Preface: If you look into a Mainframe computer system, you will find Brocade SANS storage made use of Ficon connection. As times goes by, Hi-end supercomputer system still using this solution.
Furthermore, Brocade products not limit the usage in supercomputer. The Fibre Channel storage networking and management solution are expanded to cloud computing. Becuase the Fibre Channel storage networking solutions are the most trusted.
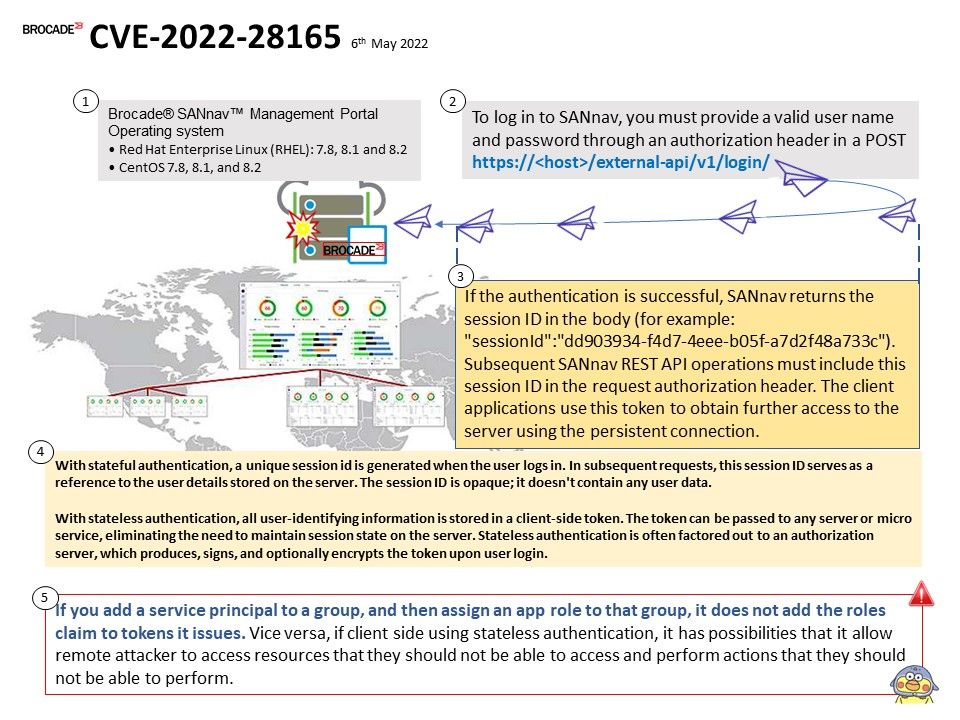
Background: SANnav Management Portal supports an application programming interface (API) for managing Brocade® storage area network (SAN) fabrics. The REST API provides you with a web-services interface for accessing the SANnav Management Portal server system. The REST APIs are organized into various services, such as Login, Discovery,FCR, Fault, Inventory, and Northbound Streaming. You can use the REST API to build your own SANnav clients.
Vulnerability details: A vulnerability in the role-based access control (RBAC) functionality of the Brocade SANNav before 2.2.0 could allow an authenticated, remote attacker to access resources that they should not be able to access and perform actions that they should not be able to perform. The vulnerability exists because restrictions are not performed on Server side to ensure the user has required permission before processing requests.
Important notice – If you add a service principal to a group, and then assign an app role to that group, it does not add the roles claim to tokens it issues. Vice versa, if client side using stateless authentication, it has possibilities that it allow remote attacker to access resources that they should not be able to access and perform actions that they should not be able to perform.
Reference (see below):
- With stateful authentication, a unique session id is generated when the user logs in. In subsequent requests, this session ID serves as a reference to the user details stored on the server. The session ID is opaque; it doesn’t contain any user data.
- With stateless authentication, all user-identifying information is stored in a client-side token. The token can be passed to any server or micro service, eliminating the need to maintain session state on the server. Stateless authentication is often factored out to an authorization server, which produces, signs, and optionally encrypts the token upon user login.
Affected Products – Brocade SANnav before 2.2.0
Remedy: Fixed in Brocade SANnav 2.2.0
Official announcement: Please refer to the link for details – https://www.broadcom.com/support/fibre-channel-networking/security-advisories/brocade-security-advisory-2022-1844
Additional details: According to above principles. One of the remedy solution can be used to implement claim-based authorization. App roles can be assigned to a user or a group of users. App roles can also be assigned to the service principal for another application, or to the service principal for a managed identity.