Preface: Within this week, the impression of VMware products vulnerabilities draw attention with a lot of people. It is because the vulnerabilities was found are high risk rating. But VMware is one of the pillar of virtual machine machine world. Do not worry too much. A good product should have space for improvement.
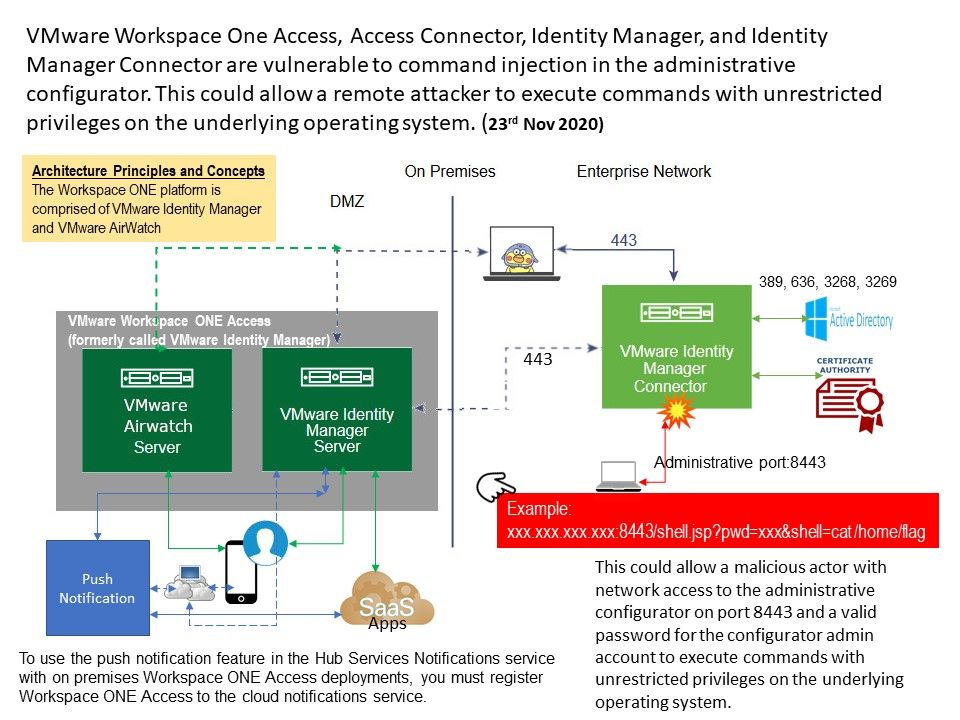
Product background: Workspace ONE Access, (formerly VMware Identity Manager), provides multi-factor authentication, conditional access and single sign-on to SaaS, web and …
Vulnerability details: VMware Workspace One Access, Access Connector, Identity Manager, and Identity Manager Connector are vulnerable to command injection in the administrative configurator. But do not contempt this design fault because attacker require admin credential. However when attacker successful execute this vulnerability. It can compromise all the back end windows domain controller and critical system. It has workaround only provided by vendor currently. The goal of the workarounds do the hardening of web server config file and enforce the access control. For example, it is recommend to use “su” function instead of root. If you have interested of the details. Please refer to diagram.
Official announcement:
VMware – https://kb.vmware.com/s/article/81731
CERT Coordination Center – https://kb.cert.org/vuls/id/724367