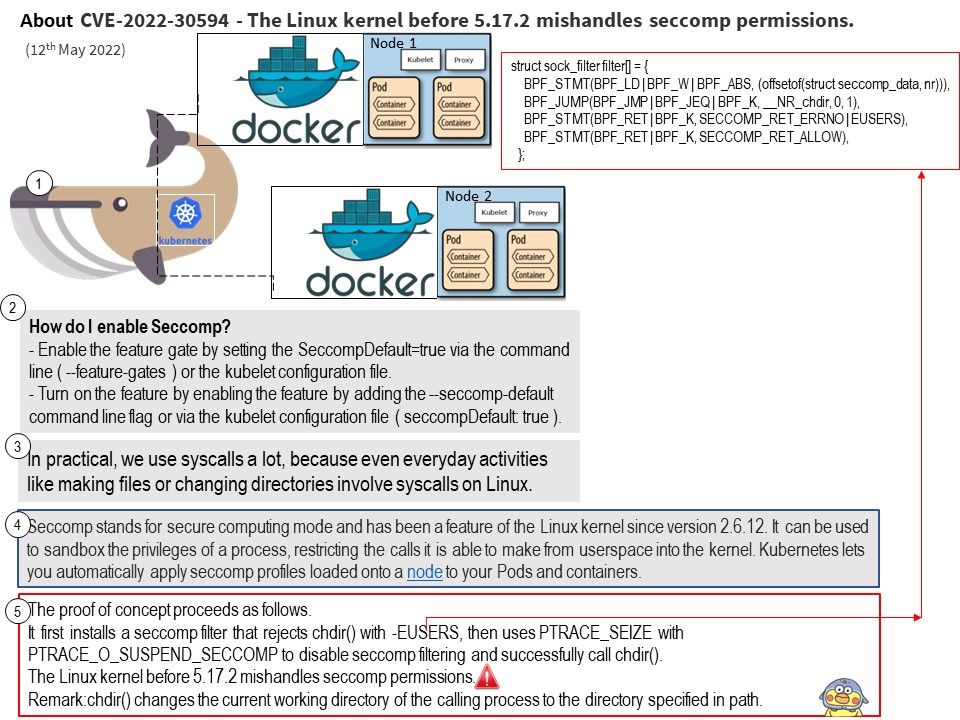
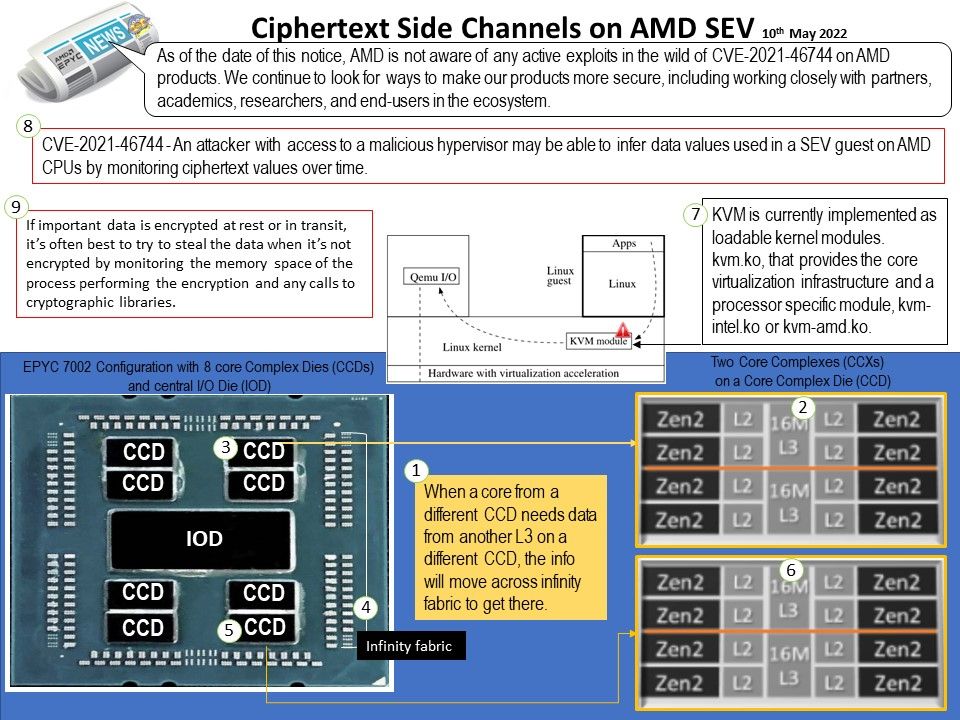
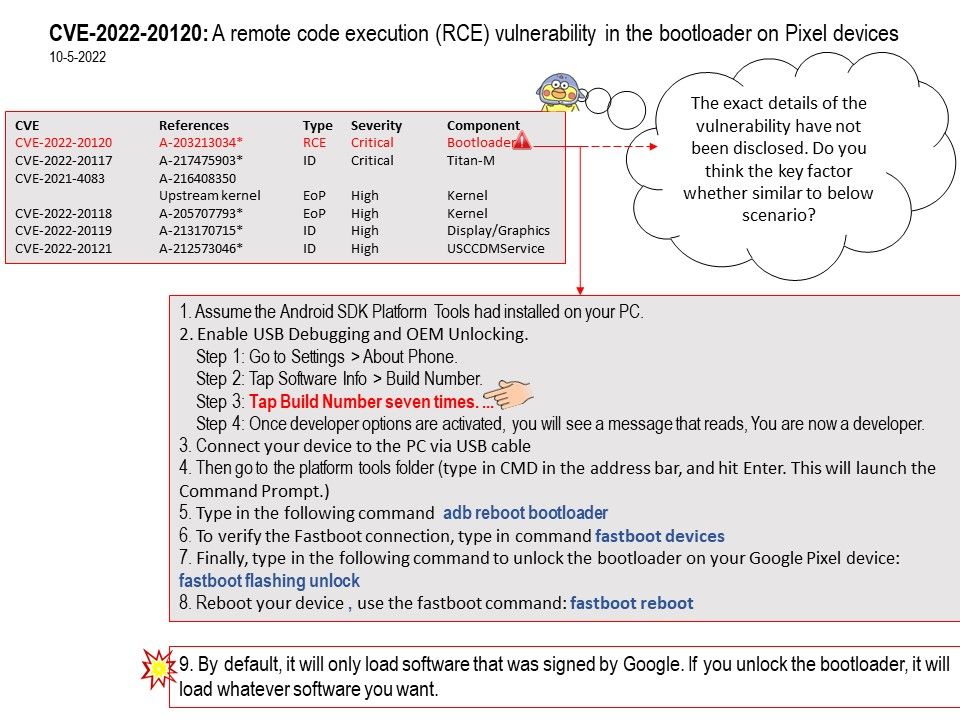
Preface: There’s no needle with both ends pointed. The baseline requirements of ETSI EN 303 645 specifically have timely, automatic updates as one of its requirements. So the first step in best practice is to ensure that software updates can be delivered to your system, preferably automatically and over-the-air (OTA).
