Preface: Open vSwitch is a production quality, multilayer virtual switch licensed under the open source Apache 2.0 license. It is designed to enable massive network automation through programmatic extension, while still supporting standard management interfaces and protocols (e.g. NetFlow, sFlow, IPFIX, RSPAN, CLI, LACP, 802.1ag). In addition, it is designed to support distribution across multiple physical servers similar to VMware’s vNetwork distributed vswitch or Cisco’s Nexus 1000V.
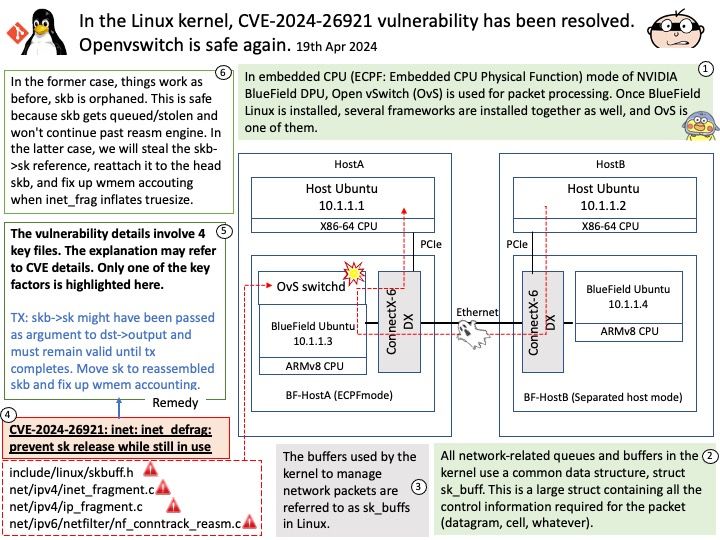
Background: The buffers used by the kernel to manage network packets are referred to as sk_buffs in Linux. The buffers are always allocated as at least two separate components: a fixed size header of type struct sk_buff; and a variable length area large enough to hold all or part of the data of a single packet.
Vulnerability details: The vulnerability details involve 4 key files. The explanation may refer to CVE details. Please refer to the link for details –
https://nvd.nist.gov/vuln/detail/CVE-2024-26921
Security Focus: A relevant old patch about the issue was : 8282f27449bf (“inet: frag: Always orphan skbs inside ip_defrag()”) [..] net/ipv4/ip_output[.]c depends on skb->sk being set, and probably to an inet socket, not an arbitrary one. If we orphan the packet in ipvlan, then downstream things like FQ packet scheduler will not work properly. We need to change ip_defrag() to only use skb_orphan() when really needed, ie whenever frag_list is going to be used.
TX: skb->sk might have been passed as argument to dst->output and must remain valid until tx completes. Move sk to reassembled skb and fix up wmem accounting.