Preface:
A science concept guide human being to hypothesize boldly, to testify rigorously. It looks to me that this concept is principle but I believe that more terms can enrich our technology life. For example, carry the don’t care term during your development and thinking. That is even though it was unsucessful, you will receive knowledge. You will dig out more during this circumstances.
Remark: Since don’t care term also apply to boolean expression. May be you are think that it is a little bit side track, right. But we are in cyber world. In digital logic, a don’t-care term for a function is an input-sequence (a series of bits) for which the function output does not matter.
OK, we go to the subject matter today. How we imagine that Sherlock Holmes do a study on cybercrime. Find out the (malware & ransomware) perpetrator?
Perform investigation
From digital forensic point of view, the investigation will focus on the following objectives:
Capturing a Live RAM dump
Acquiring a Disk Image
Discovering and Analyzing Evidence
Creating Reports
Since I am not going to suggest that we engage a real exercises now. It is not a good idea without preventive control to execute this job. Run in rush without preparation thus contain inherent risk harm your machine and personal data. So we step back take a hot example (wanna cry) see whether can dig out more idea and information.
Observation Point 1 – Languages
Since we are not going to do a forensic investigation. We simply walk through example (wannacry) on language setup. From language setup capabilities (see below), it looks that it cover the languages all around the world.
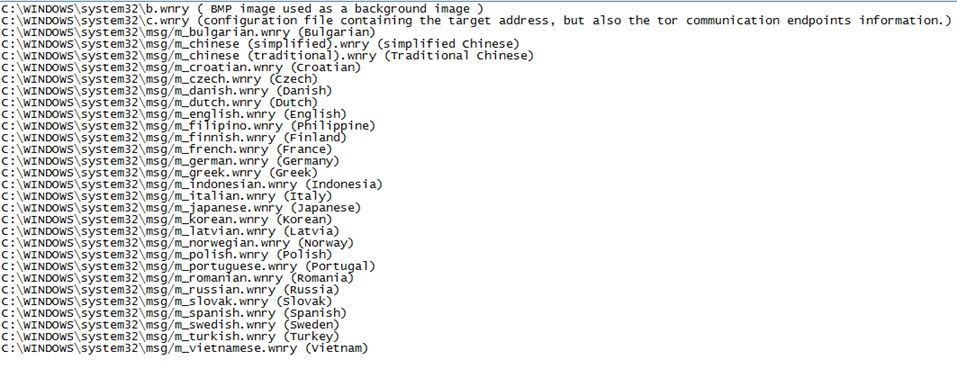
Criminal psychology
From criminal psychology point of view, it looks that the criminal not going to specify a specifics target. A high level point of view that they are looking for money. Fully compatible of language set benefits for their objective.
Observation Point 1.1 – Written language and grammar
From detection point of view, the written language and grammar can provides hints to detective see whether to dig out hints. This hints may speculate for the direction of the detection. For example: the fundamental limitation of mother tongue translation to other native language.
Weakness of this detection method:
Such detection might fool by criminal group and intend to interfere the direction.
