Preface: There are two primary types of buffer overflow vulnerabilities: Stack overflow and Heap overflow.
Product background: The administrative command–line client is a program that runs on a file server, workstation, or mainframe. It is installed as part of the Tivoli Storage Manager server installation process. The administrative client can be accessed remotely. From the administrative client, you can issue any server commands.
Vulnerability details: The PoC shown that you can do the following on the IBM Tivoli Storage Manager. In the “id” field paste the Proof of concept text format file (xxx.txt) and press “ENTER.
Below example is the essential command. According to the below details, it will let you know how to execute above syntax.
Official reference: You can bypass this batch mode double quotation mark restriction for Windows clients by using the back slash () escape character. For example, on the OBJECTS parameter of the DEFINE CLIENT ACTION command, you could enter the string with the \ character preceding the double quotation marks in the command.
dsmadmc-id=admin-password=admin define clientaction test_node domain=test_dom action=restore objects=’\”C[:]\program files\test*\”’
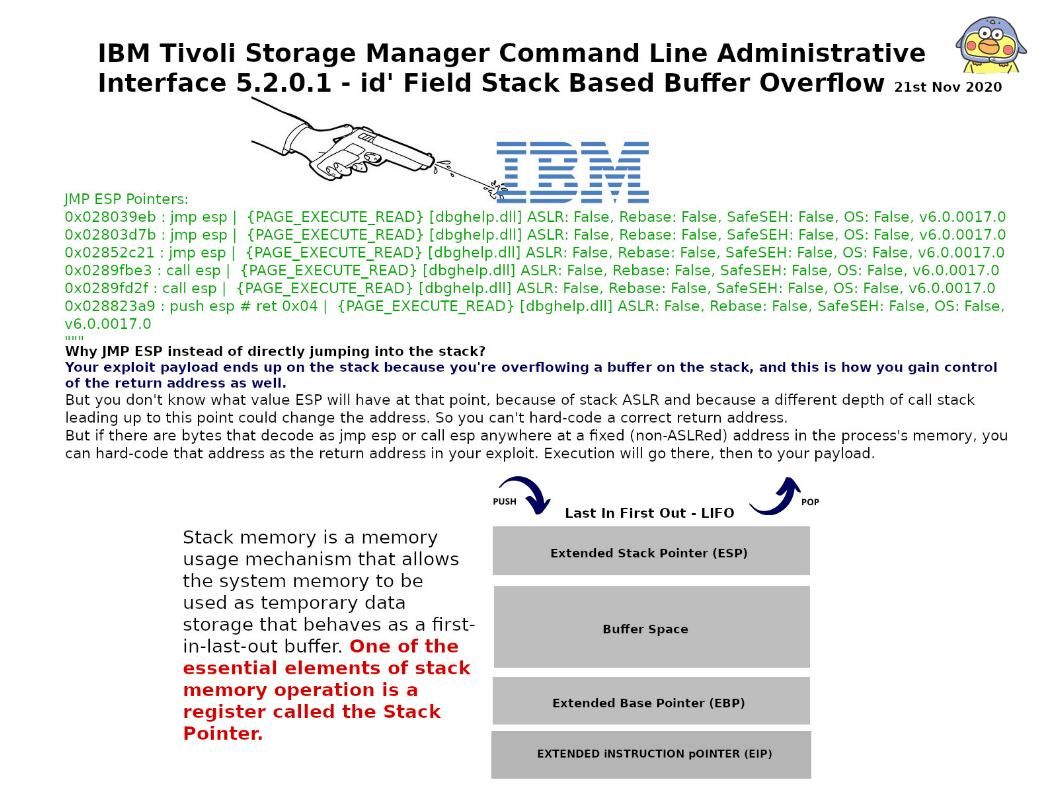
The PoC text file details do not display on our discussion. However I would like to bring your focus to the function which appear on the file. It is the jmp esp feature. The details you can find on the picture.