Preface: ezXML – XML Parsing C Library version 0.8.5 ezXML is a C library for parsing XML documents inspired by simpleXML for PHP.
According to the statistis by W3Techs, PHP is use by 79.2% of all websites primary server-side programming language.
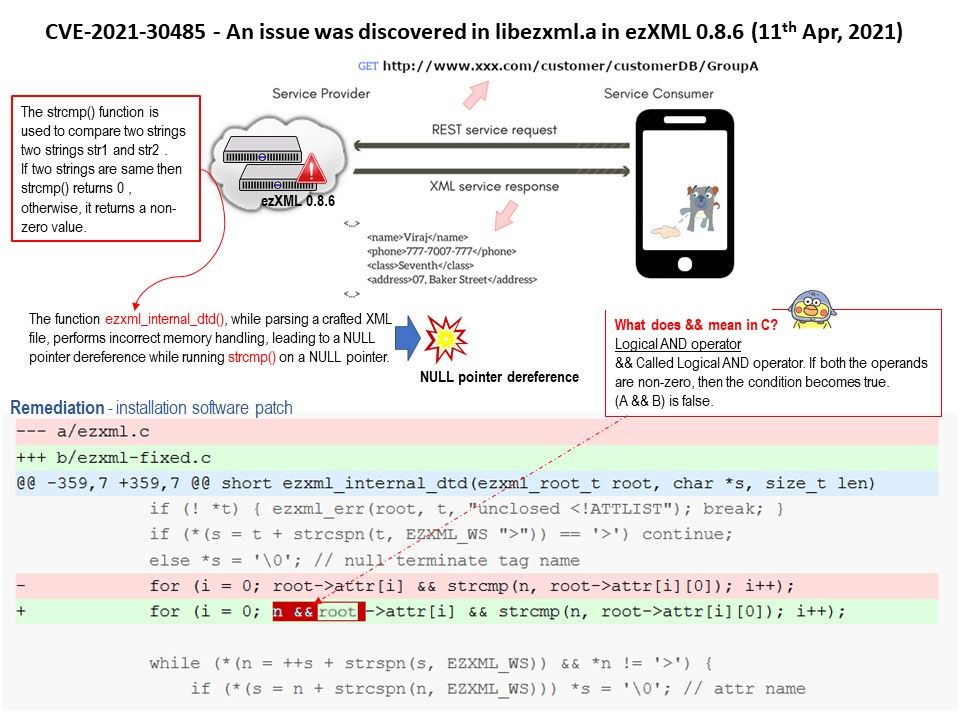
Background: In an XML file, there are both tags and text. The tags provide the structure to the data. The text in the file that you wish to store is surrounded by these tags, which adhere to specific syntax guidelines. XML parser is a software library or a package that provides interface for client applications to work with XML documents. It checks for proper format of the XML document and may also validate the XML documents.
Vulnerability details: An issue was discovered in libezxml.a in ezXML 0.8.6. The function ezxml_internal_dtd(), while parsing a crafted XML file, performs incorrect memory handling, leading to a NULL pointer dereference while running strcmp() on a NULL pointer.
Consequences: Running a program that contains a NULL pointer dereference generates an immediate segmentation fault error. This defect may manifest itself as a program crash, or be transformed into a software exception that can be caught by program code.
For more details, please refer to link https://nvd.nist.gov/vuln/detail/CVE-2021-30485