Observation Point 2 – Malware written technique:
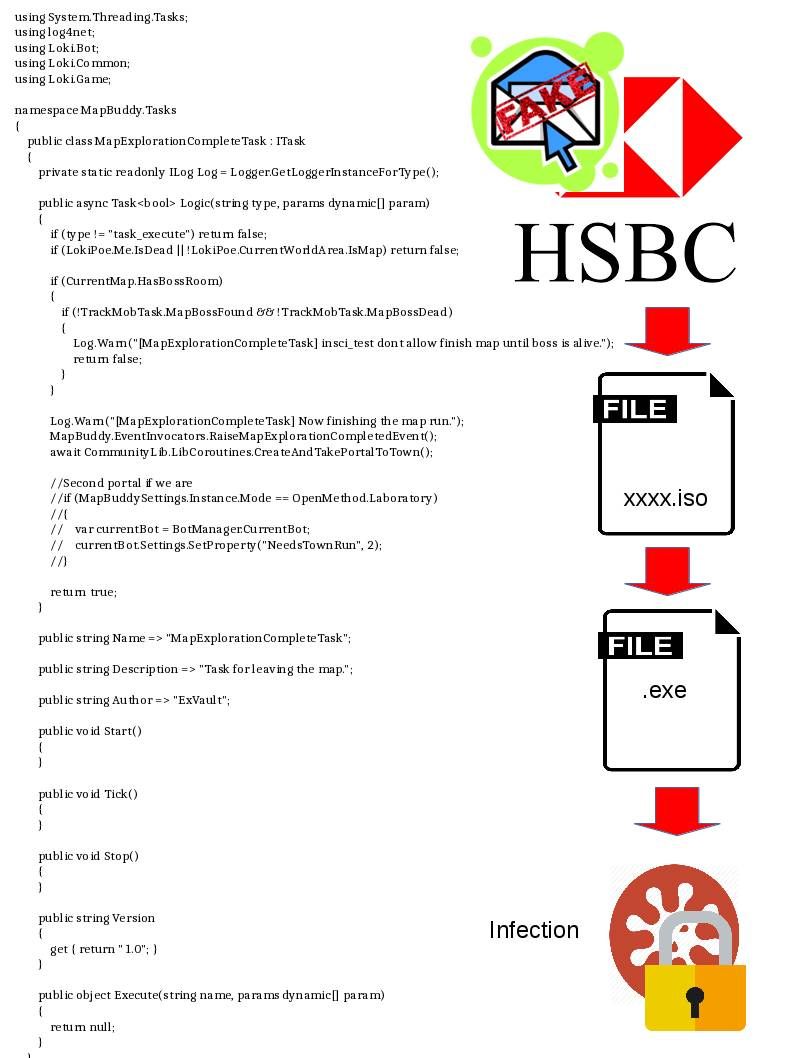
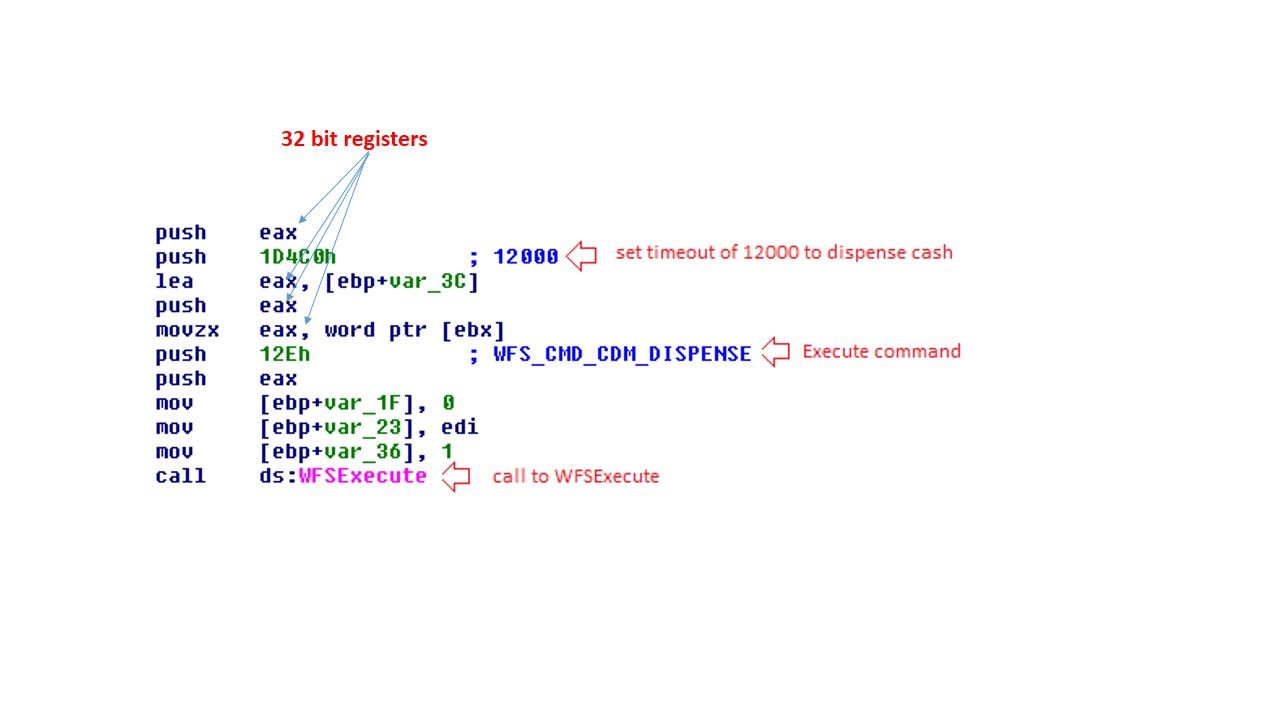
Some of the times, the written programming style and infection technique might provides hints to detective to the right direction. But a lot of time will interfere the direction of investigation. For example: Wannacry relies on NSA (DoublePulsar) back door software agent or SMB v1 vulnerability (see below picture) to execute the job task. From normal circumstance’s, bad guy will implant a backdoor to victim machine to fulfill the infiltration job task. Unfortunately the backdoor software (DoublePulsar) was given from NSA of their global surveillance program. Wannacry is a ransome software. In the sense that NSA might not be the perpetrator. As a result it interrupt the trace process. The investigator can’t follow the hints to predict who is the appropriate party to do this criminal job.

Observation Point 3 – Down to the grove, execute forensic investigation
Since above observation items might contain fundamental weakness. As a matter of fact, those items of evidences might become a relevant evidence. The fundamental theory by law of relevant evidence interpret that relevant part of evidence is logically connected to the fact it is intended to establish” (Blackwell, 2004). However the investigator or detective most likely will prefer to execute forensic investigation to receive the digital and demonstrative evidence.
Technical limitation of the forensic investigation
We know that ransomware infection crisis like Wannacry victims suspended Health care services in United Kingdom. The major effect which harm to whole hospital services over there! Since healthcare services maintains compliance standard. It is possible to let the forensic investigator do the investigation (see below step).
1. Capturing a Live RAM dump
2. Acquiring a Disk Image
3. Discovering and Analyzing Evidence
4. Creating Report