Background: Traditionally, U-Boot is the most popular boot loader in linux based embedded devices. Das U-Boot is an open-source, primary boot loader used in embedded devices to package the instructions to boot the device’s operating system kernel.
Numerous features and modes of operation can be selected by adding definitions to the board-configuration file. Below example is a partial configuration header file.
define CONFIG_COMMANDS (CONFIG_CMD_DFL & ~CFG_CMD_NFS)
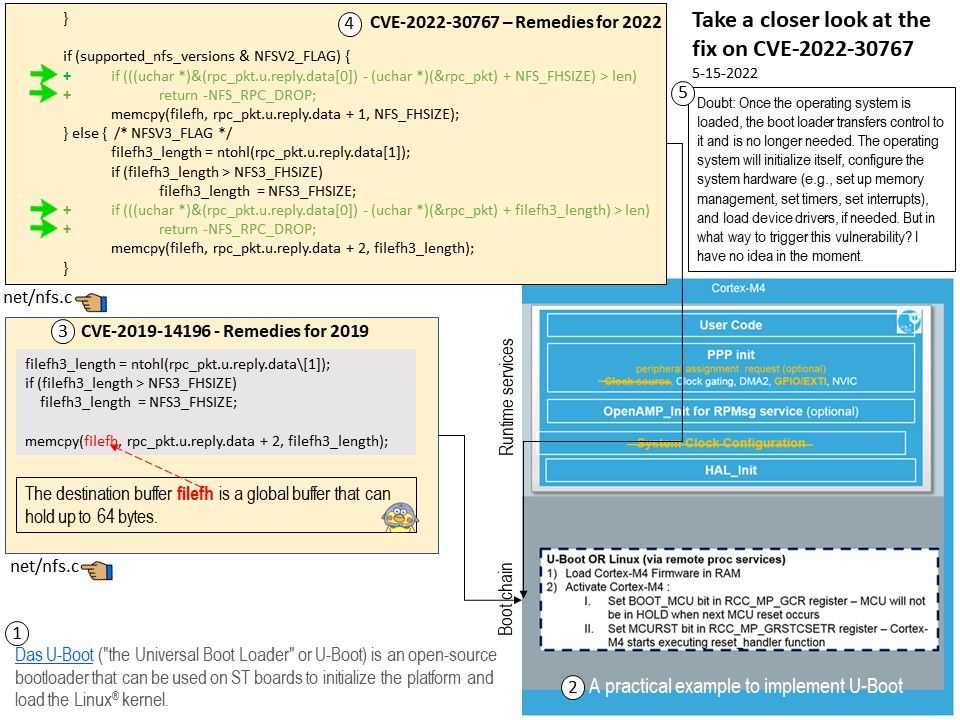
Vulnerability details: An issue was discovered in Das U-Boot through 2019.07. There is an unbounded memcpy with a failed length check at nfs_lookup_reply.
nfs_lookup_reply in net/nfs.c in Das U-Boot through 2022.04 (and through 2022.07-rc2) has an unbounded memcpy with a failed length check, leading to a buffer overflow.
Remark: When you call memcpy you need to pass it two pointers, and the size of the object to copy.
Remedy: Please refer to the link for details – https://github.com/u-boot/u-boot/commit/5d14ee4e53a81055d34ba280cb8fd90330f22a96
Doubt: Once the operating system is loaded, the boot loader transfers control to it and is no longer needed. The operating system will initialize itself, configure the system hardware (e.g., set up memory management, set timers, set interrupts), and load device drivers, if needed.
If there is buffer overflow vulnerability happen in a bootloader. My idea is that the risk rating or impact all depends on the device whether accepted remote process service or accept Updating the Bootloader Over-the-Air (OTA).
In theory, in the out-of-bounds write vulnerability, the software writes data past the end, or before the beginning, of the intended buffer, which can result in the corruption of data, a crash, or code execution.
But in what way to trigger this vulnerability? I have no idea in the moment.
.jpg)
.jpg)
.jpg)