Preface: Traditionally, the only way to enable that syscall in Linux was to enable CONFIG_CHECKPOINT_RESTORE. However, since Linux v5.10.20 and v5.11.3, a new CONFIG_KCMP has been added to Linux to allow enabling sys_kcmp without having to enable CONFIG_CHECKPOINT_RESTORE!
Background: Secure computing mode ( seccomp ) is a Linux kernel feature. You can use it to restrict the actions available within the container. The seccomp() system call operates on the seccomp state of the calling process. You can use this feature to restrict your application’s access. Syscalls are system calls, and they’re the way that you can make requests from user space into the Linux kernel.
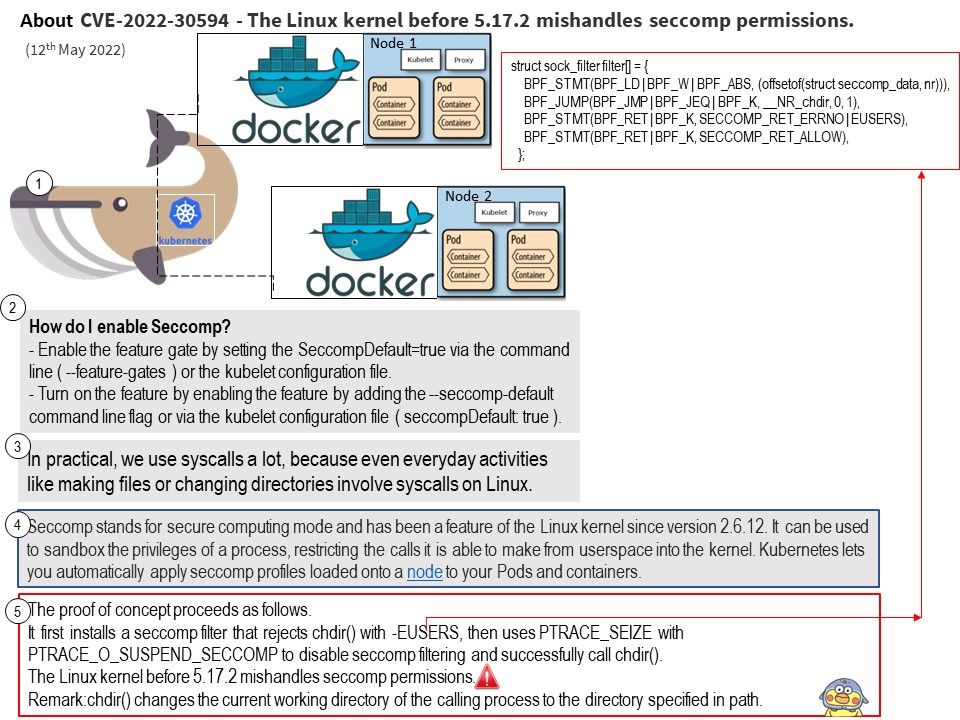
In practical, we use syscalls a lot, because even everyday activities like making files or changing directories involve syscalls on Linux.
Vulnerability details: The Linux kernel before 5.17.2 mishandles seccomp permissions. The PTRACE_SEIZE code path allows attackers to bypass intended restrictions on setting the PT_SUSPEND_SECCOMP flag.
Vulnerability found permission checks were done on the PTRACE_SETOPTIONS path. However the PTRACE_SEIZE code path allows attackers to bypass intended restrictions on setting the PT_SUSPEND_SECCOMP flag.
The vulnerability move the permissions checks out into a helper function and let both ptrace_attach() and ptrace_setoptions() call it.
Official announcement (For details, please refer to the official announcement) – https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=ee1fee900537b5d9560e9f937402de5ddc8412f3