However a technical limitation has been found on traditional digital forensic investigation criteria.
Few evidences will be lost once victim power off their machine.
Victim which have technical know how will erase some evidence
Audit log disable by default
Advanced technology enhance the limitation on their investigation algorithm
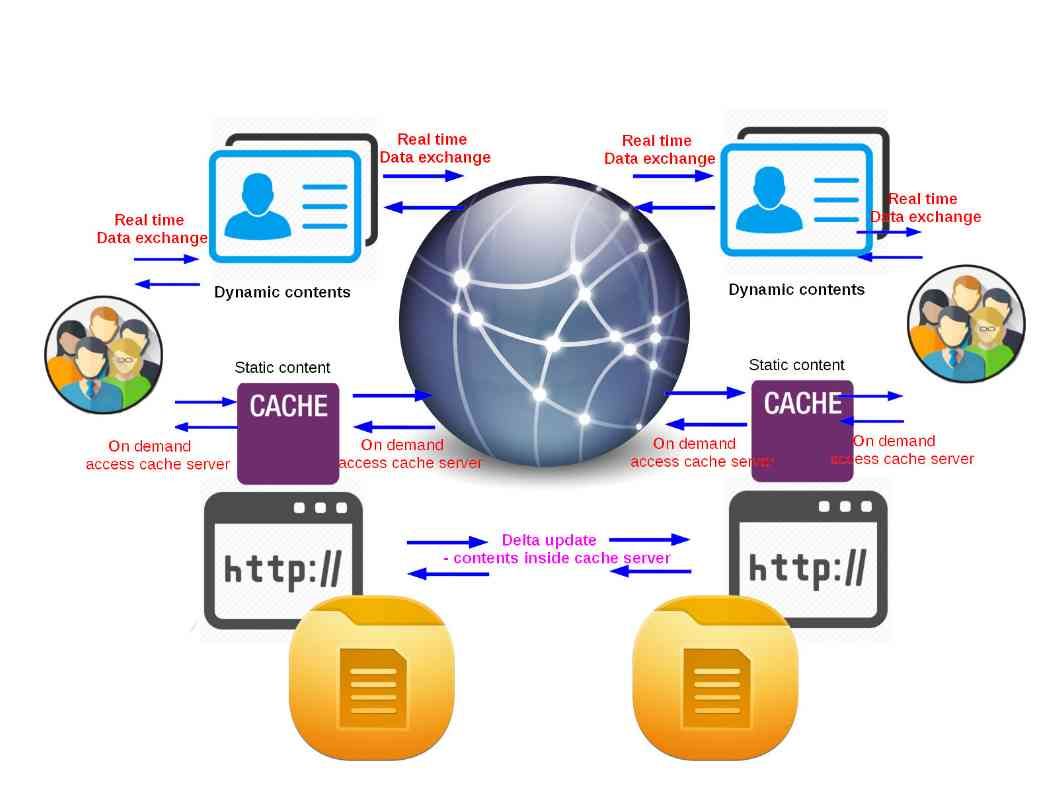
Technology company note with alert of the technical weakness during forensics investigation. A preventive mechanism was build to avoid lost of critical data after system power off. The enhancement is that an software agent will be installed on the workstations. The software agent will collect the delta (data change) and then forward to the centralized repository in real time.

As we know, no design and solution is prefect. For this enhancement it is prefect to implement to enterprise or corporate environment. For workstation for personal usage it is difficult to implement. A drawback alert to the detective or government enforcement team that there is a technical limitation on personal devices (personal computer workstations, mobile computing devices and IoT devices).
Multi-angle detection architecture
Readers, if you can read this down to here, we might know the mentioned investigation mechanism are able to collect the following details.
(1) Memory dump, (2) disk image, (3) malware activities finger print, (4) virus and malware types, (5) C&C server public IP address and (6) malware dropper file.
Even through we received above informations on hand. However, it is hard to provide a comprehensive of evidence proof who is the perpetrator! For example, it is hard to collect the information details once workstation compromised by wannacry. As a matter of fact the whole disk has been encrypted. So, what’s the next step when investigator face this problem.
