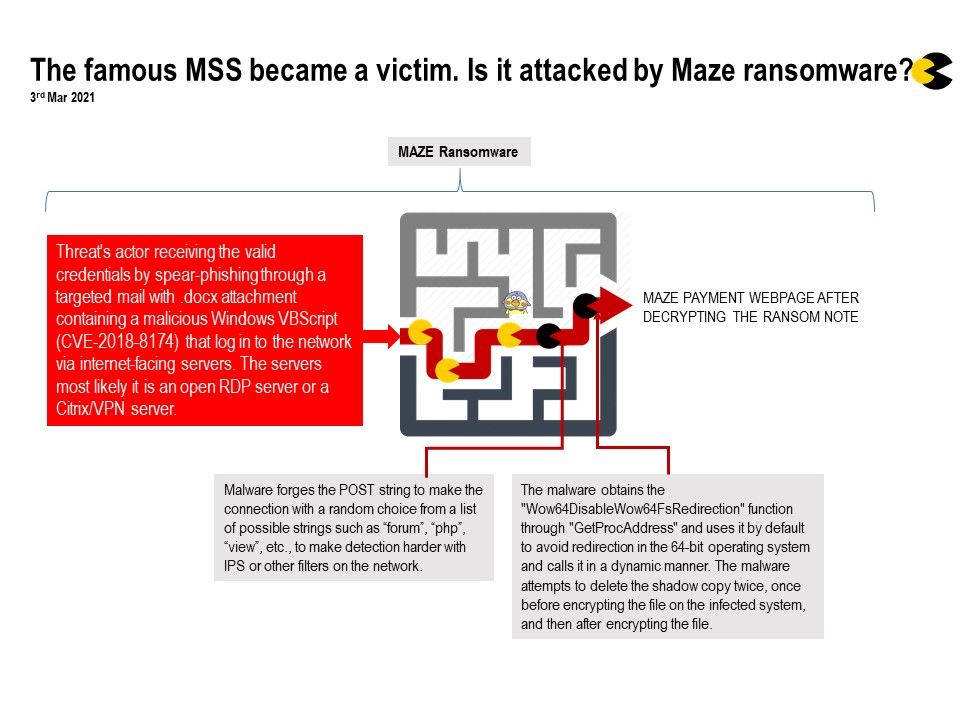
Background: On July last year (2020), Secret Service warned that since MSPs service a large number of organizations at the same time
through remote administration tools, cyber criminals are specifically targeting MSPs to conduct their attacks at scale to infect multiple companies through the same vector.
Incident details: CompuCom began contacting customers to alert them that their company system facilities had been encountered cyber attack. However, the details did not mentioned what type of cyber attack occurred . An unofficial new let the people know perhaps it was ransomware.
Reference: Maze ransomware relies on CVE-2018-8174. This ransomware aim to receive the user credentials before proceed Reconnaissance. By prediction, the attacker collecting the user credential through guessing default/weak passwords or spear-phishing through a targeted mail with a .docx attachment containing a malicious macro. When an attacker compromises the system and uses the vulnerability to escalate privileges. Upon completion, it will perform ransomware encryption operations.
Headline News: CompuCom Issues Statement Regarding Malware Incident – https://finance.yahoo.com/news/compucom-issues-statement-regarding-malware-212400889.html