Preface: KVM (Kernel based Virtual Machine) is an open source Linux kernel virtualization infrastructure2 which relies on the hardware virtualization technologies, fully integrated in the Linux kernel. Its first version was introduced in the 2.6.20 Linux kernel tree (released in February 2007). KVM developers are primarily funded by a technology startup called Qumranet, now owned by RedHat. Developers had an original approach. Instead of creating major portions of an operating system kernel themselves, they choose to use the Linux kernel itself as a basis for a hypervisor.
KVM stands for Kernel-based Virtual Machine. Being an open-source virtualization software that’s embedded into Linux, KVM does two things:
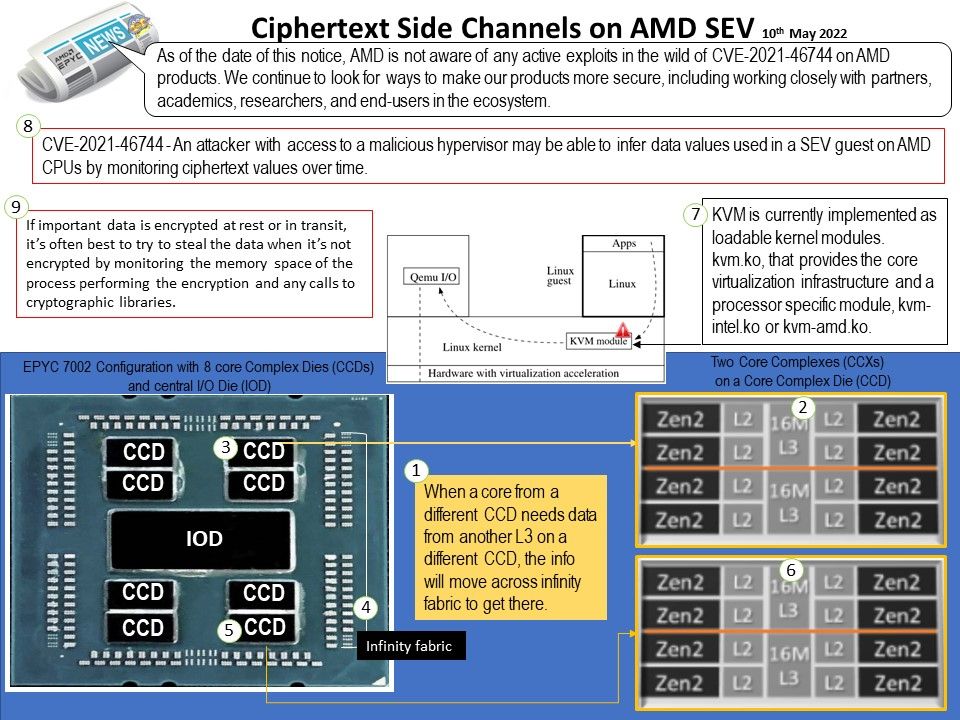
- Makes Linux a hypervisor
- Enables Linux to run multiple, isolated virtual environments
KVM initially supported x86 platform processors and was subsequently ported to S/390, PowerPC, and IA-64 platforms
Background: AMD EPYC 7002 Processors – A dual-socket AMD EPYC workstation or server is idea for compute intensive tasks such as high performance computing (HPC) and artificial intelligence (AI) applications thanks to their huge memory bandwidth, memory capacity and outstanding I/O. AMD EPYC Processors with improved execution pipelines, higher clock rates, and up to 4x the shared Level 3 cache. A Level 3 (L3) cache is a specialized cache that that is used by the CPU and is usually built onto the motherboard and, in certain special processors, within the CPU module itself.
The AMD EPYC 7002 Series Processor is the latest generation of the AMD64 System-on-Chip (SoC) processor family. It is based on the Zen 2 microarchitecture introduced in 2019, supporting up to 64 cores (128 threads) and 8 memory channels per socket. AMD’s CCD is actually an abbreviation of Core Chiclet Die.The Zen 2 architecture processor is not a large core packaged together, but is divided into two parts: the CCD core and the I/O core, of which the CCD core is a pure computing The core contains two CCXs, that is, each CCD has 8 cores and 16 threads.
Vulnerability details: An attacker with access to a malicious hypervisor may be able to infer data values used in a SEV guest on AMD CPUs by monitoring ciphertext values over time.
Speculation based on vulnerabilities: If important data is encrypted at rest or in transit, it’s often best to try to steal the data when it’s not encrypted by monitoring the memory space of the process performing the encryption and any calls to cryptographic libraries.
Official announcement: AMD provides preventive and corrective controls, please refer to the link for more details. https://www.amd.com/en/corporate/product-security/bulletin/amd-sb-1033
My comment: Due to this design flaw, the vendor (AMD) recommend to do a series of preventive and corrective control. In my personal point of view, the first step should dicuss with system architect and software development how to integrate below concept of Linux clear cache command into the work flow.
Drop all caches – Below Linux command:
sync; echo 3 > /proc/sys/vm/drop_caches