Preface: RIOT is a low-memory operating system suitable for IoT devices. It is an open source software released under LGPLv2.
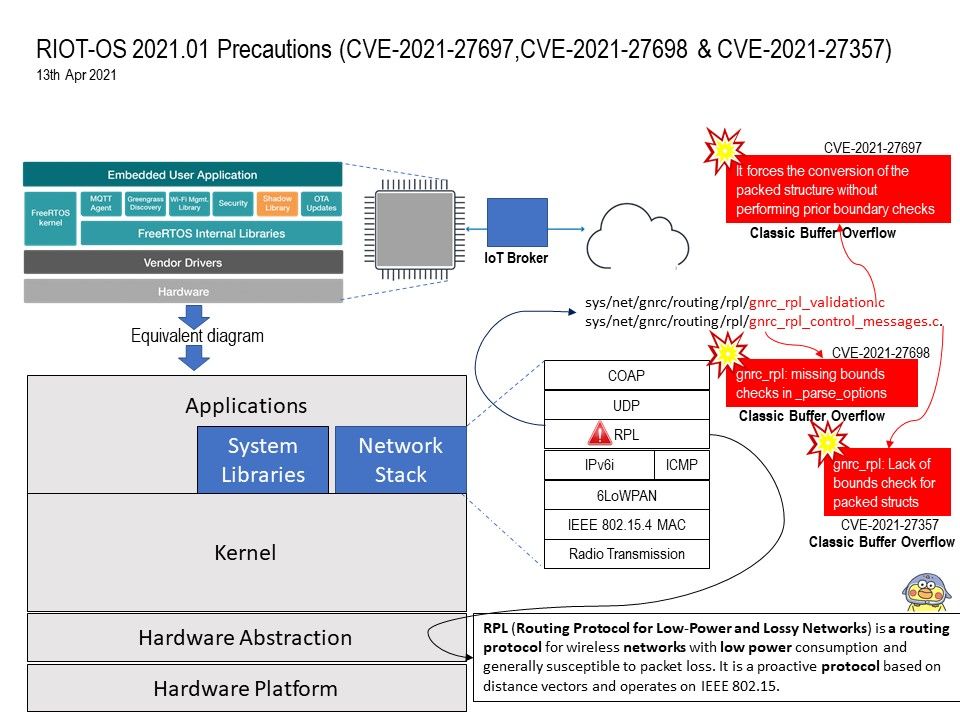
Background: RPL (Routing Protocol for Low-Power and Lossy Networks) is a routing protocol for wireless networks with low power consumption and generally susceptible to packet loss. It is a proactive protocol based on distance vectors and operates on IEEE 802.15.
Vulnerability details: RPL is a distance vector routing protocol based on the construction of a directed acyclic graph (DAG). Existing Routing Protocols for Low Power and Lossy Networks (RPL) are considered lightweight and secure routing protocols for IoT devices, which offer a slight safeguard against innumerable forms of RPL routing attacks. Unfortunately of design weakness. There are total of 3 potential risk of vulnerabilities was found in RPL function. All the vulnerability will be trigger buffer overflow. For more details, please refer to the link below:
CVE-2021-27697 RIOT-OS 2021.01 contains a buffer overflow vulnerability in sys/net/gnrc/routing/rpl/gnrc_rpl_validation.c
through the gnrc_rpl_validation_options() function. – https://nvd.nist.gov/vuln/detail/CVE-2021-27697
CVE-2021-27698 RIOT-OS 2021.01 contains a buffer overflow vulnerability in /sys/net/gnrc/routing/rpl/gnrc_rpl_control_messages.c
through the _parse_options() function – https://nvd.nist.gov/vuln/detail/CVE-2021-27698
CVE-2020-27357 RIOT-OS 2020.01 contains a buffer overflow vulnerability in /sys/net/gnrc/routing/rpl/gnrc_rpl_control_messages.c – https://nvd.nist.gov/vuln/detail/CVE-2021-27357