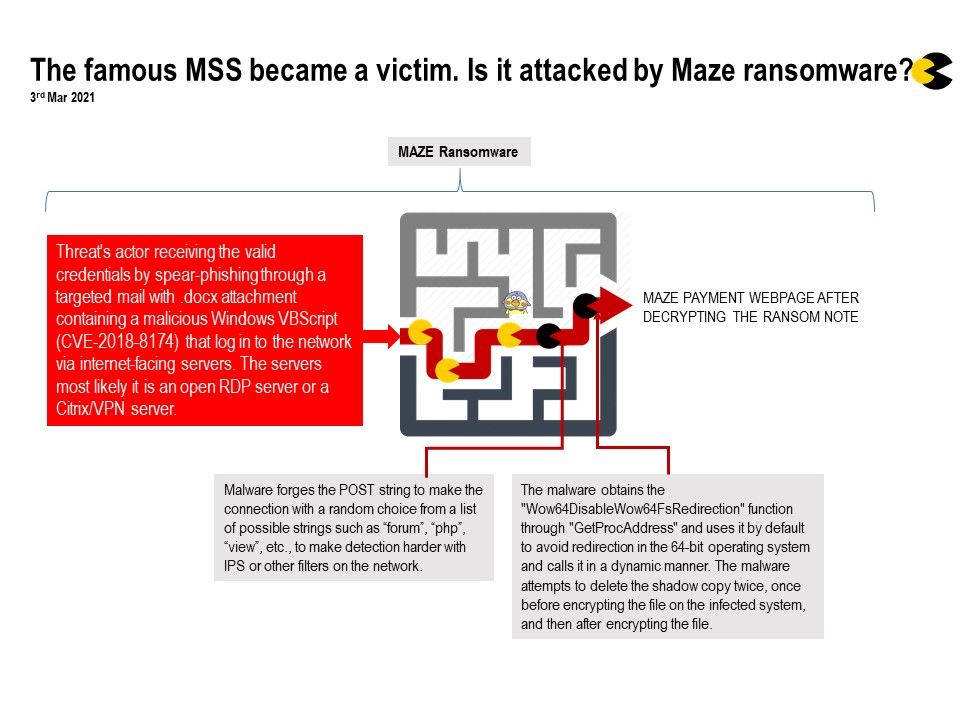
Preface: There is a registry key in your system that can be set to prevent certain applications from running, including security software.
Background: If the software developer creates a buffer and reserves 1024 bytes then tries to copy anything more than 1023 bytes (computers start counting at 0 remember) it will overflow out from the buffer and overwrite other memory locations on the stack.
When problem occurred. It will overwrite is the saved EBP (base pointer) and then the saved EIP (saved return address) and then the function parameters.
The function gets called it first creates a new Stack Frame. Then pushes the base pointer onto the stack so that it can retrieve it later and then it pushes the return address (saved EIP) onto the stack, this is so that when the function finishes it can return to the previous function that called it.
Reference: If interested to know the detail, you can read the details through the link – https://malvuln.com/advisory/8936c97e99799809812fa740076a2d7f.txt
It was interested that the Portable executor not new. The historical record shown that the first submission of PE file is on 2016.
This malware/Torjan activities keep going on for 6 years.


.jpg?width=1920&height=1080&fit=bounds)