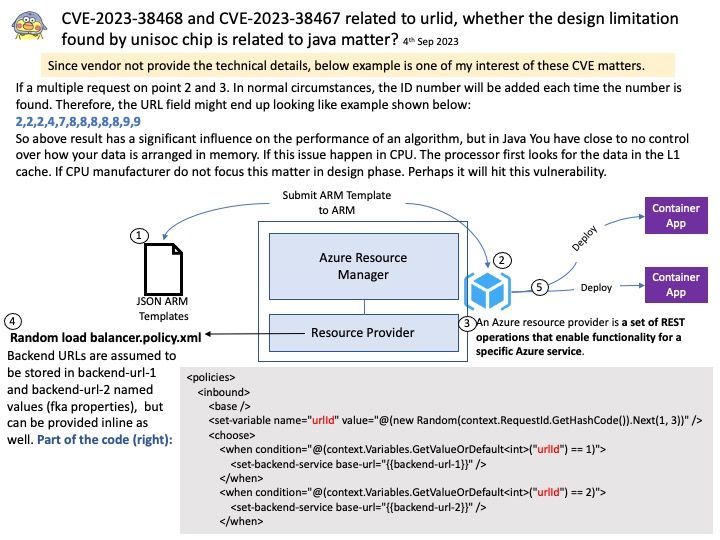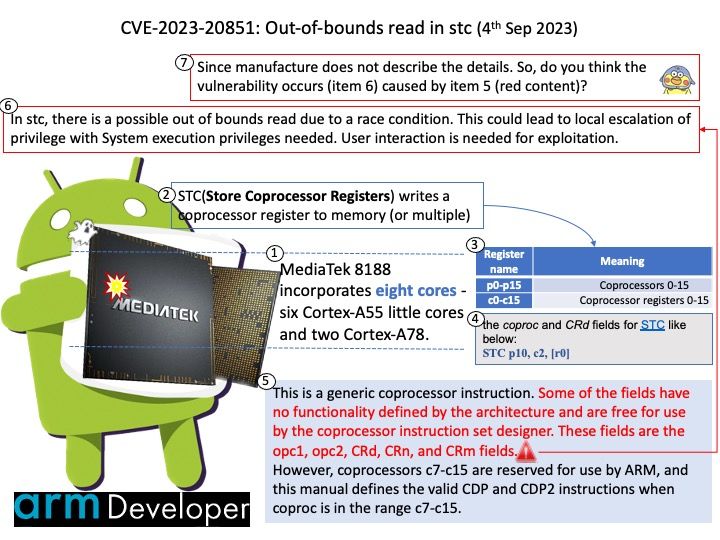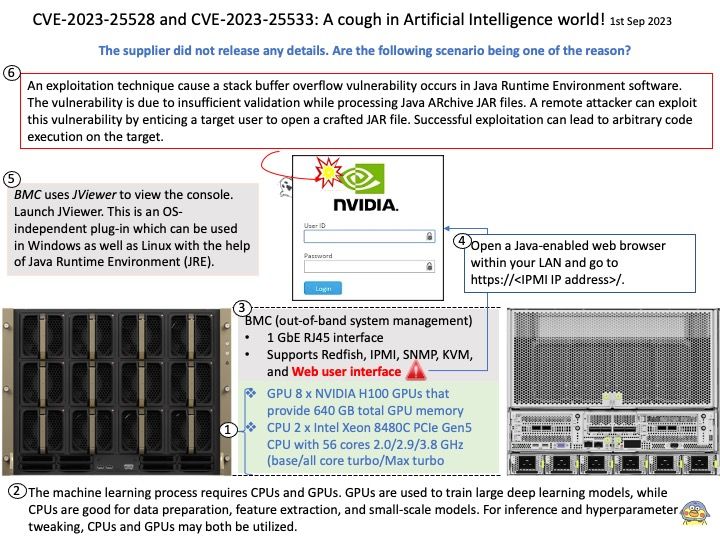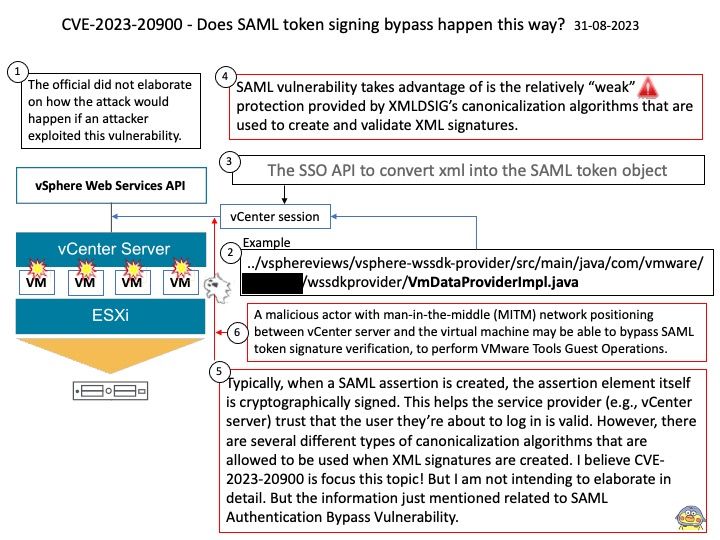
Preface: Technicians tend to focus on zero-day vulnerability status. Makes sense. However, the computer world expands from workstations and intranets into the IoT world. The Internet of Things master put the workstation project into the IoT catalog early on. At the same time, software includes operating system platform and programming language design, and is not limited to Microsoft software product platforms. Therefore, any alleged vulnerability will be exploited by cybercriminals against real situations. Today, my focus in this brief topic is not on the severity of design flaws. The case was discovered in March last year. But there are still status updates today.
Background: The GNU C Library project provides the core libraries for the GNU system and GNU/Linux systems, as well as many other systems that use Linux as the kernel. These