Preface: Use After Free scenario can occur when “the memory in question is allocated to another pointer validly at some point after it has been freed.
Background: If there is a process named vmware-vmx[.]exe in the process list then there is a virtual machine that is currently powered on. The Virtual Machine Monitor (VMM) process is in charge of managing the virtual machine memory and transfers virtual machine storage and network I/O requests to the VMkernel. All other, non-critical to performance, I/O requests are forwarded by VMM to VMX.
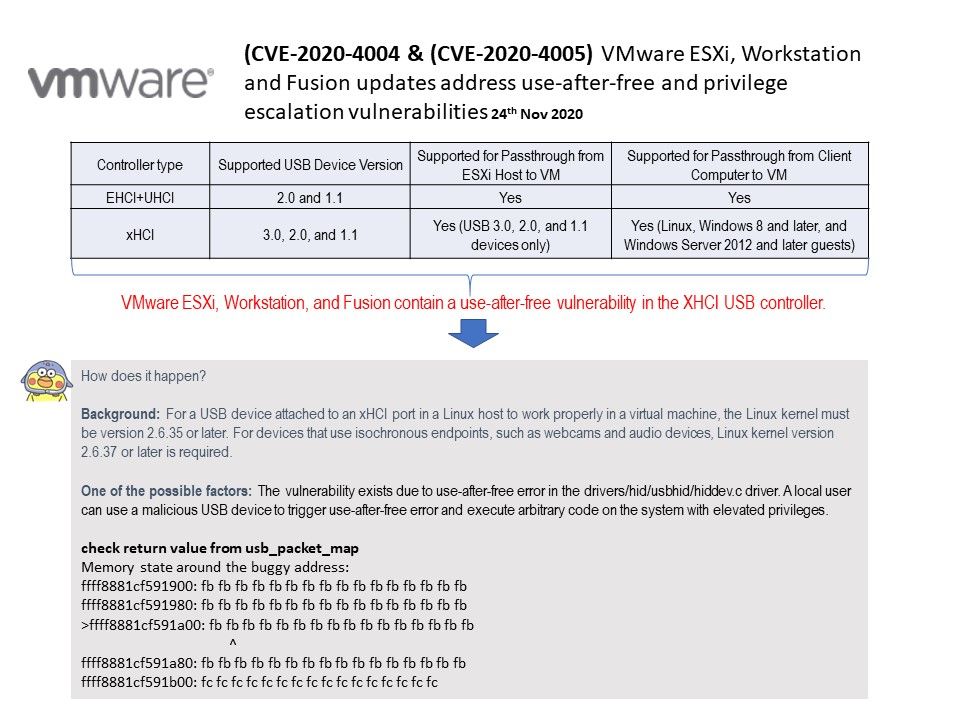
Vulnerability details: Use-after-free vulnerability in XHCI USB controller (CVE-2020-4004) VMware ESXi contains a use-after-free vulnerability in the XHCI USB controller. VMware ESXi contains a privilege-escalation vulnerability (CVE-2020-4005) that exists in the way certain system calls are being managed. A malicious actor with privileges within the VMX process only, may escalate their privileges on the affected system. Successful exploitation of this issue require cooperate with another vulnerability (e.g. CVE-2020-4004). If the attacker successfully exploited two different vulnerabilities. As a result, he can manipulate the entire system, including all VM guest OS.
Official announcement (workarounds): https://www.vmware.com/security/advisories/VMSA-2020-0026.html