Preface: The interconnect component of the opensource application is the opensource software.
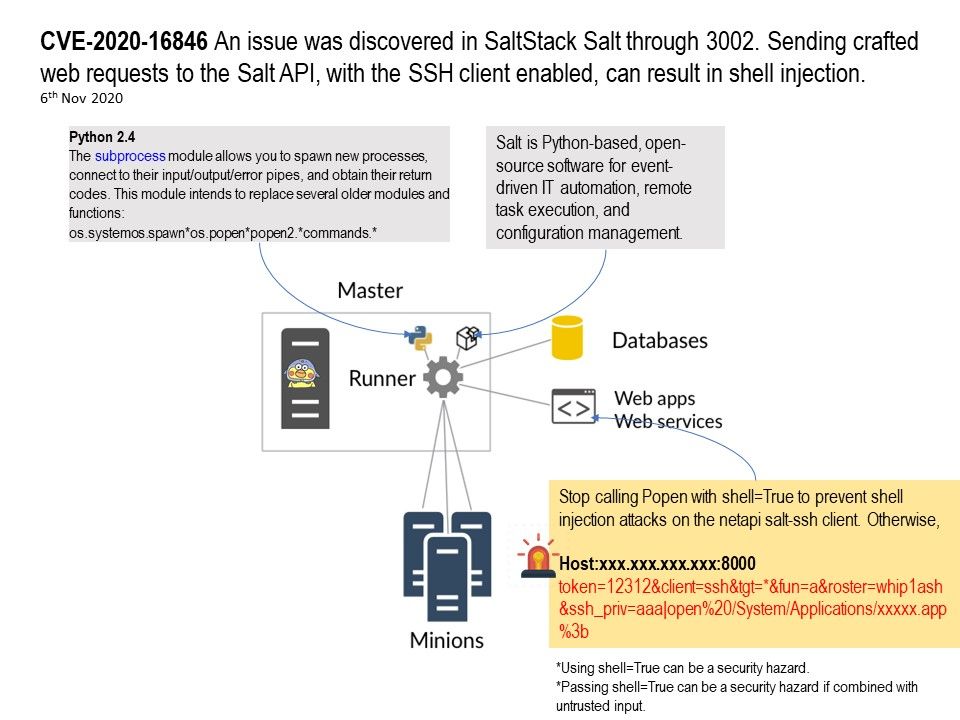
Background: Salt (sometimes referred to as SaltStack) is Python-based, open-source software for event-driven IT automation, remote task execution, and configuration management.
Vulnerability details: An issue was discovered in SaltStack Salt through 3002. Sending crafted web requests to the Salt API, with the SSH client enabled, can result in shell injection. For more details, please refer to attached diagram.
Workaround:
- Stop calling Popen with shell=True to prevent shell injection attacks on the netapi salt-ssh client.
- Split a command string so that it is suitable to pass to Popen without shell=True. This prevents shell injection attacks in the options passed to ssh or some other command.
How to Mitigate: Install the CVE fix and ensure your Salt-API has been restarted.
Announcement by NIST: https://nvd.nist.gov/nvd.cfm?cvename=CVE-2020-16846