Preface: VMware Flash End of Life and Supportability (78589) – https://kb.vmware.com/s/article/78589
Background: Flex is a powerful, open source application framework that allows you to build mobile applications for iOS, Android, and BlackBerry Tablet OS devices, as well as traditional applications for browsers and desktops using the same programming model, tool, and codebase. From a platform perspective, the vSphere Web Client is based on Apache Flex, which used to be called Adobe Flex. Adobe Flex is a Flash-based platform so it requires Adobe Flash to be installed in order to run.
Ref: Flex uses MXML to define UI layout and other non-visual static aspects, ActionScript to address dynamic aspects and as code-behind, and requires Adobe AIR or Flash Player at runtime to run the application.
Vulnerability details: VMware has released important security updates to address two vulnerabilities in the vSphere Web Client (FLEX/Flash) portion of vCenter Server. CVE-2021-21980 is an arbitrary file read vulnerability in the vSphere Web Client and CVE-2021-22049 contains an SSRF (Server Side Request Forgery) vulnerability in the vSAN Web Client (vSAN UI) plug-in. An attacker with access to port 443 on vCenter Server could gain access to sensitive information or take control of a system.
The vCenter Server 7.x and Cloud Foundation 4.x release lines are not affected by these vulnerabilities as they do not use the vCenter Server vSphere Web Client (FLEX/Flash).
Official announcement: https://www.vmware.com/security/advisories/VMSA-2021-0027.html
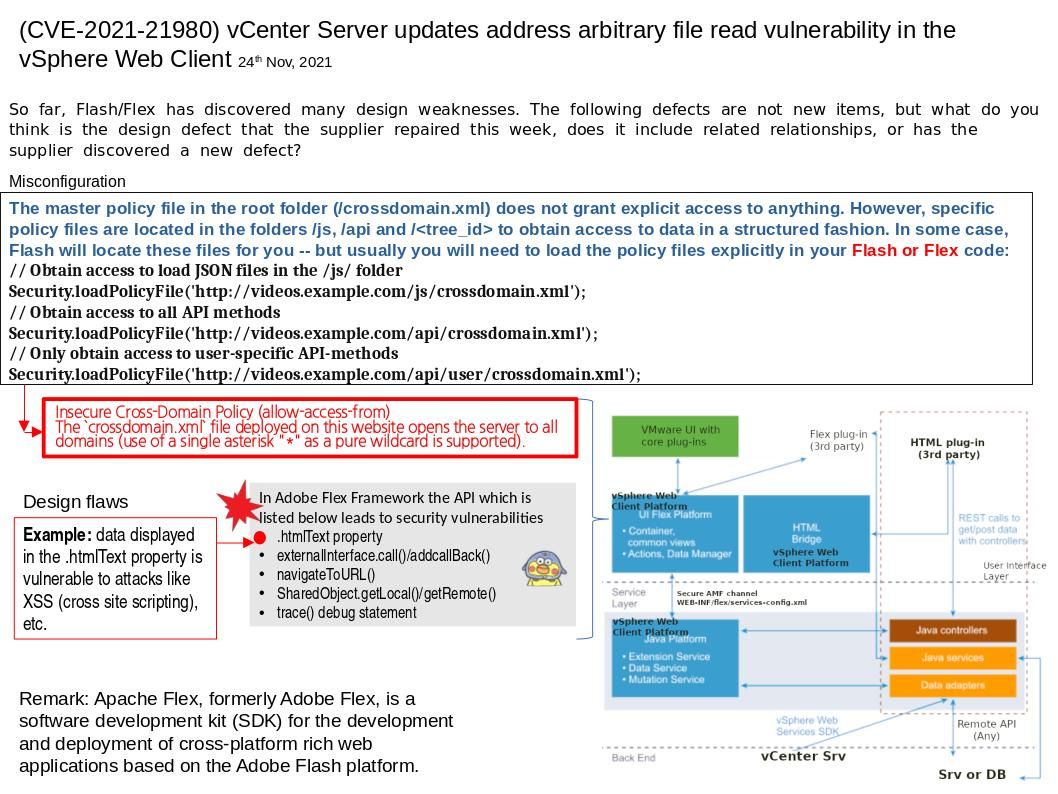
Reminder: So far, Flash/Flex has discovered many design weaknesses. The defects display on attached diagram are not new items, but what do you think is the design defect that the supplier repaired this week, does it include related relationships, or has the supplier discovered a new defect?