Preface: When you know there is a vulnerability on the tool. Perhaps, your security awareness level will decrease. Maybe that makes sense, if you don’t use the tool, the risk is nullified.
But sometimes it’s exceptions and coincidences. Something similar happens in the Kubernetes environment as well.
Background: Ephemeral containers differ from other containers in that they lack guarantees for resources or execution, and they will never be automatically restarted, so they are not appropriate for building applications.
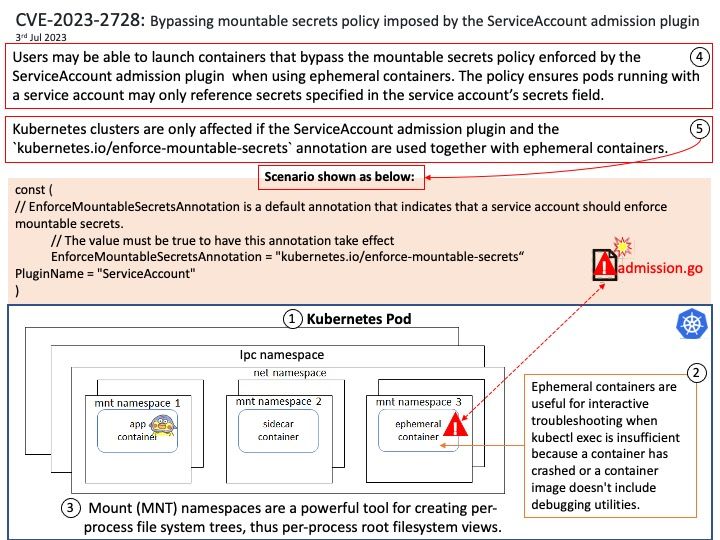
Ephemeral containers are useful for interactive troubleshooting when kubectl exec is insufficient because a container has crashed or a container image doesn’t include debugging utilities.
In Kubernetes, namespaces provides a mechanism for isolating groups of resources within a single cluster.
- IPC namespaces contain a specific kind of IPC objects known as “POSIX IPC” and “SysV IPC” – shared memory areas, message queues, and semaphores.
- Mount (MNT) namespaces are a powerful tool for creating per-process file system trees, thus per-process root filesystem views.
Linux maintains a data structure for all the different filesystems mounted on the system. This structure is a per-process attribute and also per-namespace.
Vulnerability details: Users may be able to launch containers that bypass the mountable secrets policy enforced by the ServiceAccount admission plugin when using ephemeral containers. The policy ensures pods running with a service account may only reference secrets specified
in the service account’s secrets field. Kubernetes clusters are only affected if the ServiceAccount admission plugin and the kubernetes[.]io/enforce-mountable-secrets annotation are used together with ephemeral containers.
Official announcement: For details please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-2728