Refer to below picture, you might aware that point C (C&C server) and point D (victim compromised web server) are located in different regions. They are not in single operation. Even though Forensics investigator are able to decrypted the hard disk or collect the activities log from their SIEM device. The trace result sometimes mislead the location of the area. It is hard to provides a clear picture. In order to identify the root sources. A detection terminology so called multi angle detection algorithm will be assist investigator in such circumstances.
The concept idea is that investigator will summarize the following entities.
1. Total no. of C&C servers and their IP addresses
2. Total no. of Victims (compromised web server) and their IP address
3. Categorized the IP address and highlight the IP address region
Remark: As we know, hacker will relies on Tor network to hide himself in effective manner. Since it is hard to know their location status once their connectivities get inside to the onion network (Tor network).
4. Execute forensic investigation to the compromised server (Point D)
5. Find out the C&C server connectivity (Point C)
6. Sometimes law enforcement team not going to let hacker know they has been traced. The job might run on ISP side (Point B). For instance, they will lock down the appropriate tor certificate and filter the certificate Issuer and Subject ID patterns.
7. Since two important elements (tor cert and C&C server public IP address) are known. It is more easy to do the following to find out the attacker source IP address:
a. Define correlation rule to find out the source IP address of the attacker.
b. Apply Google analytic methodology to figure out the attacker IP address.
8. The final action is activate the local police force to arrest the hacker.

Summary:
Regarding to above description it looks that it is not easy to lock down the hackers actual location. Heard that some security expert relies on English written skill or C&C server to predict the attacker source IP address. From technical point of view, it might contained distortion.