Preface: Who uses Xen? Amazon Web Services alone runs ½ million virtualized Xen Project instances according to a recent study and other cloud providers such as Rackspace and hosting companies use the hypervisor at extremely large scale. Xen is a type-1 bare-metal hypervisor.
Background: A Xen host will run a number of virtual machines, VMs, or domains (the terms are synonymous on Xen). One of these is in charge of running the rest of the system, and is known as “domain 0”, or “dom0”.
Any other VM is unprivileged, and are known as a “domU” or “guest”.
A hypercall is based on the same concept as a system call. System calls are used by an application to request services from the OS and provide the interface between the application or process and the OS. Hypercalls work the same way, except the hypervisor is used.
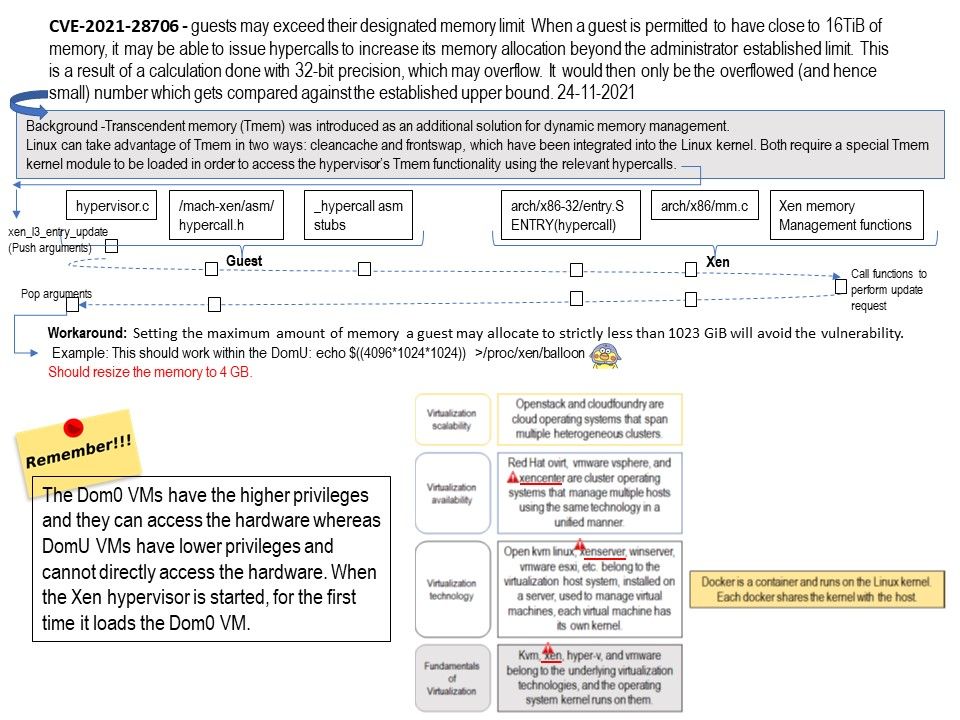
Vulnerability details: (Official description) – When a guest is permitted to have close to 16TiB of memory, it may be able to issue hypercalls to increase its memory allocation beyond the administrator established limit. This is a result of a calculation done with 32-bit precision, which may overflow. It would then only be the overflowed (and hence small) number which gets compared against the established upper bound.
Impact: A guest may be able too allocate unbounded amounts of memory to itself. This may result in a Denial of Service (DoS) affecting the entire host.
Workaround: Setting the maximum amount of memory a guest may allocate to strictly less than 1023 GiB will avoid the vulnerability.
Example: This should work within the DomU:
echo $((4096*1024*1024)) >/proc/xen/balloon
Should resize the memory to 4 GB.
Official article: Please refer to the link – https://xenbits.xenproject.org/xsa/advisory-385.txt