libraries provide critical APIs including ISO C11, POSIX.1-2008, BSD, OS-specific APIs and more. These APIs include such foundational facilities as open, read, write, malloc, printf, getaddrinfo, dlopen, pthread_create, crypt, login, exit and more.
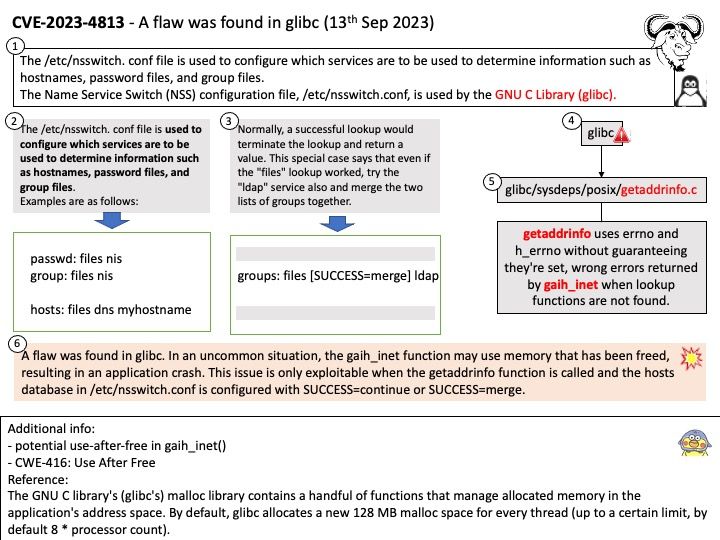
The /etc/nsswitch[.] conf file is used to configure which services are to be used to determine information such as hostnames, password files, and group files.
The Name Service Switch (NSS) configuration file, /etc/nsswitch[.]conf, is used by the GNU C Library.
Vulnerability details: A flaw was found in glibc. In an uncommon situation, the gaih_inet function may use memory that has been freed, resulting in an application crash. This issue is only exploitable when the getaddrinfo function is called and the hosts database in /etc/nsswitch[.]conf is configured with SUCCESS=continue or SUCCESS=merge.
Official announcement: For details, please refer to the link – https://nvd.nist.gov/vuln/detail/CVE-2023-4813