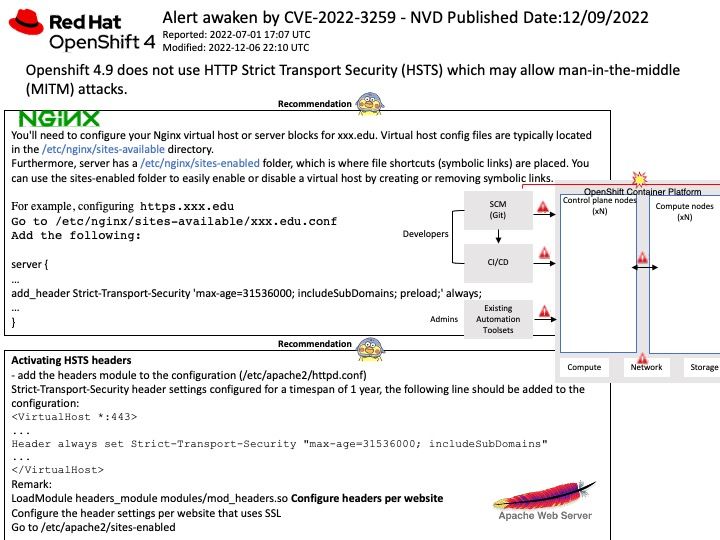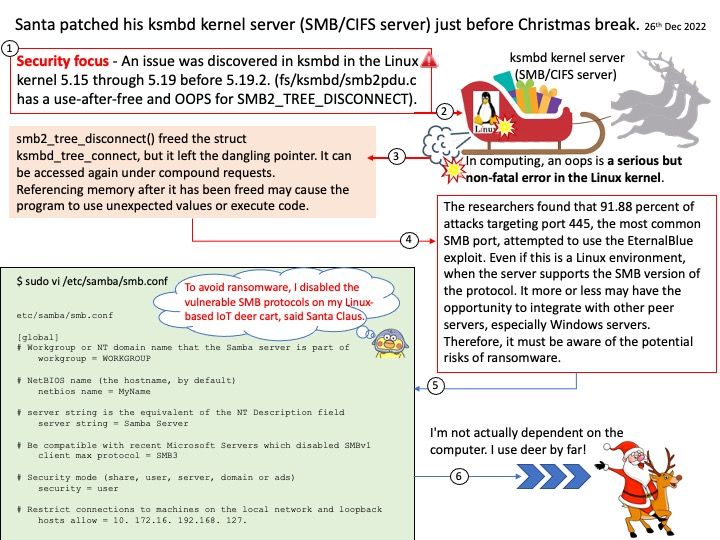
Preface: The researchers found that 91.88 percent of attacks targeting port 445, the most common SMB port, attempted to use the EternalBlue exploit. Even if this is a Linux environment, when the server supports the SMB version of the protocol. It more or less may have the opportunity to integrate with other peer servers, especially Windows servers. Therefore, it must be aware of the potential risks of ransomware.
Background: Common Internet File System (CIFS), an implementation of the Server Message Block (SMB) protocol, is used to share file systems, printers, or serial ports over a network. Notably, CIFS allows sharing files between Linux and Windows platforms regardless of version.
Ref: To mount the CIFS share on Linux for File Viewer, use the command: mount -t cifs // host_name / VIEWER_SHARE -o username= username ,password= password / local_path. CIFS is an unsecure implementation of SMB – its lack of encryption has seen it exploited through malware like NotPetya and the WannaCry ransomware attack, which occurred through a zero-day exploit called EternalBlue.
Vulnerability details: CVE-2022-47939 – An issue was discovered in ksmbd in the Linux kernel before 5.19.2. fs/ksmbd/smb2pdu[.]c has a use-after-free and OOPS for SMB2_TREE_DISCONNECT.
- In computing, an oops is a serious but non-fatal error in the Linux kernel.
Details about this design weakness, see the link – https://git.kernel.org/pub/scm/linux/kernel/git/torvalds/linux.git/commit/?id=cf6531d98190fa2cf92a6d8bbc8af0a4740a223c
Merry Christmas and Happy New Year