Preface: Fuchsia is an IoT; first OS means OS for your fridge, RaspberryPi, car, TV, etc.
Background: Zircon is the core platform that powers the Fuchsia OS. Zircon is composed of a microkernel (source in kernel/…) as well as a small set of userspace services, drivers, and libraries (source in system/…) necessary for the system to boot, talk to hardware, load userspace processes and run them, etc. Fuchsia builds a much larger OS on top of this foundation. One benefit of the microkernel approach is ease of extending the operating system. All new services are added to user space and consequently do not require modification of the kernel. Fuchsia is an open-source capability-based operating system developed by Google. As a general purpose operating system, Fuchsia is designed to power a diverse ecosystem of hardware and software.
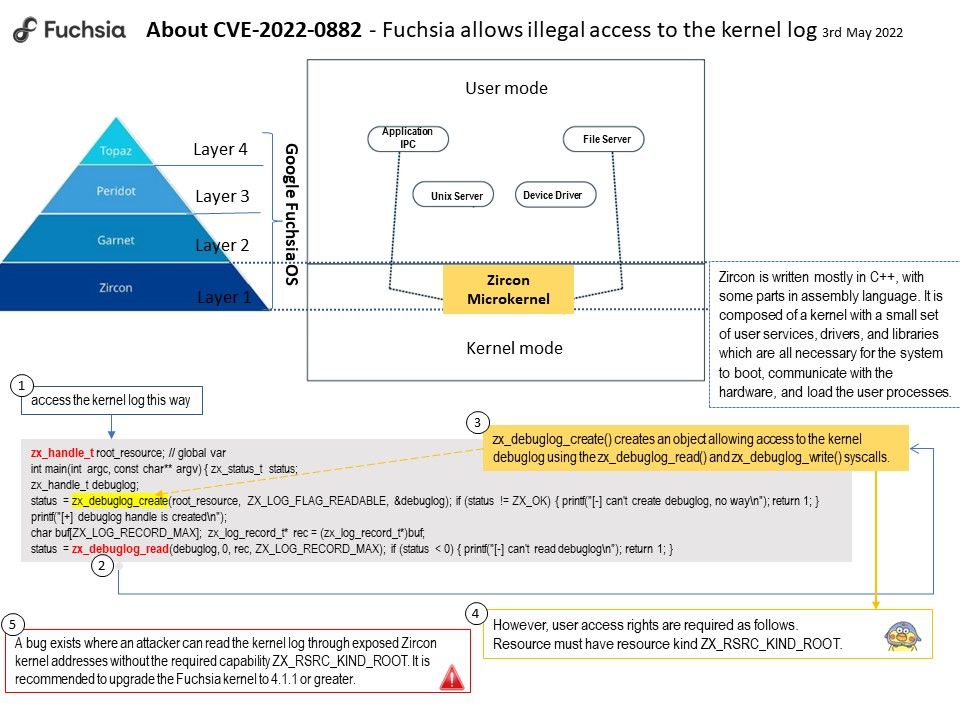
Vulnerability Details: A bug exists where an attacker can read the kernel log through exposed Zircon kernel addresses without the required capability ZX_RSRC_KIND_ROOT.Fuchsia allows illegal access to the kernel log. This exposes Zircon kernel addresses and other sensitive information to components that do not have the required functionality. It is a security issue. Please refer to the link for details – https://bugs.fuchsia.dev/p/fuchsia/issues/detail?id=94740
Remedy: It is recommended to upgrade the Fuchsia kernel to 4.1.1 or greater.