Preface: Citrix Hypervisor is based on the Xen Project hypervisor, with extra features and supports provided by Citrix. Citrix Hypervisor 8.2 uses version 4.13. 4 of the Xen hypervisor.
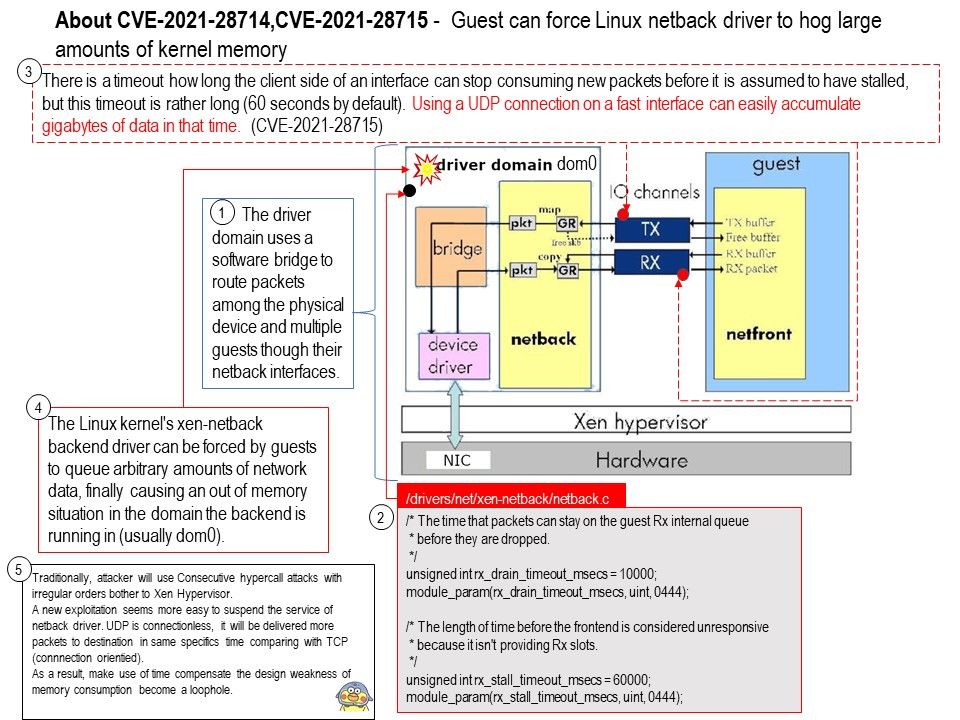
Background: Netfront communicates with a counterpart backend driver called netback in the driver domain, using shared memory I/O channels. The driver domain uses a software bridge to route packets among the physical device and multiple guests though their netback interfaces.
Vulnerability details: Incoming data packets for a guest in the Linux kernel’s netback driver are buffered until the guest is ready to process them. There are some measures taken for avoiding to pile up too much data, but those can be bypassed by the guest:
There is a timeout how long the client side of an interface can stop consuming new packets before it is assumed to have stalled, but this timeout is rather long (60 seconds by default). Using a UDP connection
on a fast interface can easily accumulate gigabytes of data in that time. (CVE-2021-28715)
The timeout could even never trigger if the guest manages to have only
one free slot in its RX queue ring page and the next package would require more than one free slot, which may be the case when using GSO,XDP, or software hashing. (CVE-2021-28714)
Additional: Traditionally, attacker will use Consecutive hypercall attacks with irregular orders bother to Xen Hypervisor.
A new exploitation seems more easy to suspend the service of netback driver. UDP is connectionless, it will be delivered more packets to destination in same specifics time comparing with TCP (connnection orientied). As a result, make use of time compensate the design weakness of memory consumption become a loophole.
Official announcement: https://cve.report/CVE-2021-28715/6270cec3