Preface: Most SD-WAN suppliers have partnerships with leading cloud platforms, and they use a variety of methods to accelerate traffic coming to and from cloud platforms. But IT pros say, it should look for better security.
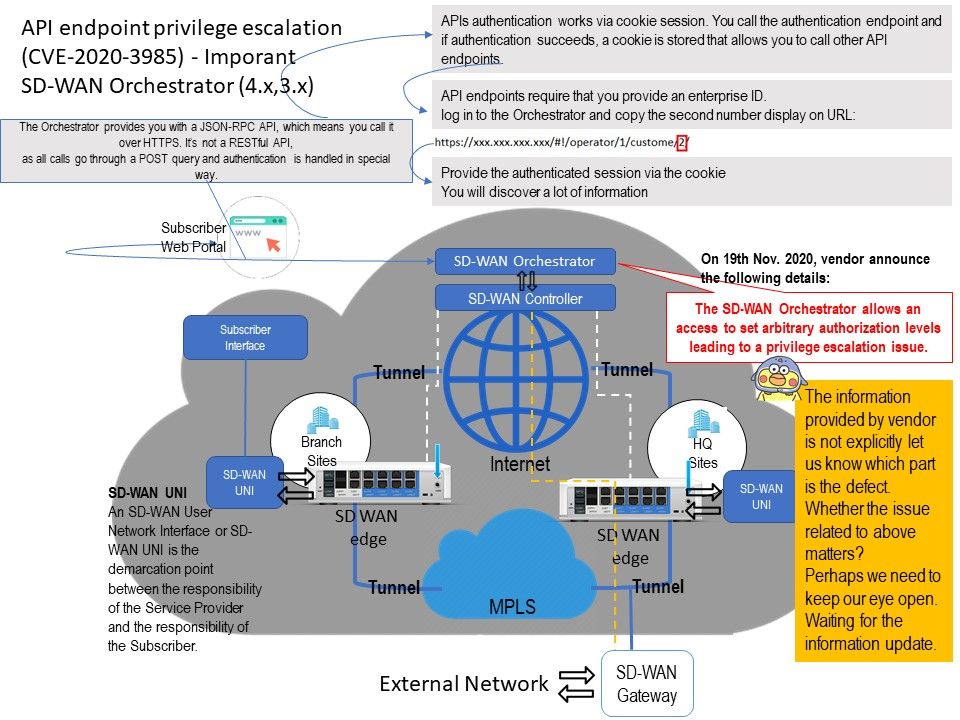
Background: The Orchestrator provides you with a JSON-RPC API, which means you call it over HTTPS. It’s not a RESTful API, as all calls go through a POST query and authentication is handled in a somewhat special way.
Vulnerability details: The SD-WAN Orchestrator allows an access to set arbitrary authorization levels leading to a privilege escalation issue.
Known Attack Vectors: An authenticated SD-WAN Orchestrator user may exploit an application weakness and call a vulnerable API to elevate their privileges.
Observation: According to VMware SD WAN 4.0 release note published on 18th Nov 2020. The Orchestrator API do the enhancement especially role base access control. A various new APIs used in the creation and management of custom roles. For example: role/getEligiblePrivilegesForCustomization – List privileges that eligible for customization for a given role. It is the effective solution to avoid misconfig of user role and access control.
Official announcement: https://www.vmware.com/security/advisories/VMSA-2020-0025.html