Preface: Google Pixel is a brand of consumer electronic devices developed by Google that run either Chrome OS or the Android operating system. The Pixel brand was introduced in February 2013 with the first-generation Chromebook Pixel. The Pixel line includes laptops, tablets, and smartphones, as well as several accessories.
Background: The Google Pixel is one of the smartphones on the market today. The Google Pixel also works with digital camera products.
How do you identify a Pixel device? The simple way is to go through the settings menu. → Settings → About Phone → Model Number. The display will tell you the make and model number of your device alongside the IMEI Number, serial number and also the version of Android you are running.
How do I get into bootloader? Follow below steps:
- Ensure the phone is turned off.
- Press and hold the VOLUME DOWN button.
- Press the POWER button.
- Continue to hold VOLUME DOWN until the Download mode is displayed.
- Press VOLUME DOWN to go to Reboot to bootloader.
- Press the POWER button.
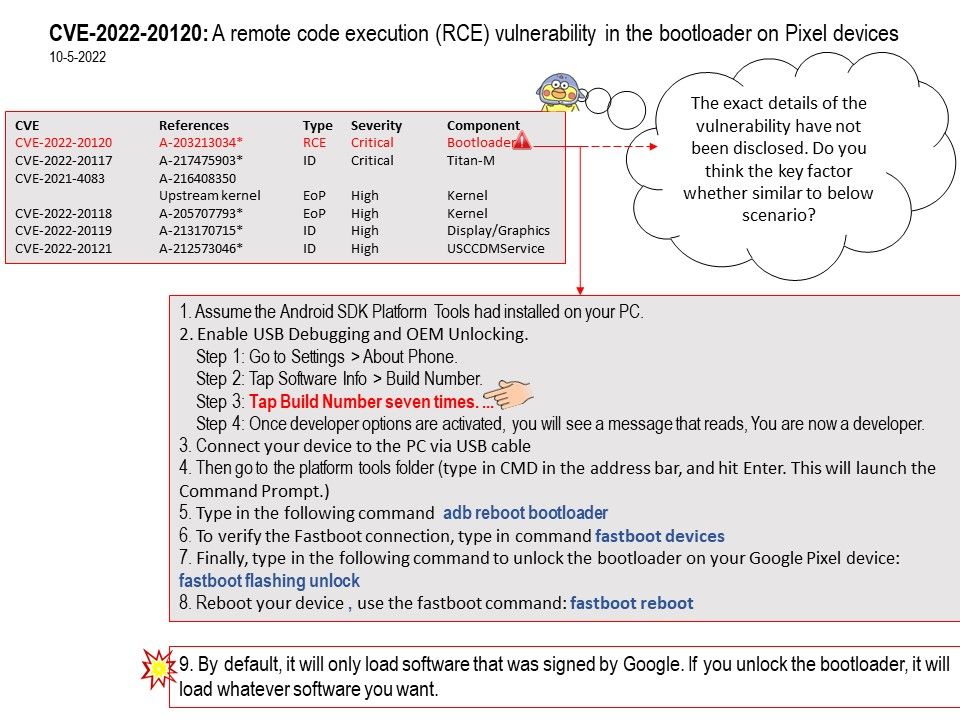
Vulnerability details: With just a few minutes of physical access and a USB cable, attackers can silently and invisibly compromise unpatched devices. The exact details of the vulnerability have not been disclosed. Do you think the key factor whether similar to steps displayed in attached diagram?
Official announcement (Pixel Update Bulletin—May 2022): Please refer to the link for details – https://source.android.com/security/bulletin/pixel/2022-05-01#pixel