NATS Srv wiki – Cloud native messaging system made for developers and operators who want to spend more time doing their work and less
time worrying about how to do messaging.
End user of this product: Mastercard, Baidu, Alibaba Group, VMware, GE, Pivotal, Telia Company, netlify, htc, GE, Zephyr Project, tinder and ERICSSON
Vulnerability details: Some libraries treated tokens signed with the none algorithm as a valid token with a verified signature. The result? Anyone can create their own “signed” tokens with whatever payload they want, allowing arbitrary account access on some systems.
*In systems using HMAC signatures, verificationKey will be the server’s secret signing key
*In systems using an asymmetric algorithm, verificationKey will be the public key against which the token should be verified
Security focus: If a server is expecting a token signed with RSA, but actually receives a token signed with HMAC, it will think the public key is actually an HMAC secret key.
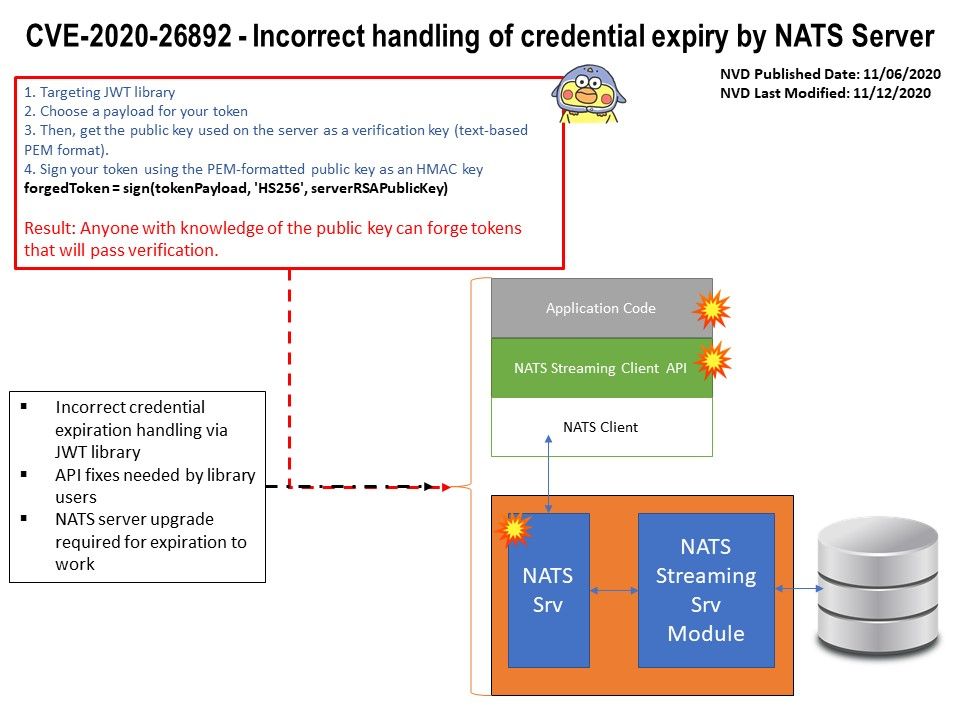
- Targeting JWT library
- Choose a payload for your token
- Then, get the public key used on the server as a verification key (text-based PEM format).
- Sign your token using the PEM-formatted public key as an HMAC key
forgedToken = sign(tokenPayload, ‘HS256’, serverRSAPublicKey)
Result: Anyone with knowledge of the public key can forge tokens that will pass verification.
Reference: https://www.openwall.com/lists/oss-security/2020/11/02/2/2